Strategies for Your Businesses to Block Cyberattacks


- Implement zero-trust policies
- Use the blockchain and VPNs for data encryption
- Avoid public Wi-Fi
Global cybercrime inflicted damages worth more than $45 billion to businesses worldwide in 2018. According to a report from the Internet Society’s Online Trust Alliance (OTA), over two million cyber incidents were responsible for the losses.
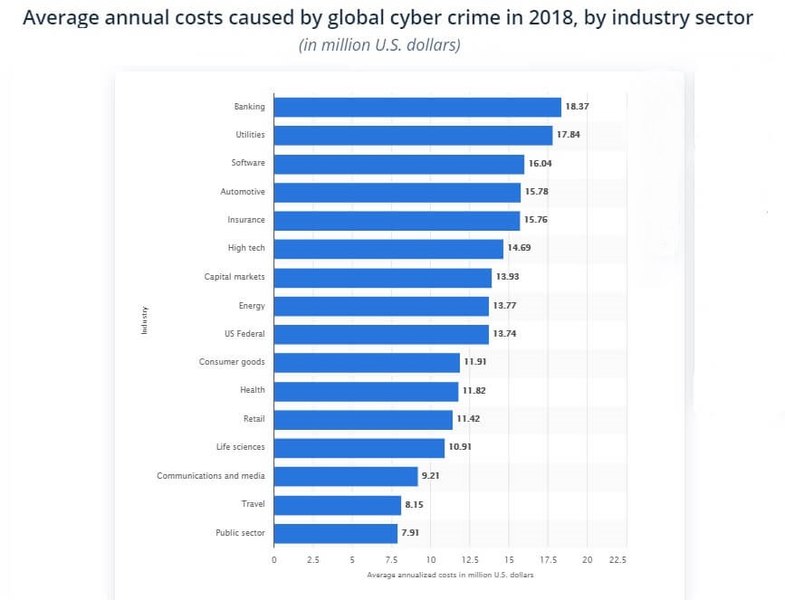
The banking sector took the most significant blow, losing an annualized average of $18.37 million during that period, according to Statista. Meanwhile, the utilities and software industries reported an average of $17.84 million and $16.04 million in damages, respectively.
But you cannot accurately measure the losses that cybercrime is inflicting on businesses. There are other factors one must consider, like rebuilding damaged reputations, restoring compromised data, and investing in cybersecurity to prevent future attacks.
While weak security measures are responsible for several data breaches and network penetrations, more businesses are becoming victims of targeted attacks. And an increasing number of cyber threats are aimed at small and medium-sized enterprises (SMEs).

That is an alarming trend as SMEs lack resources to implement the necessary IT security measures and rarely attract in-demand cybersecurity talents.
Nonetheless, all businesses can adopt several cybersecurity strategies to mitigate the risk of data breaches. And I don’t mean installing specific software like antiviruses or firewalls. I’m talking about implementing a full model that minimizes hacking risks and makes your data as secure as possible.
Adopt Broad Zero-trust Strategy
Implementing a zero-trust strategy might seem like a paranoid approach to IT security. But in fact, that is how the most successful companies and government agencies treat both their partners and software vendors.
The zero-trust approach states that organizations should not trust any parties inside or outside their perimeters. Instead, they must verify everything that’s trying to connect to their systems before giving them complete access.
That’s because malicious entities can penetrate corporate systems through compromised accounts or networks of business partners. That includes the delivery of malware and ransomware.
How Zero-Trust Model Works
You need to be well aware of who has access to your company network so that you can protect yourself from data breaches. For example, work-from-home policies and remote access business apps can lead to unauthorized system entries. Therefore, you must adopt very strict and thorough user access rights for your employees.
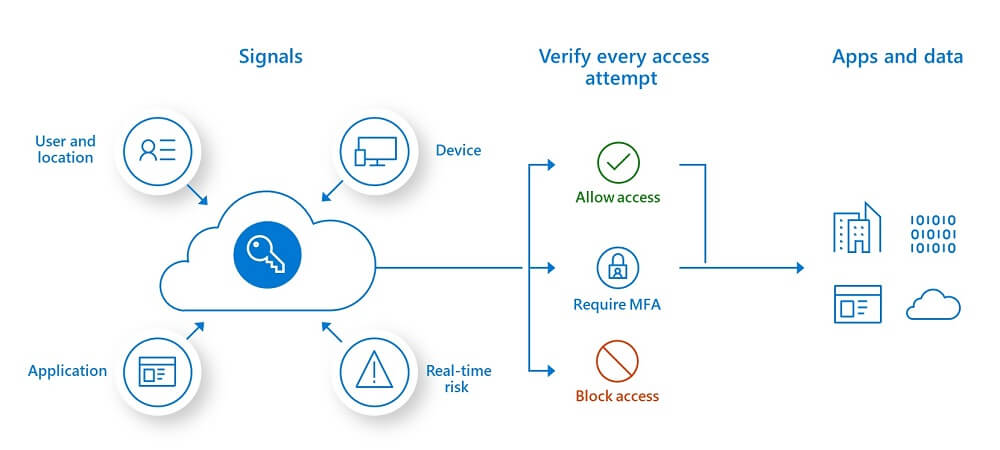

