Fake TripAdvisor Complaints – Knight Ransomware Negotiates No More


Ransomware-as-a-Service has become a popular practice among cyber criminals. They target specific entities, encrypt their files, and ask for a certain ransom in exchange for the decryption key. This particular form of attack requires skills, especially in the “tricking the victim” department. And skills were definitely shown with the new Knight Ransomware attack.
Such practices are almost always the result of phishing attacks, and that’s exactly what it is now, as the individuals behind this recent attack are distributing the ransomware through a spam campaign disguised as TripAdvisor complaints.
It all starts with a fake email and ZIP file – the rest is well-known when ransomware is involved. What is this campaign all about? How are the threat actors implementing it? Find out below.
From Cyclops to Knight – Different Name, Same Modus Operandi
Ransomware attacks have been occurring more frequently in recent months. In fact, this year alone saw its fair share of such practices targeting huge companies around the world.
In fact, a while ago, Webtec’s Erie Plant suffered a similar fate. An attack on its systems caused disruption in its employees’ ability to log onto the network and do their jobs.
Before that, Colombian energy supplier EPM was hit with a huge ransomware attack caused by none other than the BlackCat group. Now, the Knight ransomware is in the spotlight.
The name “Knight Ransomware” saw the light a couple of weeks ago – By the end of July 2023. However, it’s been around for way longer than that, as it’s a recent rebrand of the Cyclop Ransomware-as-a-Service.
As we mentioned, the entire operation begins with a fake email masquerading as TripAdvisor complaints. Sophos researcher Felix discovered and analyzed the campaign.
Felix didn’t share any of the emails in question. However, he did state that the emails include a ZIP file attachment, “TripAdvisorComplaint.zip.” That’s what a typical phishing email includes. Instead of an actual executable file, the ZIP includes the Knight Ransomware.
The Detailed Process
Unfortunately, it doesn’t end here. Some. of the emails were seen spreading the ransomware variant via an HTML attachment named “TripAdvisor-Complaint-[random].PDF.htm.”
The HTML attachment redirects the users to a fake TripAdvisor page. Obviously, the threat actors behind this attack worked hard on this campaign. It’s all obvious, as the landing page is completely convincing.
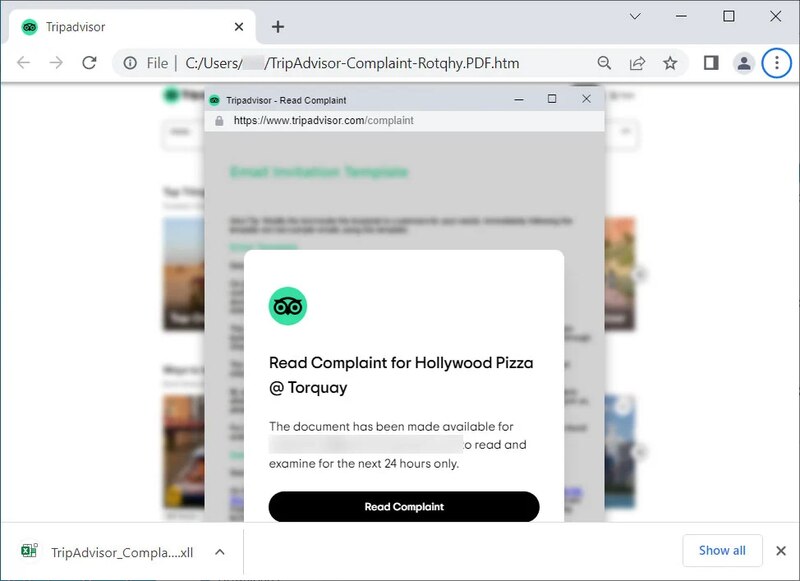

