Kyocera Ransomware Attack – LockBit Back at It


In the cybercrime underworld, various threat actors roam the internet searching for perfect candidates to call victims. Each group has its own technique and capabilities, and we can say that LockBit is one of the most dangerous ones out there. Aside from previous attacks, LockBit has shown to be quite capable with the new Kyocera ransomware incident.
Kyocera AVX Components Corporation (KAVX), a subsidiary of the Japanese semiconductor giant Kyocera, is a huge US manufacturer with a yearly revenue of nearly 1.5 billion dollars.
If a company like that is breached, rest assured that the number of impacted individuals would be huge. And that’s exactly the case in this particular incident. What do we know about it? Find out below.
LockBit Strikes, Kyocera Discloses
As we mentioned, LockBit is one of the most dangerous ransomware groups out there. It has been causing a lot of problems lately among big companies around the world.
In fact, a while ago, the group managed to infiltrate Pendragon Group – a big company with more than 200 car dealerships in the U.K.
No one is safe when it comes to cybercrime. If it’s a company of value to them, it’s getting targeted. Even Pizza Hut fell victim a couple of months ago.
Now, LockBit has set its eyes on Kyocera and successfully breached its systems. KAVX discovered the intrusion on October 10, 2023, and according to the breach notification, the attack occurred between February 16th and March 30th, 2023.
“On March 30, 2023, KAVX experienced a cybersecurity incident affecting servers located in Greenville and Myrtle Beach, South Carolina, USA, which resulted in the encryption of a limited number of systems and temporary disruption of certain services.
KAVX later discovered that the data contained on the impacted servers included personal information of individuals globally.”
Normally, a data breach targets information like names, email addresses, and credit card information. This particular attack exposed full names and Social Security Numbers (SSNs).
According to the company, there might possibly be more details out in the open, but it decided to censor that section in the notice.
The company did mention that no threat actors have actually abused the data, but customers should look out for identity theft and fraud practices – users should remain vigilant.
But how did everyone know that LockBit was behind the attack? Well, it didn’t take long for the group itself to claim it, as it added the firm to its data leak site.
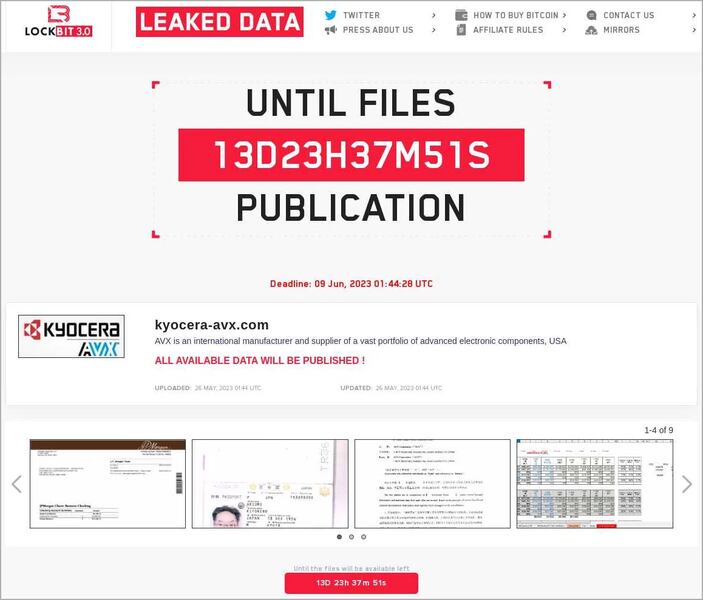

The hackers gave KAVX till June 9th, 2023, to settle the payment. We don’t know what occurred later on, but what we know for sure is that your data is out in the open. Be careful.
LockBit Strikes Again – An Old Breach Resurfaces
The leaked data is very sensitive. In fact, if abused, it can lead to the exposure of proprietary designs and so much more.
LockBit has been around for quite some time now, terrorizing companies all over the world. What you can do is remain vigilant when it comes to what you receive via email or text message.
This might be a continuation of the attack by others since your data is now exposed. Stay safe.



