BrazKing Android Malware Resurfaces and Targets Brazilian Banks


Spreading malware through fake SMS has become very common, and recently, a new campaign is spreading the resurfaced trojan – BrazKing.
Unlike other trojans, this one does not rely on apps distributed through Google Play. On the contrary, attackers are targeting the users’ fear factor, tricking them into thinking that their Android system is not up to date.
An SMS leads to a website, a website leads to download an APK, and finally, the malware is installed. What is this about? How do the attackers operate? Find out in this article.
Update Your Software and Fall Victim
IBM Trusteers researchers found the malware outside the Play Store. But how are the users ending up installing the malware?
At first, they get an SMS stating that their Android version is outdated. The SMS is shown in the image below:
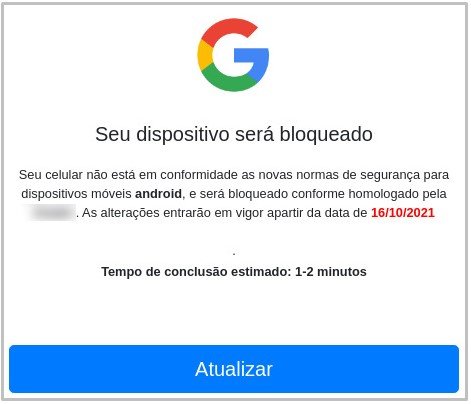

The message includes a link that takes the victim to a website that seems very legit. Once there, the user is prompted to download an APK that will allegedly update their system to the latest version.
If some users are aware of such scams, they’ll think that they’re safe if no permission was granted. However, this malware is using a new technique.
It only needs one single permission – allowing “Downloads from unknown sources.” Once allowed, the malware infects the device and requests access to the ‘Accessibility Service’.
With full control now, BrazKing can perform the following malicious activity. (Source: Security Intelligence).
- Dissect the screen programmatically instead of taking screenshots in picture format. This can be done programmatically but on a non-rooted device that would require the explicit approval of the user.
- Keylogger capabilities by reading the views on the screen.
- RAT capabilities—BrazKing can manipulate the target banking application by tapping buttons or keying text in.
- Read SMS without the ‘android.permission.READ_SMS’ permission by reading text messages that appear on the screen. This can give actors access to 2FA codes.
- Read contact lists without ‘android.permission.READ_CONTACTS’ permission by reading the contacts on the “Contacts” screen.
The malware can detect any login attempt to banking accounts. After that, it connects to the command and control server, which allows the attackers to receive the correct login credentials.
You can see BrazKing’s overlay techniques and how stealthy they are in the image below:
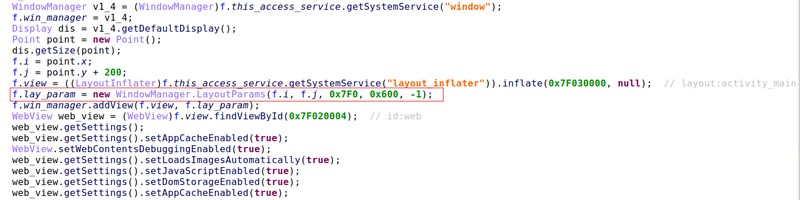

Not only does it do damage, but it also makes sure that no one can undo it. The malware uses obfuscation to go undetected and taps on the ‘Back’ or ‘Home’ buttons to prevent the users from deleting the malware.
BrazKing – The Malware is There to Stay
BrazKing is a serious threat. Users will have a hard time detecting it, let alone deleting it. If the victims try to use Antivirus software in hopes of scanning and removing the malware, it’ll tap on the home button continuously.
To avoid this, all you have to do is be very careful when downloading apps. Don’t use unofficial sources, especially while operating an Android device. Always use Google Play Store for getting apps, and you’ll be fine.



