A Malicious WhatsApp App – Yo! They’re Stealing Your Access Keys


Android users have always had this one advantage over iOS ones – the ability to install unofficial applications. However, this is a bittersweet advantage as while they do have convenience, they’re also more susceptible to malware. Speaking of, YoWhatsApp is malicious.
We all love having that “One Up” over our contacts who use the official WhatsApp app. Well, with the ability to customize the interface, block access to chats, read deleted messages, and more – it is definitely enticing for users to install.
Several unofficial WhatsApp applications are out there to download. Some are good, some are ok, and some are downright malicious. Yes, YoWhatsApp was found stealing access keys for users’ accounts. What is this about? Find out below.
YoWhatsApp – An Unofficial App with an Official Threat
As we mentioned, unofficial WhatsApp Android applications are in the dozens and not all of them are designed to give you the convenience you’re looking for.
Sure, they make it easier, but if a malicious actor is behind them, things are definitely going South quickly. (Even the official version is susceptible to attacks).
Similar unofficial apps include WhatsApp Plus and the newly updated YoWhatsApp v2.22.11.75. Apparently, this new version of “Unofficial” WhatsApp snatches access keys, enabling the threat actors to control users’ accounts.
The past year has had its fair share of malicious attacks, especially through social media platforms. Kaspersky has been reporting such incidents for quite some time now and it’s been investigating cases of the Triada Trojan lurking within modified WhatsApp builds.
With YoWhatsApp, the threat actors are after the access keys. According to the cybersecurity firm, this modded app harvests users’ WhatsApp access keys and sends them to the developer’s (Threat actor) remote server.

Kaspersky did not state that any of these stolen keys have been used till now. However, the cybersecurity firm does warn users that threat actors might use open-source utilities to connect and perform actions as the user without even having the actual client.
Those include taking over the account, accessing sensitive communications with private contacts, and impersonating the real user. It doesn’t end here.
YoWhatsApp is a replicate of the real thing, which means that it will ask for the same permissions such as SMS access. In other words, users would be giving full permission to the Triada Trojan.
With such access, this malicious trojan can subscribe the victims to premium services without their knowledge or consent.
Yo! How is the Application Spreading?
Now that question is: If it’s an unofficial application, how are the threat actors promoting it? Well, we have to say that Snaptube is at it again.
In the past, Snaptube was spreading malvertising campaigns and now, it’s spreading YoWhatsApp ads. You can see an image highlighting the ad received through the popular video downloader:
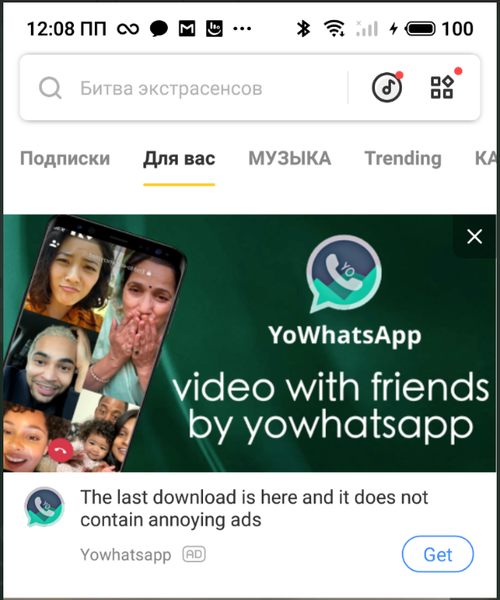

Kaspersky contacted the people behind Snaptube and notified them about the advertisement of malicious apps through their platform so that they can close the distribution channel.
Speaking of distribution through other platforms, we mentioned that there’s also another clone called WhatsApp Plus. This is also a malicious app that’s being advertised through the VidMate app.
We have to note that not every one of these unofficial clones is malicious. However, avoiding them altogether is definitely recommended just to be on the safe side.
YoWhatsApp – Convenience vs. Maliciousness
Convenience always comes with a price and with these apps, it’s always your private information. Unofficial apps, in general, are very dangerous to use, regardless of their functionality.
And when it’s a social media app that allows you to engage in private conversations, things can get out of hand in an instant. Even the real WhatsApp has had its fair share of cyberattacks in the past.
Our advice here is to stay away from any unofficial source to avoid this predicament. To be frank: Just use the normal WhatsApp application.