When the users click on “Read Complaint, an Excel XLL file named ‘TripAdvisor_Complaint-Possible-Suspension.xll’ will be downloaded on the device.
And we all know what happens next. The Excel file will prompt the users to “Enable this add-on for this session only.”
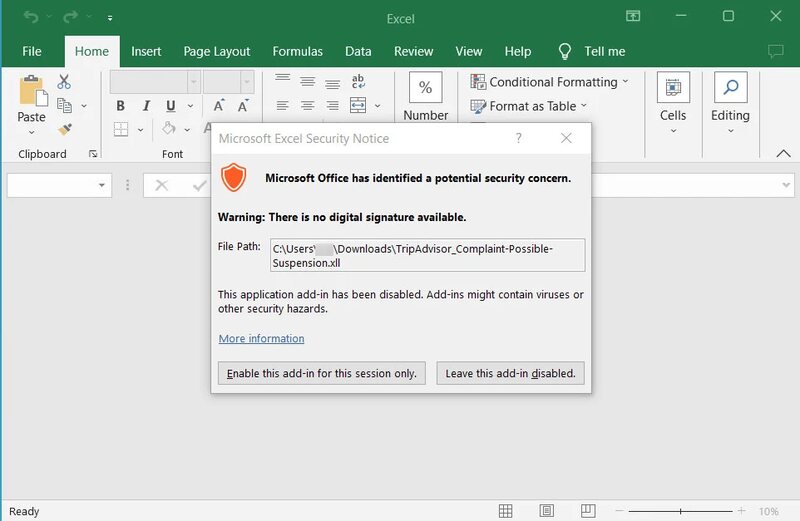

The moment the users click that option, the Knight Lite ransomware encryptor makes its way to the device and encrypts its files.
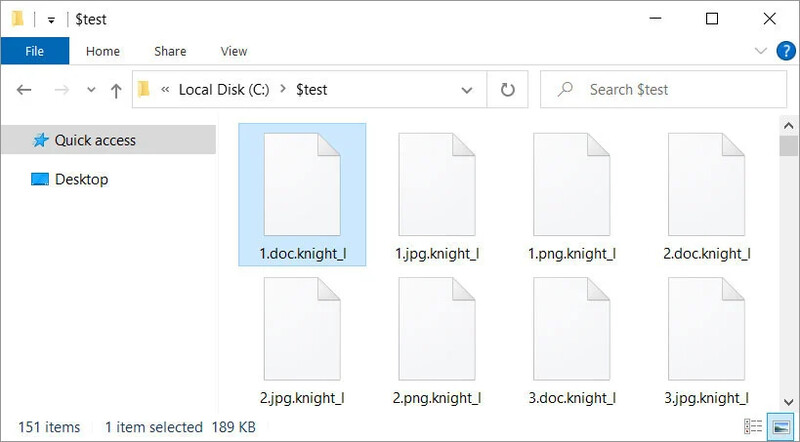

Just like any ransomware attack, the files contain a ransom note, where the operators of this campaign are asking for $5,000 to be sent to a listed Bitcoin address by following a link to the Knight Tor site.
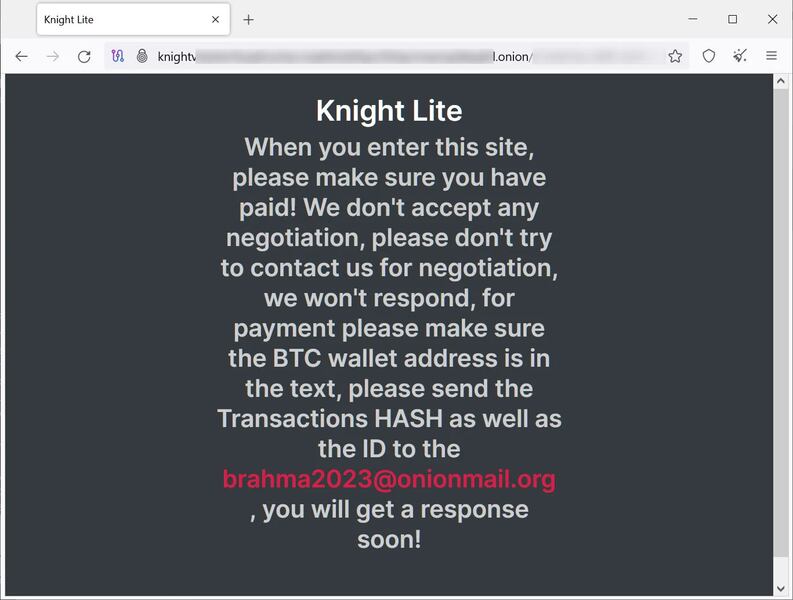

Usually, when the victims reach the website, they can negotiate with the attackers. However, these particular threat actors don’t seem to want anything to do with negotiations.
They just want their payment, and that’s it. Once the ransom is settled, the victims will end up receiving a decryptor from the Knight affiliate.
A Well-Executed Campaign
Using TripAdvisor as a disguise for this campaign is genius. The service is very popular all around the world, and the email delivers some sense of urgency.
Cybercrime is on the rise, and you need to take proper precautions when handling emails. Always visit a website manually – do not follow any provided link. Stay safe.



