New Android Phishing Attack – Malaysian Banks Credentials At Risk


Phishing attacks targeting Android devices don’t seem to be stopping anytime soon. A while ago, the malware took on the form of fitness apps, QR Codes, as well as device cleaners.
However, this time around, a fake Android app is masquerading as a housekeeping service. What does it do? It steals the bank credentials of 8 different Malaysian banks.
Cleaning Service Malaysia – an app that’s supposed to help with cleaning houses is actually “vacuuming” one-time passwords and MFA codes used in e-banking services.
The impact is big and sensitive information is on the line, which is why you need to learn more about it. Here’s what we know about the new phishing campaign.
Cleaning Service Malaysia – The Ultimate Cyber Vacuum
Recently, phishing scams have been flooding the official Google Play Store. However, most attacks come from fake websites and social media accounts.
The Cleaning Service Malaysia malware is yet another form of attack, created to target Malaysian users and their banking credentials.
The app’s promotion technique relies on multiple fake or cloned websites and social media accounts, which in the end, prompt the user to download its malicious APK.
Once the victim downloads the app, it requests personal information such as name, phone number, and address. (Check the image below).
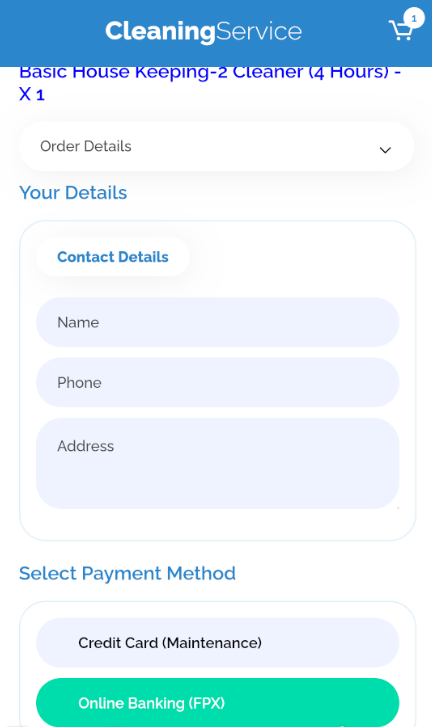

Once entered, the application sends the information to a C&C server (hosted by the attacker) as plain text. You can see more details in the following demonstration:
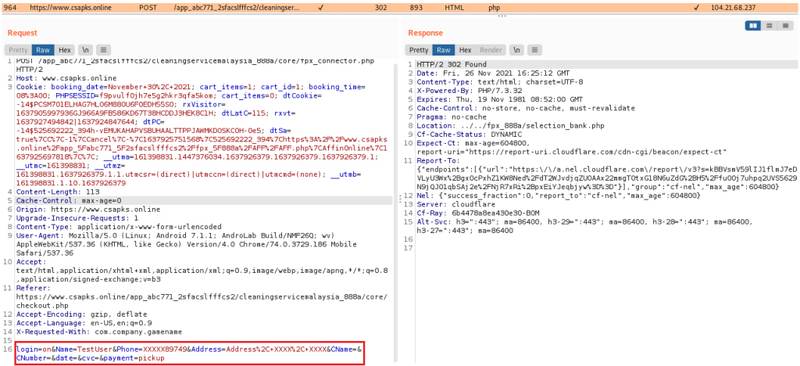

Next, the application asks the users to select their payment method. This is where everything bad happens. On the payment page, the malware lists multiple Malaysian banks to choose from (8 of them).


