Get Flash Player – Flubot is Back with an Upgrade


Spreading malware through phishing SMS is a very common form of cybercrime due to the fact that it actually works… with ease.
Not long ago, Flubot, one dangerous malware used SMS messages to spam thousands of Android users in Finland. Now, the malicious software is back with a frightening upgrade.
Flubot is targetting new Android devices in the form of an SMS prompting users to download Flash Player through a fake APK file. The problem this time around is that the malware can do so much more than it could before.
The danger of Flubot is real, and we’re here to shed more light on it. All you have to do is go through this comprehensive article.
Install Flash Player, Install the Flubot Malware
Flubot has a specific target in mind, a victim’s banking credentials. As mentioned, a while ago, Flubot sent more than 70,000 phishing messages in 24 hours to Finnish residents.
This time around, the malware also uses campaigns with SMS texts asking the recipient if they wanted to upload a video from their device.
The following example represents a text received by polish residents as reported by CSIRT KNF.
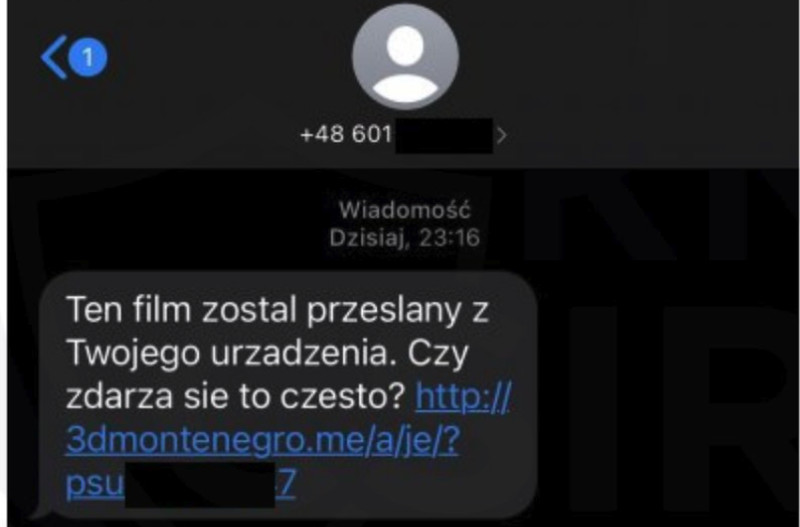

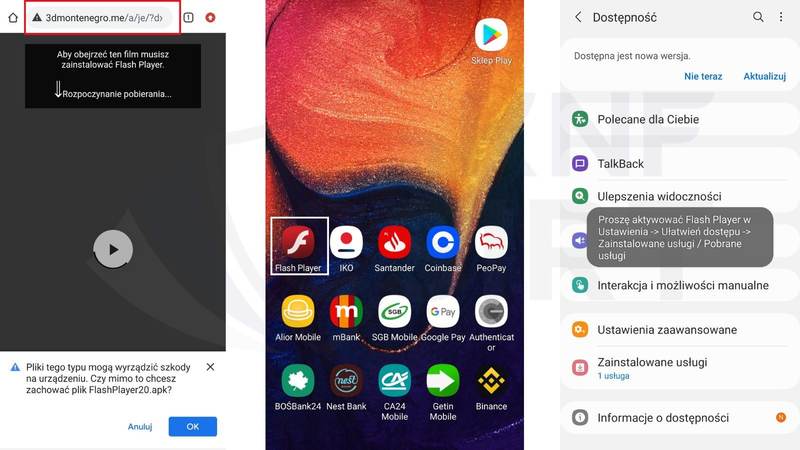
Just like Flubot’s previous attempts, the victims have to click on the link provided in the text message. Once they do, they’re redirected to a page that offers a fake Flash Player APK, which then installs the FluBot malware on the Android device.
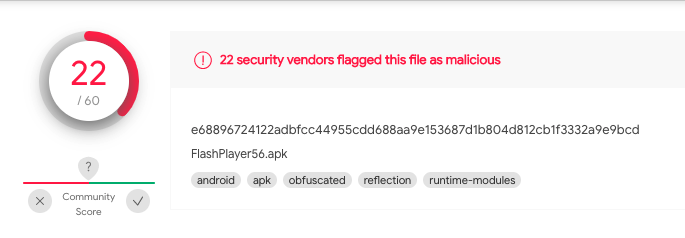
If the users have some tech-savvy background, they’ll easily figure out how malicious this APK file is by running a Virus Total scan. According to 22 security vendors, this APK is flagged as malicious.

We’ve recommended this before, and we’ll do it as many times as it requires to keep our readers safe. Never install apps from APKs hosted at remote sites.
That goes specifically for well-known applications like Flash Player as you can easily get it from the official source. If you’re wondering how the process goes, take a look at the images below:

In the past, the Flubot malware was capable of the following malicious activities:
- Access contact lists.
- Remove applications.
- Turn off Android Battery Optimization.
- Perform screen grabbing and keylogging.
- Make calls at will.
- Disable Play Protect
- Steal OTPs by intercepting text messages.
Now, the new variant (since it’s a commonly used word nowadays) can perform new tasks thanks to the upgrade it has gotten:
- Send lengthier text messages.
- Update the DGA seed remotely.
- Update DNS resolvers.
We’re here to shed light on what Flubot is, and what has it been up to lately. If you want a more technical representation, check out the F5 Labs report.
Flubot Updated – A New, More Contagious Variant
Flubot won’t be able to get a hold of your device if you don’t click on the link to download the infected application on your device.
If you manage to avoid that, you’ll be stopping the malware from spreading to your contacts, and from them to others.
Always make sure that what you’re downloading comes from an official source, and stay away from APK files. You never know what’s lies in those.



