Hello XD Ransomware – A Typical Attack with a “Backdoor” Twist


Ransomware operators seem to be on a roll recently, targeting more and more users all over the world. A typical attack sees threat actors exfiltrating a victim’s sensitive data, encrypting it, and threatening to publicize the information unless he/she pays a specific ransom. However, with the Hello XD ransomware variant, the process reached a new level of maliciousness.
The ransomware is not new as it first showcased its capabilities back in November 2021. Now, recent research highlights how the attackers have enhanced this variant and elevated its techniques.
With new features and capabilities, this upgraded sample features stronger encryption. In other words, it’s more dangerous than ever. How does it work? What techniques does this ransomware have? Find out below.
A New Variant – It Starts with a Hello
The use of ransomware has reached new heights in the last year. Big targets such as Frontier have suffered major breaches due to ransomware attacks.
The past ones were cliches, following the protocols of every single ransomware campaign out there. But now, things are quite different as the “Hello XD” variant has reached new levels in terms of execution.
Originally, threat actors used the leaked source code of Babuk to create Hello XD. When the ransomware was fully functional, the operators behind it targeted corporates using a small number of double-extortion attacks, stole their data, and then encrypted them.
A report by security research firm Palo Alto Networks Unit 42 explains how the creator of Hello XD designed a new form of encryptor. It has advanced technologies to avoid detection and executes different encryption algorithms.
In other words, the threat actor’s intentions seem to be creating a new ransomware strain with unique functionalities and features for attacks with absolute results.
A Malicious Process, with a Smile
Most ransomware attacks end up with a Tor site, where the victims finalize their payment process in exchange for a decryptor. However, Hello XD is not using that currently. Instead, the note instructs the targets to use a TOX chat service for further negotiations.
This ransom note by Hello XD explains everything the victims should do.


Just like most messaging platforms nowadays, TOX is a peer-to-peer instant messaging protocol that offers end-to-end encryption. It’s practically the perfect tool for ransomware groups to initiate their negotiations. This has been seen with the LockBit 2.0 operators.
The old variants of Hello XD didn’t pop much at first. When they first hit a Windows or Linux device, the desktop screen remained the same – it simply left the ransom note. Now, with this new one, the malware shifts the background to a ghost.
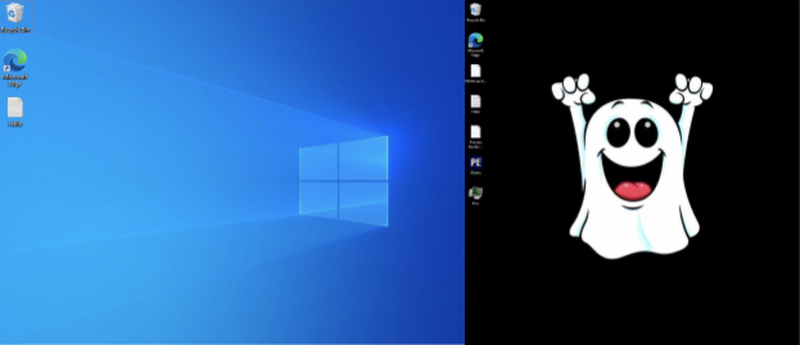

When the ransomware sets root, it disables shadow copies and prevents system recovery. Once that is done, it starts encrypting files by adding the .hello extension to their names.
Unfortunately, it doesn’t stop here. The title of this article states that there’s a twist and this comes in the form of a backdoor.
Hello XD places an open-source backdoor named MicroBackdoor. This allows the operators several privileges on the compromised system, including full navigation, file exfiltration, command execution, and the ability to wipe traces. The entire Hello XD operation is explained in this report.
Hello XD Ransomware – One Heck of a Malicious Salutation
Hello XD operators have enhanced their way of attacking users. With a backdoor in place, there’s no telling what they can do now.
All we know is that this particular threat actor seems to be knowledgeable and in a position to move Hello XD forward. Researchers have to analyze the threat to determine the damage that can be done in the near future.



