Discord’s New Phishing Campaign – Babadeda Hits Hard


Discord just doesn’t seem to get a break from phishing attacks. Not long ago, the platform was hit with Free Nitro Steam Scam.
And now, a new campaign is using the Babadeda crypter to hide malware and target Discord’s crypto, NFT, and DeFi communities.
It all starts with a Discord message that redirects you to a supposedly harmless website. Finally, you end up installing Babadeda, which starts distributing remote access trojans (RAT).
With a very low AV detection rate, the malware is a force to be reckoned with. But how exactly is it doing this? We’ve covered everything below.
Cryptocurrency Jeopardized – BabaDeda Hits Hard
Cryptocurrency has become very popular with time. In fact, the cryptocurrency market is now worth more than $2.5 trillion, which, unfortunately, makes it an important target.
Discord has just recovered from a phishing campaign to encounter a new one. This time around, the attackers are using the Babadeda crypter (Russian for Grandma-Grandpa), which can easily bypass signature-based antivirus solutions.
When it comes to groups related to cryptocurrency on Discord, anyone can get it. It’s there for the public to access. This comes in handy to the attackers as they can freely send private messages to other users within a channel.
The sophisticated campaign exclusively targets the Crypto, NFT, and DeFi communities, where the attackers send a private message inviting the users in the community to download a related application that would provide additional benefits and features.
Apparently, since the attackers created a Discord bot account on the official company’s Discord channel, they were able to successfully disguise themselves as the channel’s official account.
It All Starts with a Message
One of the phishing attempts came in the form of “Mines of Dalarna,” – a PC game built on the blockchain.
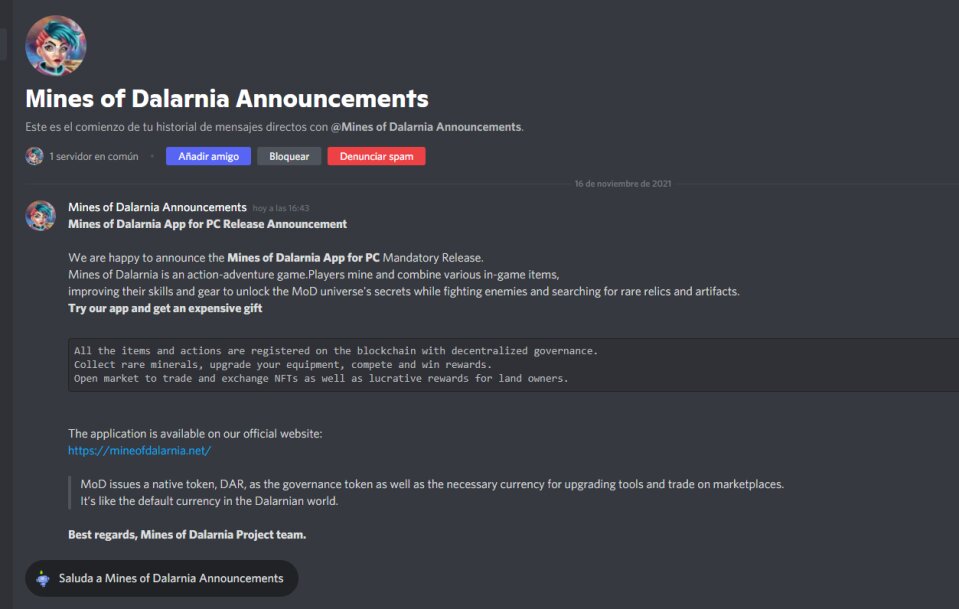

As you can see in the image above, the email includes a link where users can download the application. Of course, it states that the source is their official website.
Once the recipients click on the URL, it will direct them to a decoy site that looks legit enough to fool just anyone.
The victims are prompted to select Download App in order to get the application. However, all they’ll be getting is a malicious installer that embeds the Crypter with the payload.


The original website doesn’t say “Download App.” Instead, it asks the users to click on “Play Now” if they wish to install the application on their device.
But that means nothing, the website still looks legit. The attackers even took extra measures to ensure that the trick goes all the way.
If you noticed, the website has an HTTPS connection. Well, that’s because the attackers used LetsEncrypt to enable the feature.
Not to mention that the attackers removed/added letters from/to the domain name to make the decoy site look a lot like the original one.
Finally, according to, the attackers might be Russian speakers as they most likely forgot to translate the HTML object from their native language into English. You can see it on the bottom-left corner of the screen in the image below.
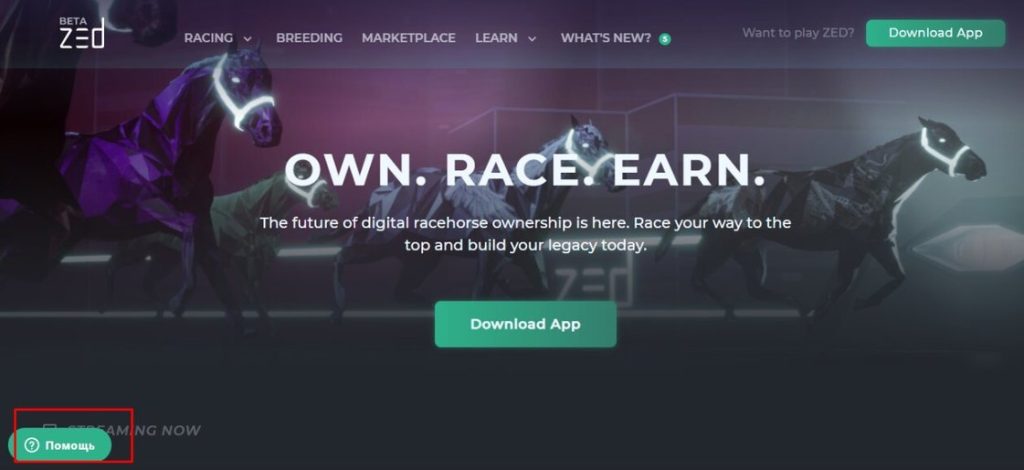

According to Morphisec, at least 82 domains were created between July 24, 2021, and November 17, 2021.
Babadeda Hits Discord – Let the Crypto Mining Begin
Phishing attacks are on the rise, be it by email, SMS, or messages on social media platforms, they’re here to stay.
You can either fall victim to such attacks or try as much as you can to avoid them. We’ll take the second option and advise you to stay aware of what you receive.
Don’t go clicking on links you’re not sure about. If you have doubts, visit the official website manually, at least you’ll know you’re safe.



