COVID-19-Related Cyberattacks Increased Significantly, New Study Finds


- Coronavirus-related cyberattacks increasing
- Hackers using new malware and attacking methods
- Spear-phishing attacks on the rise
- COVID-19 cyberattacks by industry
The COVID-19 pandemic crossed all borders, and its effects disrupted every sector. Millions of people lost their jobs, and countless others suffered pay cuts as businesses and organizations try to stay afloat. Industries like education, retail, tourism, hospitality, sports, aviation, and many more took massive hits, and many companies are unable to get back on their feet.
But one sector significantly affected by the Coronavirus yet somehow manages to slip under the radar in daily conversations is cybersecurity. As employees shifted to working from home and using private, less secure computers to access company data, cybercriminals seized the opportunity to up their game.
According to a recent study, cyberattacks related to the Coronavirus increased by several hundred percent. And the most popular means of attack: phishing emails. The study also observed new methods through which hackers duped their victims.
Hackers Exploiting Pandemic to Launch Cyberattacks
Cybercriminals are always looking for new ways to breach your device and steal your data. They take advantage of ongoing events happening worldwide to scam victims and steal their information without their knowledge. The COVID-19 outbreak was an ideal platform for launching cyberattacks as the entire world went into lockdown.
As a result, businesses shifted to the digital world. A massive number of employees began working from home without proper cybersecurity protection. Workers used their private computers to access company tools, systems, emails, and files. And the only thing standing between laptops or desktop computers and malware is an antivirus program. Moreover, there are no cybersecurity team members to monitor any suspicious activities.
All these factors created the perfect environment for cybercriminals, who launched an all-out war. They sought to take maximum advantage of the coronavirus situation and used every trick up their sleeves, including new malware and attack methods.
New Malware Arising
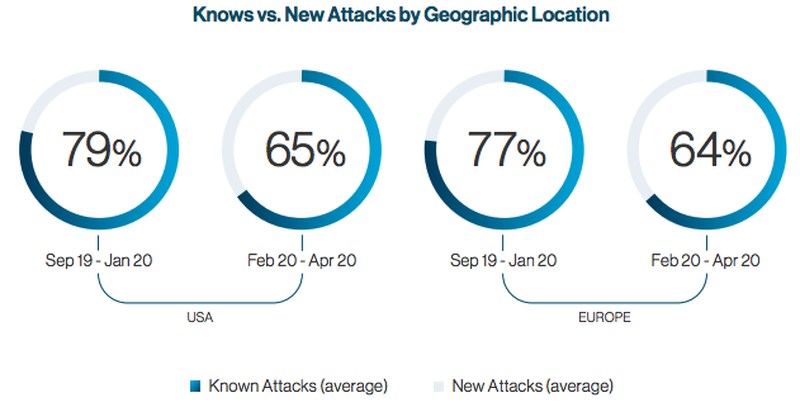
Cybersecurity firm Cynet reported a change in cyberattacks in Europe and North America ever since the Pandemic began. The company released a study recently, showing there’s been an increase in new malware and attack methods. Prior to the Coronavirus outbreak, data showed that hackers used existing malicious software in approximately 80% of their attacks, while the remaining 20% contained new malware.
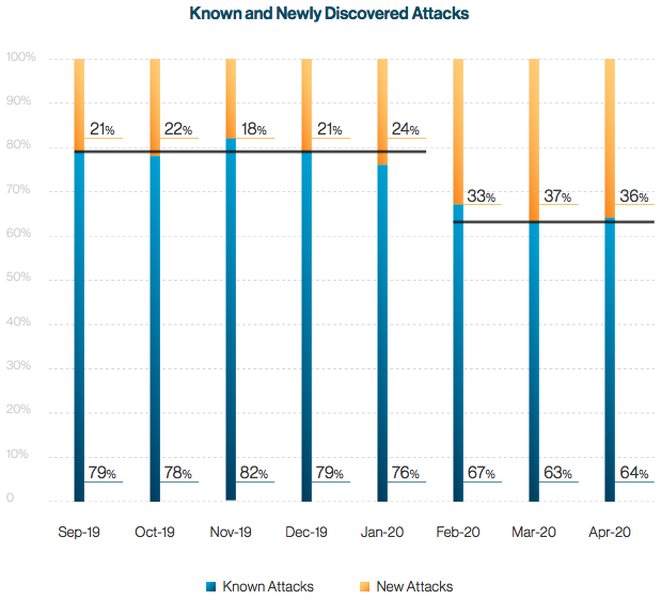

