MacStealer Emerges – New macOS Malware with Familiar Capabilities


When it comes to malware infections, we rarely encounter any involving macOS devices. According to reports, Android platforms are the most susceptible to cyberattacks – Even via Google Play Store. macOS is very secure, but apparently, not that much – Enter MacStealer.
In a new campaign, threat actors are using this new information-stealing malware that has the ability to siphon sensitive information from infected devices.
While still a work in progress, MacStealer can do a lot of damage once it sets root. So, how does the process take place? What capabilities does this malware possess? Here’s what we know.
MacStealer – iCloud Keychain Data at Risk
As we mentioned, the possibility of infecting a macOS device is pretty low, but in some cases, the threat actors have what it takes to execute it.
Unlike Android and Windows devices, macOS thoroughly checks what software a user is downloading. In fact, even if the app is not from the App Store, the Mac device checks that Apple verifies the developer via Gatekeeper.
Not only that, but it also examines the file for malware and malicious code. Yes, Apple devices are fairly secure, which shows how capable the threat actors in this campaign are.
Threat actors are selling the malware on hacking forums for $100. Once MacStealer infiltrates a device, it sets its focus on image files, PDFs, archives, Google Chrome, Mozilla Firefox, Brave browsers, Microsoft Office files, and Python scripts.
After that, it starts harvesting iCloud Keychain data, passwords, and credit card information. The report by Uptycs researchers Shilpesh Trivedi and Pratik Jeware doesn’t state how it’s delivered, but it does clarify that it is propagated as a DMG file (weed.dmg).
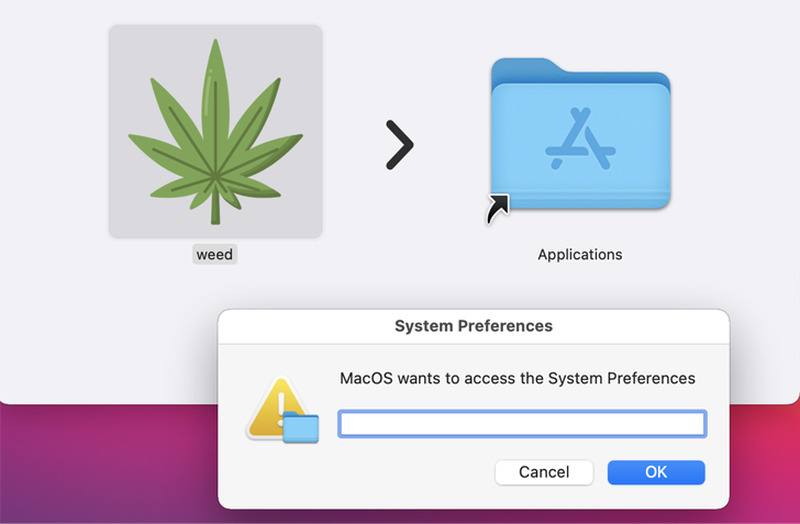

Once the users execute it, a fake password window pops up seeking access to the System Settings app. In reality, it’ll harvest everything the user submits.
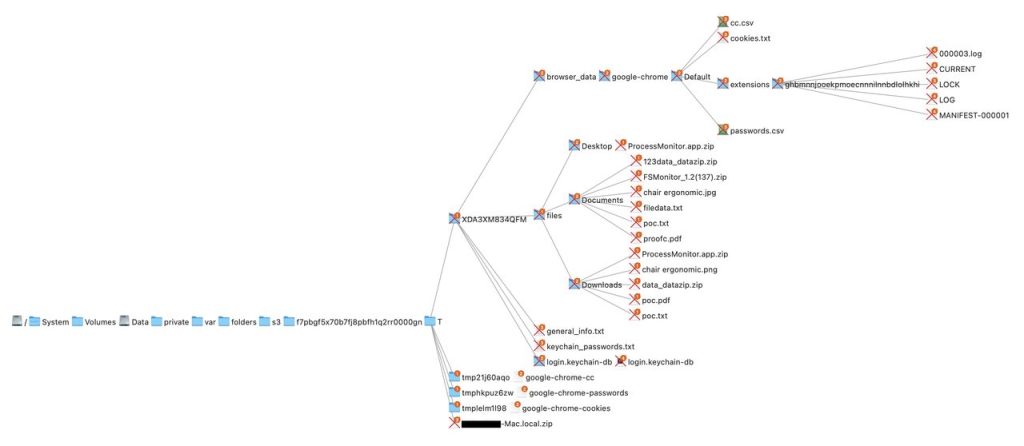

The report states that the authors behind this malware are upgrading it regularly. Soon, it might be able to capture data from Apple’s Safari browser and the Notes app. Things are going to get riskier in the near future.
Malware Infiltration Hits macOS
Such malware families spread through various methods, including email attachments, fake software downloads, and other social engineering techniques.
The most common one would be phishing emails, which we’ve seen a lot this year. MacStealer is still in development, but it’s going places.
We advise Mac users to update their devices’ software to the latest version and perform a thorough scan as soon as possible. You don’t want to end up facing such a malware family – Your data is at risk.



