Twilio Phishing Attack – Simple SMS, Major Data Breach


Targetting big companies in phishing campaigns has become a very common tactic by cybercriminals. A couple of months ago, Cox Communications suffered a huge breach, which allowed the attackers to gain access to customers’ personal information. Now, cloud communications company Twilio suffered the same fate as the threat actors managed to steal employee credentials in an SMS phishing attack.
The attack is very sophisticated and it aims to harvest customers’ information at the end of the process. This shows how capable the threat actors are.
Tricking employees and stealing their credentials is not as easy as it may seem. But with few social engineering techniques, it’s possible. How are the threat actors implementing this malicious campaign? Find out below.
Twilio Phishing Attack – A Small Text for Total Control
As we mentioned, targeting big companies can be very beneficial for cybercriminals, especially if the company falls into the communication department.
Back in 2020, 75% of organizations around the world fell victims to some kind of phishing attack. This shows that malicious attacks are accelerating in numbers, which definitely poses a real threat.
In fact, when Verizon – one of the largest U.S.-based telecommunication service providers was used in a phishing campaign a couple of months ago, we knew that hackers would stop at nothing to achieve their goals.
Twilio has around 256,000 active customer accounts – a decent number that cybercriminals can easily benefit from. It all starts with an SMS and ends with harvesting customer information. Here’s what the company had to say:
“On August 4, 2022, Twilio became aware of unauthorized access to information related to a limited number of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials.
The attackers then used the stolen credentials to gain access to some of our internal systems, where they were able to access certain customer data.“
Phishing campaigns that include some sense of urgency usually end up with high success rates. This time around, the attackers are preying on Twilio employees’ “fear” factor. They sent them warnings that their passwords had expired or were scheduled to be changed.
The text includes a link, which is practically how a phishing campaign works. The image below showcases what the employees received during this attack.
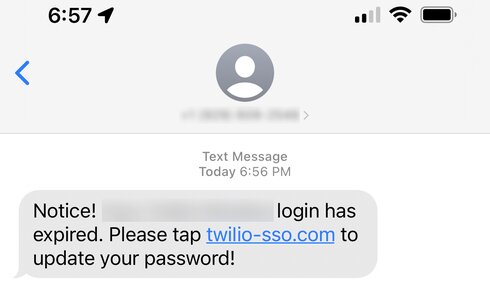

The URL that contains URLs containing “Twilio,” “Okta,” and “SSO” (short for single sign-on) keywords redirects employees to a Twilio sign-in page clone.
Once there and the employees submit their data, the attacker could intercept the login credentials and use those to access the compromised accounts. The company refused to provide any additional information about the attack.
EMEA Communications Director Katherine James did not respond to any questions considering how many employees’ accounts the attack compromised or how many customers it affected.
A Nicely Calculated Attack – From SMS to SOS
The attackers did put a lot of effort into this attack. Presumably, they collected the data from other breaches and searched for Twilio employee names with their phone numbers.
If the rumors are true, the attackers managed to get all of this information from LinkedIn’s latest data breach. Twilio sent emails to the affected customers.
If anyone did not get such notifications, it means there is no evidence that the attack affected their account.



