Old Qbot Still Quick in Stealing Sensitive Data


If you think Qbot retired from the cybercrime life, you thought wrong. The malware is still very much in the game, showing no signs of aging despite first emerging in 2007. In fact, cybersecurity experts say that Qbot only needs about 30 minutes to steal your sensitive data once it infects your device.
Threat actors still use this malicious software, albeit with a few improvements, because of its high efficiency and fast spread. It exploits vulnerabilities in popular Microsoft apps like Outlook then, after infiltrating your phone or computer, steals your account credentials.
Old Bot, New Tricks
Qbot, a.k.a. Qakbot or QuakBot, is back raising havoc using light-speed attacks, according to researchers at The DFIR REPORT. The new study found that cybercriminals made improvements to the antique malware and unleashed it back in October 2021. What’s more alarming is how fast it spreads.
The report says that once Qbot infects your PC, it only needs around half an hour or so to steal sensitive data like emails and online banking credentials. Hackers target their victims through phishing campaigns, sending out emails containing malicious files or links. That includes scam messages and topics about COVID-19, tax payments, and job offers.
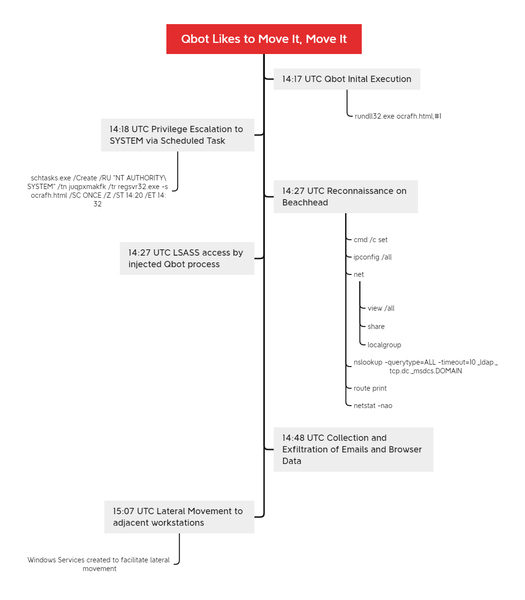
In one case the DFIR Report examined, initial Qbot access was unknown. But the victim was most likely infected via a malicious excel document. The malware used legitimate Windows apps like MSRA.exe to escape detection then created a schedule task to get higher access to the system. 30 minutes later, Qbot was stealing “browser data and emails from Outlook,” which could be used to spread to other networks.
“At around 50 minutes into the infection, the beachhead host copied a Qbot dll to an adjacent workstation, which was then executed by remotely creating a service,” said the report.
… and before we knew it, all workstations in the environment were compromised.
The DFIR Report
Qbot Infection Timeline

Qbot Branches Out To Ransomware
Stealing victims’ data isn’t enough for Qbot hackers. Some have even used it as ransomware after seizing corporate networks. The attackers would then demand a ransom in exchange for the stolen information. Ransomware gangs that used Qbot in the past include REvil, ProLock, and Egregor.
Kaspersky reported that Qakbot infected 65% more computers between January-July 2021 than in the previous year. Microsoft warned that it is very versatile malware with a modular design, appearing as a series of separate attacks on a network. It also deploys several variants of malware and ransomware. That makes it harder for cybersecurity tools to detect it.
However, threat actors mainly launch Qbot in email phishing scams, so your best line of defense is prevention. Be careful not to click on random links from unknown sources, and make sure you check the sender’s validity.