Furthermore, a lot of employees access work networks from mobile devices, most of which are relatively easy to hack. That gives you and other employers another reason to support a zero-trust policy and implement tight restrictions concerning who has access to what and from where.
Protect Your Data Using Blockchain
Blockchain is a relatively new technology that is yet to reveal its full potential. However, it offers unparalleled opportunities to protect your proprietary data. Manipulating files on distributed ledgers is almost impossible, making them a viable weapon to fight identity theft and protect intellectual property.
Storing data on a blockchain network prevents hackers from stealing copyrighted material, as there are numerous copies of the information on different devices. And every member of the network must validate the authenticity of the data.
Since the blockchain is a decentralized technology, cybercriminals cannot exploit a single weak point to change records or manipulate online financial transactions. Besides, most of the files and logs you store on the blockchain are encrypted by default. As a result, no one can see any of the information.
Perhaps the only way for a hacker to gain access to your secure blockchain data is to trick you into sharing your account’s security key. Brute force attacks are futile against blockchain networks. Yet, you should always take precautionary measures and avoid human errors.
Therefore, you should implement a zero-trust policy to avoid security breaches on the blockchain. Meanwhile, the distributed ledger is secure enough in terms of data encryption and copyright verification.
Eliminate Unsecured Networks
Wireless networks are everywhere, whether at home, work, or public spaces like cafes, restaurants, hotels, and airports. But the problem with public Wi-Fi is that it’s not at all safe. Hackers use these hotspots as hunting grounds to access and steal sensitive data.
Now, there’s a good chance that employees will, at some point, use public Wi-Fi to access corporate networks or business apps. When they do, they’ll connect to the system through an insecure network that does not require authentication or security keys.
And that is a dream come true for any hacker who is using that network. He’ll be able to launch man-in-the-middle attacks and steal the data you exchange over this insecure connection, including login credentials. In fact, hackers routinely scan public Wi-Fi networks looking for their next victims.
For that reason, you must ban any non-secure networks from accessing your business systems. If you have a bring-your-own-device (BYOD) policy in place, then all employee devices must have a corporate VPN installed. Virtual private networks encrypt your Internet traffic, i.e., the data that your device sends or receives. As a result, cybercriminals won’t be able to monitor or steal any sensitive information.
Furthermore, you should also have a policy for tracking and disabling lost or stolen devices, whether they belong to the company or an employee. A missing phone or computer with stored login credentials is a grave security risk. It provides hackers and other third parties with genuine access to your business apps.
Cybersecurity Strategies for Businesses – Final Words
Selecting and installing reliable security software is only the final step of a security strategy to protect business networks. An ad hoc approach toward cybersecurity results in incomplete and vulnerable solutions, which are also hard to maintain.
What you need in this cyberattack-ridden online world is a holistic approach that can eliminate threats before they even occur. Therefore, you must implement a zero-trust policy and use the blockchain and VPNs to encrypt data and all communication channels. In other words, you need reliable hardware and software solutions, but it all starts with a thorough cybersecurity strategy.
Are there any additional measures you can add to this business security strategy? Share your thoughts in the comment section below.



