Data Privacy Laws Should Protect Users, Not Governments


- What are software backdoors?
- How governments and other parties can exploit them
- Software backdoor risks on businesses
Speaking at this year’s CES tech trade show, Jane Horvath, Apple’s senior director for global privacy, defended the company’s stance on encryption. She joined an all-female panel to discuss the state of consumer privacy. Apple repeatedly rejects inquiries by state agencies to unlock criminal suspects’ devices, stressing that it strongly opposes software backdoors.
And the company is not alone in its stand for protecting user privacy. IT professionals all around the world share Apple’s concerns, especially those who are members of ISACA, an international association focused on IT governance.
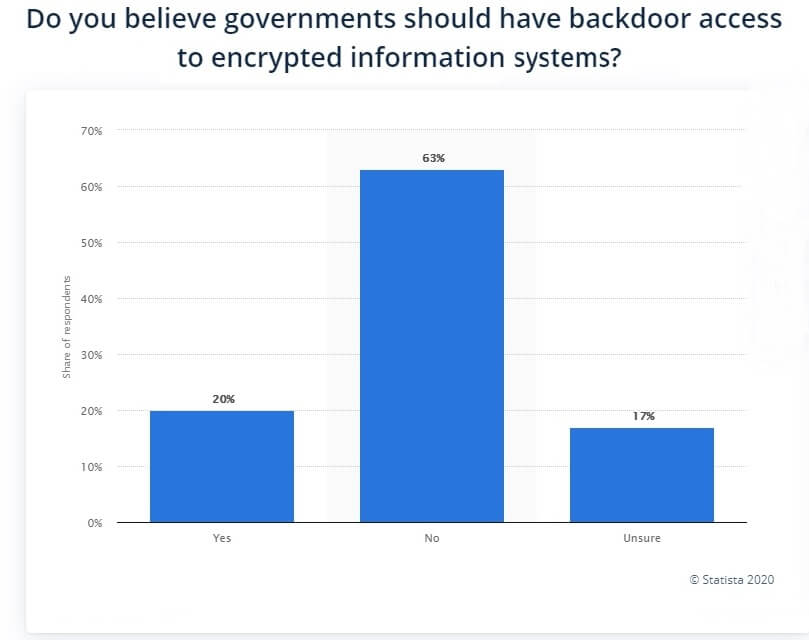
According to Statista, only 20% of IT professionals believe that governments should have backdoor access to encrypted information systems. The 2016 study also showed that 63% were against government backdoors to data, while 17% were unsure.

Any IT security specialist knows that backdoor access for one party means anyone can exploit the loophole and gain entry. In other words, it’s not just the authorities who can put their hands on your data, but also anyone with backdoor clearance.
Fundamental Problems With Backdoors for Governments
International software companies are always under pressure to provide authorities with user data access. Even the most privacy-friendly governments have been involved in spying and surveillance that target citizens and residents. They need to do so sometimes for the sake of national security.
The thing is, if you create a software backdoor for one government, others will immediately want the same treatment. And the more entities with backdoor access, the higher the chance of a login credential leak to a malicious party.
“Who controls the controller” is an old saying that dates back to Roman times. It highlights a fundamental problem in the field of IT security and data protection. You see, a lot of intelligence agencies abuse their powers for malicious purposes and even for profit. Furthermore, no government can guarantee that only a handful of personnel will use software backdoors. Anyone with clearance can view your data, and some of them might exploit that privilege.
An alarming number of people around the world fear for their privacy. They do not believe most Internet companies really care or have respect for their private data. That means that people also don’t trust their governments, as they have failed to adopt effective regulations that force companies to obey the law.

The truth is, we cannot afford to sacrifice our privacy rights for the sake of better crime prevention. History tells us that surveillance has never prevented crime and will not do so anytime soon. But the right to maintain our online privacy has always been a fundamental individual right.
Businesses and Backdoor Risks
Software users are not only individuals but also corporations. Millions of businesses across the world are using encrypted software systems to create, store, and exchange data records. That includes sensitive data about financial transactions, company reports, and customer information. And these business-critical details are stored and managed using different software applications by various vendors.
Moreover, large multinational corporations experience daily hacking attempts for such data. In the past few years, the number of attacks on Small and Medium Enterprises (SMEs) substantially grew. And now, even local businesses are no longer immune to cyberattacks.
However, if a business takes its cyber-security protection seriously, there are many ways and techniques to block most hacking attempts and keep essential data safe. But how can you fight a software backdoor if you do not know it even exists? How do you find that someone has managed to compromise your business systems without leaving a trace?
Backdoors are more dangerous than any Trojan virus or ransomware. It gives cybercriminals direct access to your system without asking for authorization and bypasses any defense system you have in place. As a result, perpetrators will have access to confidential information like contacts, financials, and tender details.
There’s a good chance that someone with ill intentions will exploit backdoors. A lot of corporations would pay top dollars to take a peek at their competitors’ business systems. And the same thing applies to government agencies and their representatives, who have absolute power over business and user data.
Privacy Protection from Backdoors – Final Words
Forcing the software industry to create backdoors for law enforcement authorities contradicts human rights to privacy and security. Data encryption was designed to protect, store, and exchange information in private, without worrying about snoopy eyes.
Therefore, software backdoors will only make things worse in an already messy cybersecurity landscape. It will also endanger businesses that have open-source apps, which can be used to scan backdoors and other vulnerabilities. As a result, large software companies like Apple, IBM, and Microsoft oppose the implementation of backdoors for personal or business use.