But in early 2020, following the spread of COVID-19, Cynet recorded an increase in “the amount of new phishing attempts, new malware variants, and even new malware.” As a result, the percentage of known attacks dropped to 65%, while new ones rose to 35%. The problem is that new malware is hard to detect by security systems, while old ones are generally picked up and dealt with.
This, of course, depends on the type of cybersecurity system you have. Regular users usually don’t go for advanced solutions, settling for an antivirus program instead. Some even use free antivirus software, which offers limited protection. But even with the latest safety measures, falling victim to a cyberattack can happen to anyone, especially if you consider the human error factor.

Spear Phishing Main Vessel for Attacks
Cynet’s COVID-19 Cyberattack Analysis shows an increase in spear-phishing attacks. Phishing is an email scam that hackers send to multiple recipients posing as legitimate entities like bank employees. They urge you to click on a malicious link or download a harmful file or document. And once you do, the malware infiltrates your device and steals your data without your knowledge or permission.
Some cybercriminals use this method to infect your device with ransomware, malicious software that encrypts your files. And the only way to get them back is by paying a ransom.
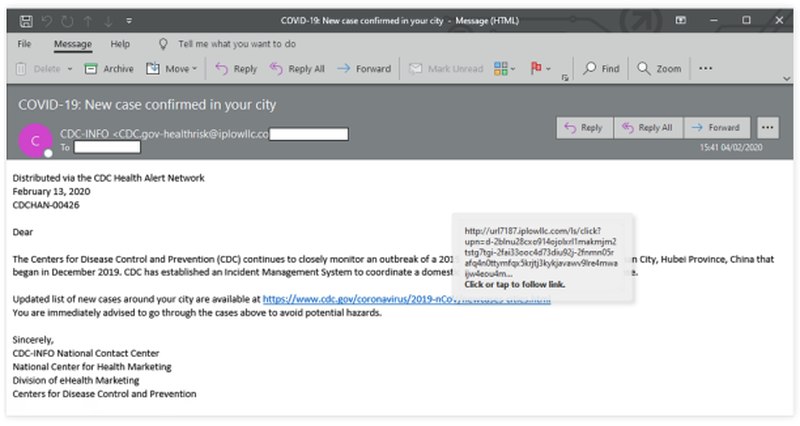

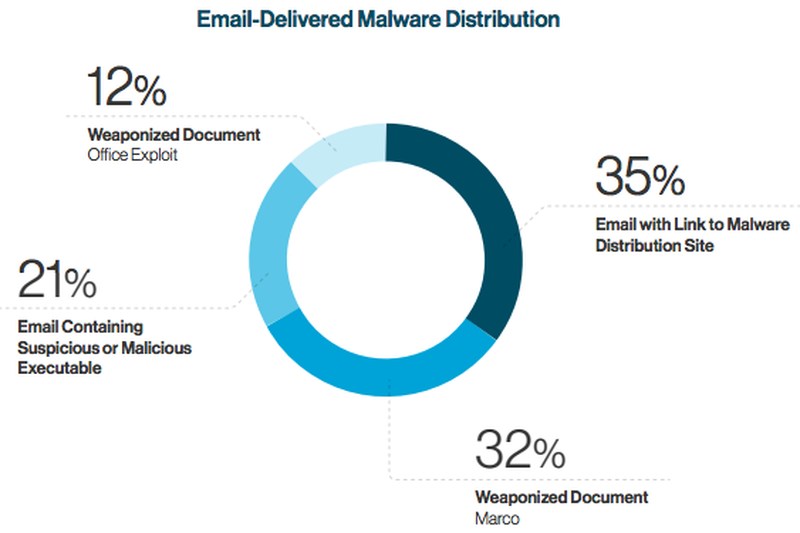
Now, in spear-phishing attacks, criminals select an individual target, instead of hundreds or thousands. During the Pandemic, scammers sent Coronavirus-related emails to people, posing as trusted sources like the Center for Disease Control (CDC). And based on Cynet’s report, the emails contained malicious attachments in the form of:
- Weaponized office document containing a Macro script that can execute a script on the victim’s host machine.
- Weaponized office document containing an exploit that utilizes a known or 0-day vulnerability in order to execute code on the victim’s host.
- Containing a malicious executable as an attachment.
- Containing a link to a malware distribution site which can infect the victim’s host machine.

