A New Phishing Attack – Out with Twilio, In with Cloudflare


When it comes to hacking, being consistent with the attack may result in high success rates. Unfortunately, recent attacks show exactly that. The hackers behind Twilio’s major data breach have resurfaced again with the same scheme but targetting none other than web infrastructure company Cloudflare.
These hackers are very persistent as this would be their second attack in a short period of time. The campaign follows the same criterion where phishing messages are sent to employees.
In the end, the threat actors are after the users’ personal information, which is practically what every phishing attack is about. But we must ask: Was this phishing attempt successful? Did the attackers get anything out of it as they did with Twilio? The answer is in the following article.
Cloudflare Phishing Attack – Another Campaign, Same SMS
Targetting big companies is a common practice nowadays among cyber criminals. And when it comes to phishing, using these companies’ names allows them to easily trick the victims.
A couple of days ago, Twilio employees received a phishing text with a link that takes them to a fake login page. The attackers used the “Sense of urgency” to lure them in and prompt them to enter their credentials so they can harvest them.
Now, the exact same attack is targeting Cloudflare employees. It all starts with an SMS stating that their schedule has been updated. Around 76 employees and their family members received such texts. The following image showcases the smishing (SMS Phishing) attempt:
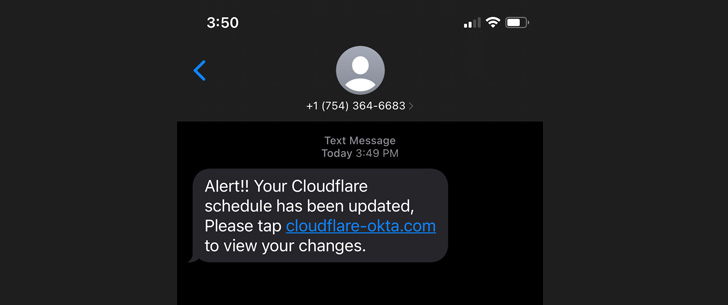

As seen in the image, the text messages include a legitimate but, of course, fake domain containing the keywords “Cloudflare” and “Okta,” which can easily deceive the employees.
According to the company, three of its employees fell for the trick, but unlike Twilio, Cloudflare is well known for its security measures. To sum it up, the attackers failed in the end.
The company uses FIDO2-compliant physical security keys – these are required to access its applications. In other words, this security technology was able to prevent this breach. According to Cloudflare:
“Since the hard keys are tied to users and implement origin binding, even a sophisticated, real-time phishing operation like this cannot gather the information necessary to log in to any of our systems.
While the attacker attempted to log in to our systems with the compromised username and password credentials, they could not get past the hard key requirement.”
If the attacker managed to get past these security measures, who knows what damage it could’ve caused?
Aside from the credentials, the phishing page can automatically download AnyDesk’s remote access software. If this takes root, the threat actor can take full control of the victim’s system.
Cloudflare’s Phishing Attack – Good Effort, Epic Fail
Twilio suffered the same breach, but it didn’t have the means to fend it off. Cloudflare, on the other hand, has all the security measures to protect its systems from such attacks.
The company is working with DigitalOcean to shut down the attacker’s server. Also, it stated that it has reset its impacted employees’ credentials to prevent any further infiltrations. We’re referring to logins using residential proxies and unknown VPNs.



