The 23andMe Breach – Credential Stuffing at Its Best


Threat actors have been targeting major organizations for quite some time now, using different methods to infiltrate their systems. Top names such as Better Outcomes Registry & Network (BORN) and Pizza Hut have recently fallen victim to such attacks. And now, 23andMe joins the latter with a breach caused by credential stuffing.
This particular technique leverages already-compromised user credentials to breach into a system, and the malicious group behind the attack utilized these accounts to infiltrate 23andMe.
Now, the US-based biotechnology and genomics firm’s data has been uploaded on hacking forums for anyone to purchase it. What is credential stuffing? What data is in question? We’ve discussed everything below.
23andMe Breached – Customer Data Up for Grabs
As we mentioned, when it comes to cybercrime, the methods and techniques vary. Unfortunately, the end result is always the same – a breach where thousands/millions are affected.
Threat actors will stop at nothing to infiltrate a target’s system if it’s deemed beneficial to their needs. That’s why attacks have been occurring more frequently for the past few months.
Whether it’s phishing emails, zero-day exploitations, or using fake apps, cybercriminals will always find a way to ensure higher success rates.
In this particular attack, credential stuffing was the used technique. What is it? This method includes utilizing previously compromised user credentials.
The threat actors pair usernames and passwords to a botnet, which then uses them on different websites and services.
You have no idea how successful this attack can be, as most individuals reuse the same username/password combination across multiple sites.
Apparently, this is the case with 23andME, which confirmed the breach a couple of days ago.
“We were made aware that certain 23andMe customer profile information was compiled through access to individual 23andMe.com accounts.
We do not have any indication at this time that there has been a data security incident within our systems.
Rather, the preliminary results of this investigation suggest that the login credentials used in these access attempts may have been gathered by a threat actor from data leaked during incidents involving other online platforms where users have recycled login credentials.”
Source: Bleeping Computer
The problem here is that the threat actors behind the attack posted the stolen data on hacking forums.
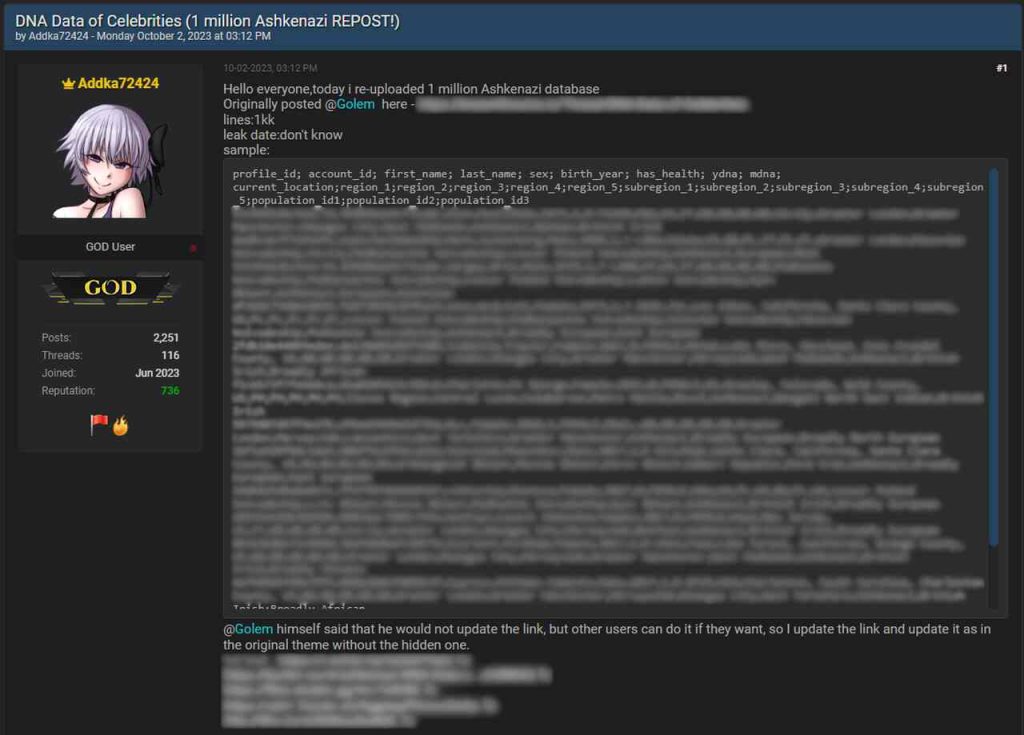

Not only that, but they’re all for sale ($1-$10 per 23andMe account). Of course, that depends on how many accounts a buyer wants to purchase.
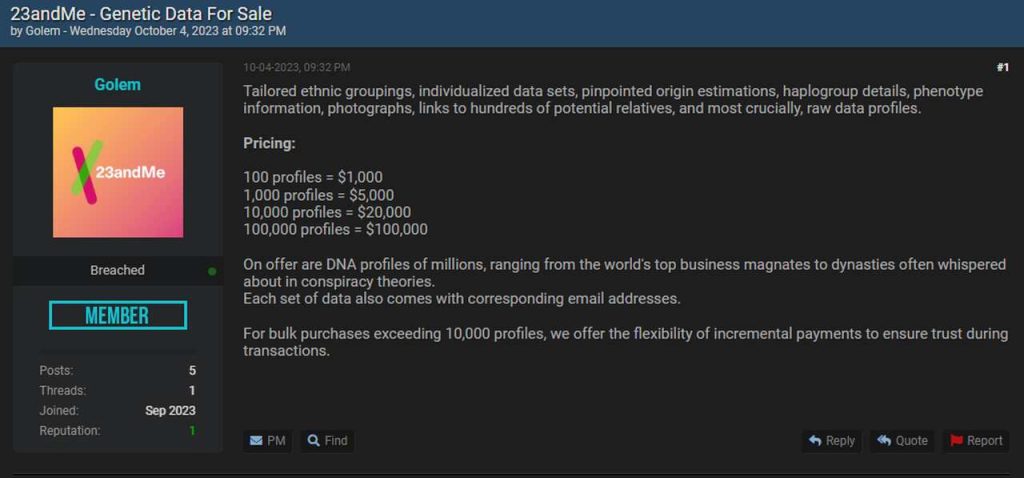

According to Bleeping Computer, the sensitive information includes full names, geographical location, usernames, profile photos, sex, date of birth, and genetic ancestry results.
Anyone who thinks that their data was compromised should remain vigilant when handling email addresses. Never click on a shady link; it could be phishing.
Another Day, Another Breach
23andMe is a reputable company in the US and has a lot of customers. This indicates that a breach within its systems can have major consequences.
The company’s platform offers two-factor authentication, which we urge everyone to utilize. You never know how the threat actors will use your email in the future. Stay Safe.