When the user selects their respective bank, the malware loads a page perfectly crafted to resemble that of the bank’s legitimate Internet Banking page.
Whatever the user submits in this step is harvested by the actors. But, unfortunately, there’s more. The app requests several permissions, and one of them doesn’t make sense at all.
When downloaded, users should allow permission to text messages. Why? Aside from harvesting banking credentials, the malware intercepts SMS code to access any OTP messages the victim receives.
In other words, the threat actors will have full access to the banking account without the users’ even knowing about it.
Something’s Off!
Based on Cyble’s thorough analysis, the threat actors themselves fell victim to several missteps that can easily identify them as “FAKE.”
First, their website’s URL seems quite odd on its own: “hxxps://www.csapks[.]online/app_abc771_2sfacslfffcs2/cleaningservicemalaysia_888a/core/main.php.”
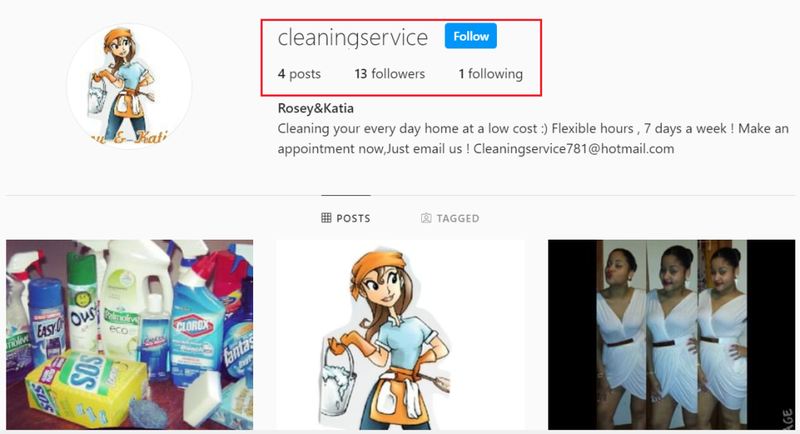
While trying to be more convincing by adding social media accounts, the attackers missed the mark as they did not fake the number of followers they have.
As you can see in the image below, the fake service’s page does not have a lot of followers or posts. When it comes to credibility, that’s not a good sign, which makes it really hard to trust.

Another suspicious act comes from their other posted social media account “Facebook.” When users select that, they’ll be redirected to a page that belongs to a legitimate company known Balabusta Brooklyn.
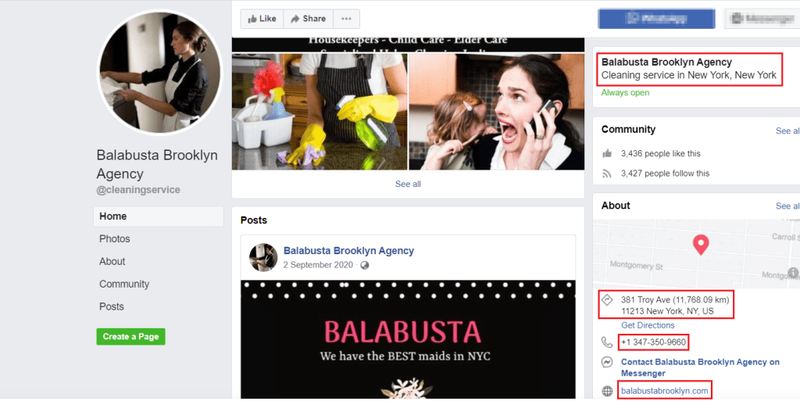

The image above clearly shows a different agency. However, what’s interesting is the fact that the page shows the actual country of the agency (New York). Apparently, the attackers didn’t put much thought into this.
And finally, Cyble researchers found a website that looks to be the one the attackers are trying to mimic. You can see UI resemblance in the image below:
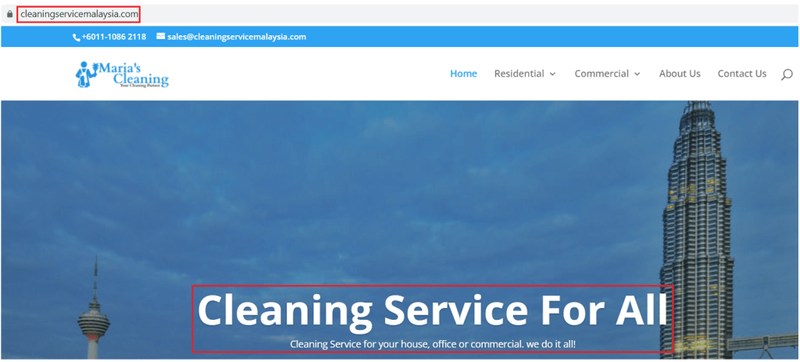

While the attackers did their best to perfect the scam, but as you can see, they still had some flaws that help detect it. All you have to do is keep a watchful eye.
The New Banking Trojan – Clean Up on Aisle Android
The Cleaning Service Malaysia malware should be a wake-up call for anyone using Android devices. Downloading apps from unofficial sources can be very dangerous. Therefore, always make sure to download Android apps from the official Google Play Store.
Moreover, keep a watchful eye on the requested permissions. If the app is asking for more than it requires to operate, look the other way instantly.
Finally, don’t give away your credentials unless the app/website is legit. Stay safe.