Thinking this is a legitimate source, some victims proceed to click the infected attachment. This allows hackers to collect your data, infect other devices within the network, or gain high-level resources access.
Most Affected Industries
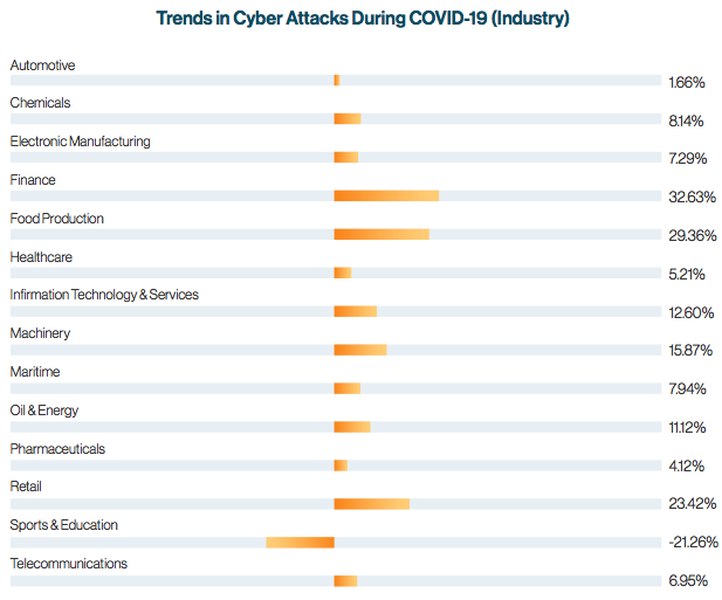
As I mentioned earlier, the number of cyberattacks related to COVID-19 grew by several hundred percent. In fact, several reports suggest that most emails concerning the pandemic are now malicious. And industry sectors aren’t just suffering from the financial impact of the Coronavirus, but also the fallout of hacking.
Cynet analysis showed a cyberattack spike in most industries. The cybersecurity firm compared the number of attacks during the pandemic to the prior three months. It found that the finance, food production, retail, and machinery sectors registered the highest increase, especially the first three (+20%). Sports and education was the only sector that witnessed fewer attacks during the outbreak than before.

Is It Possible to Avoid Cyberattacks?
Despite the increasing year-on-year cyberattacks, which continue to make headlines worldwide, many companies still don’t advanced security tools. The best way to protect your business is by investing in technologies that can detect malware early on and act accordingly. Having Extended Detection and Response (XDR) and a managed detection and response (MDR) team that’s available 24/7 will vastly improve your cybersecurity.
However, having these technologies and other system protections will only reduce cyberattack risks, not prevent them. That’s because new malware is always tricky to pick up. The Cynet report says that the only way to detect it is by using behavioral and heuristic analysis. Meanwhile, existing malicious software is easier to spot with static, signature-based techniques.
Furthermore, never ignore the possibility of human error, which can put a dent in any network security system no matter how safe it is. Therefore, in addition to advanced technologies, companies must properly train their employees to identify shady emails that contain malicious content. These emails must be forwarded to the IT or cybersecurity department. The professional personnel will identify the threat, see if it caused any damage, and nullify it.



