Report: Ransomware Payments Reached All-Time High in 2021


As ransomware gangs intensify their cyberattacks on businesses worldwide, payments in exchange for the data have also increased. According to a new report, the money victims paid to hackers hit a new high on average in 2021. Likewise, ransom demands have more than doubled, with threat actors becoming bolder and significantly affecting their targets.
The numbers come from Palo Alto Networks’ Unit 42, which published its 2022 Ransomware Threat Report Highlights on March 24. The cybersecurity experts analyzed every ransomware incident response case they took part in. And they discovered that the average payment rose by nearly 80%.
Average Ransomware Payment Reaches $541,000
Ransomware is when hackers infiltrate IT systems, then hijack and encrypt critical company data. The information could include classified files or user credentials like usernames and passwords. After locking the victim out of their own systems, the attackers demand a ransom – usually in crypto to maintain anonymity – in exchange for the data. Otherwise, they sell it or leak it to other groups.
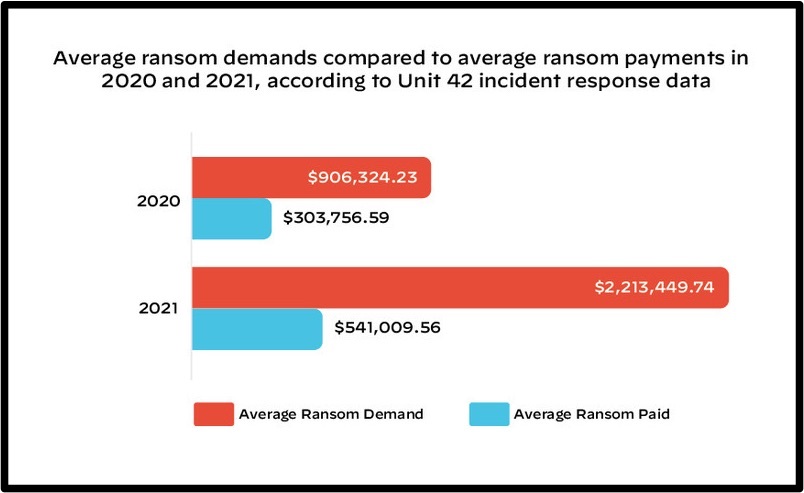
And with ransomware attacks becoming more and more sophisticated and hackers using clever tactics, victims are caving to their demands. As a result, ransom money has notably increased. According to a recent Palo Alto Networks report, ransomware payments jumped from just over $300,000 in 2020 to $541,000 in 2021 on average. That’s a staggering 78% increase.
Ransom demands also witnessed a sharp hike, registering more than double figures from the previous year. In fact, the report shows that the average sum that extortionists requested was $900,000 in 2020 but hit $2.2 million in 2021. Naturally, ransomware payments are usually much less than hackers’ initial demands. But that depends on the victim and the importance of the stolen data.

For example, researchers highlighted one incident when Blackcat hackers demanded $9 million to release encrypted data and received $8.5 million. Meanwhile, in a different case, Suncrypt cybercriminals requested $12 million but only received $200,000.
Most Companies Choose to Pay
Whether victims pay the total amount or just a fraction of the ransom indicates that crime pays. And for ransomware gangs, that’s more than enough motivation to keep launching their attacks. As long as companies keep paying, cyber threats will keep on coming. All it takes is one target to give in to their demands, and they could become millionaires.
Cybersecurity agencies from Australia, the US, and the UK released a joint advisory last month warning against the rise of ransomware. They said that threat actors would continue their cyberwars after seeing organizations pay up. Unit 42 suggests that 58% of ransomware-hit organizations opt to pay ransoms, despite warnings not to do so. However, it doesn’t always solve their problems as, in some cases, they end up paying more than once.
Hackers are now using double extortion tactics – copying the stolen data before encrypting it, then threatening to publish it. That way, they demand a ransom for the decryption key and another for not disclosing the information.
Ryan Olson, vice president of threat intelligence at Unit 42, revealed that hackers discovered more ways to extort their victims, adding that these tactics increased in the past year.
In 2021, ransomware gangs took these tactics to a new level, popularizing multi-extortion techniques designed to heighten the cost and immediacy of the threat.
Ryan Olson, Vice President of threat intelligence at Unit 42



