A Magecart Operation: Online Shoppers Targeted with Formjacking


The methods used by cybercriminals to infiltrate our devices vary, especially when it comes to groups that have perfected their malicious craft. Speaking of “Perfected,” a new Magecart campaign is luring victims in with fake payment screens that look even better than the originals.
Using fake websites is a pretty common tactic among threat actors. However, it takes skilled ones to pull off what’s at hand. They’re now using realistic-looking fake payment screens to harvest sensitive information submitted by online shoppers without their knowledge.
This form of attack is very dangerous as the actors behind it can siphon credit card information. How are they implementing this? Find out below.
The Magecart Campaign – A Perfectly Executed Scheme
In the world of cybercrime, we’ve seen all sorts of schemes that allowed threat actors to harvest victims’ data, especially incidents where credit card info is included.
With elevated techniques and capabilities, these malicious groups are able to fool anyone. In fact, a while back, we witnessed one of the most believable phishing scams ever.
Threat actors impersonated none other than Verizon with pages that perfectly replicate that of the original.
Using math symbols (checkmark, a logical NOR operator, or a square root symbol), even the toughest AI-based spam detectors could not figure this out.
Now, we’re going through the same thing as the cybercriminals in this particular campaign are also using original logos to replicate compromised stores and hijack the checkout pages.
According to Jérôme Segura, director of threat intelligence at Malwarebytes:
“The threat actor used original logos from the compromised store and customized a web element known as a modal to perfectly hijack the checkout page.
The remarkable thing here is that the skimmer looks more authentic than the original payment page.”
The skimmer lies on the checkout page. First, the victim inserts his/her credit card information – as they do with every purchase. They don’t know they’re being scammed, after all.
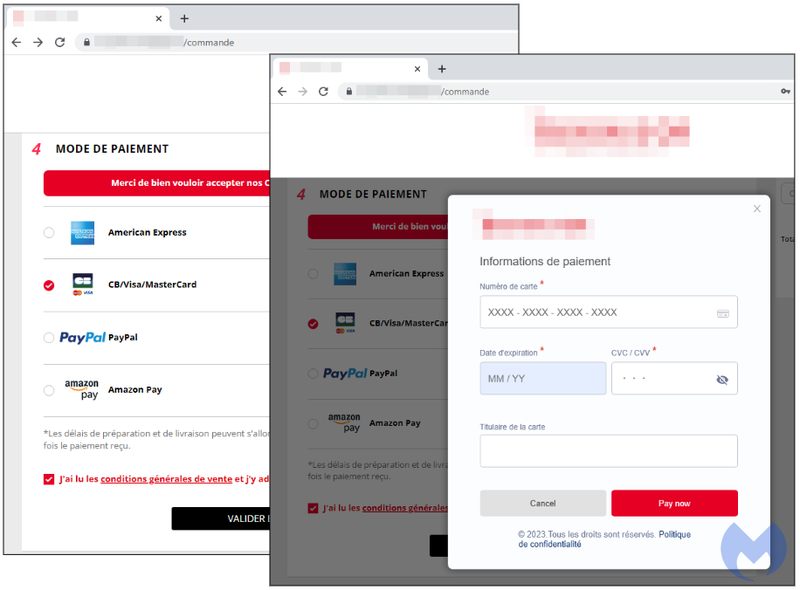

We have to give credit where credit is due. This is perfectly executed, and it can trick anyone. However, nothing is perfect, as every phishing scam has a flaw, and this one comes in the form of a “Politique de confidentialité (terms of use).”
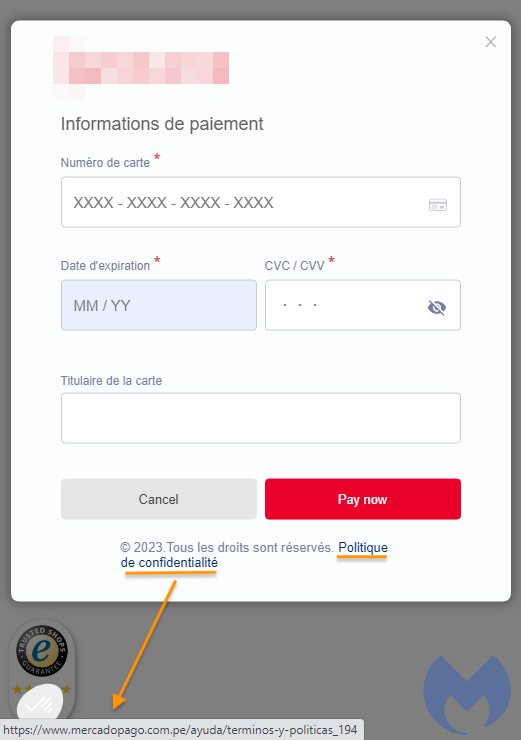

There is a mistake in the hyperlink, but unfortunately, not everyone is savvy enough to notice it. They’ll just proceed with the payment process to receive an error message about payment cancellation. In the background, however, data has been harvested.
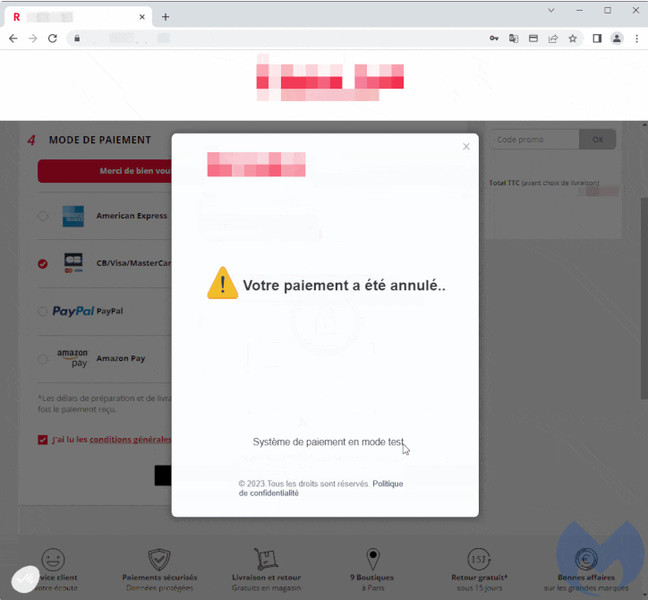

After this error, the skimmer will drop a cookie redirecting to the actual payment page if the user decides to redo it, at which point the payment will go through.
A New Campaign with Highly Advanced Capabilities
The Magecart name comes from several cybercrime groups that used skimming techniques to siphon sensitive information from e-commerce websites.
This form of attack dates back to 2010. As of 2022, studies show that over 70K stores have been compromised with some sort of skimmer.
Whenever you’re submitting your credit card information, make sure to check every single aspect of the platform/website. You never know what’s lurking within. Stay safe.



