Passwords at Risk – A Major KeePass Flaw Unearthed


We live in a time of passwords, where everything we do should always be protected with some sort of combination. Emails, Facebook, Instagram, and the likes require passwords, but how can users remember them? Easy! Password Managers, particularly the Open-Source one – KeePass.
For 19 years now, this software has been storing users’ passwords and keeping them safe all the time. However, recently, a vulnerability surfaced, which, once exploited, allows cybercriminals to retrieve the master password from the software’s memory.
CVE-2023-32784 is dangerous, especially due to the fact that KeePass hosts millions of passwords. What is this flaw all about? What can threat actors access once they exploit it? We’ve explained everything below.
Another Day, Another Vulnerability: Enter CVE-2023-32784
No matter how reputable the company is, flaws and vulnerabilities are bound to exist every now and then. That’s what security updates are here for.
The biggest companies around the world have had their fair share of flaws in the past few months. In fact, none other than Rubrik – the cloud data management service – disclosed a vulnerability in its GoAnywhere service.
In this particular incident, threat actors were able to harvest sensitive information belonging to their employees – no customer data was affected.
Even QNAP witnessed a critical and dangerous PHP vulnerability a while back. However, the situation is quite different with KeePass.
This open-source software is popular around the world. Users install it for free to store usernames, passwords, free-form notes, and file attachments in an encrypted file.
This encrypted file is well-protected with a Master Password, which brings us to the problem at hand. If malicious actors decided to exploit the CVE-2023-32784, they’d gain access to the master password created by users.
A security researcher discovered the flaw and published a KeePass 2.X password dumper on GitHub two weeks ago about how the exploitation process could go.
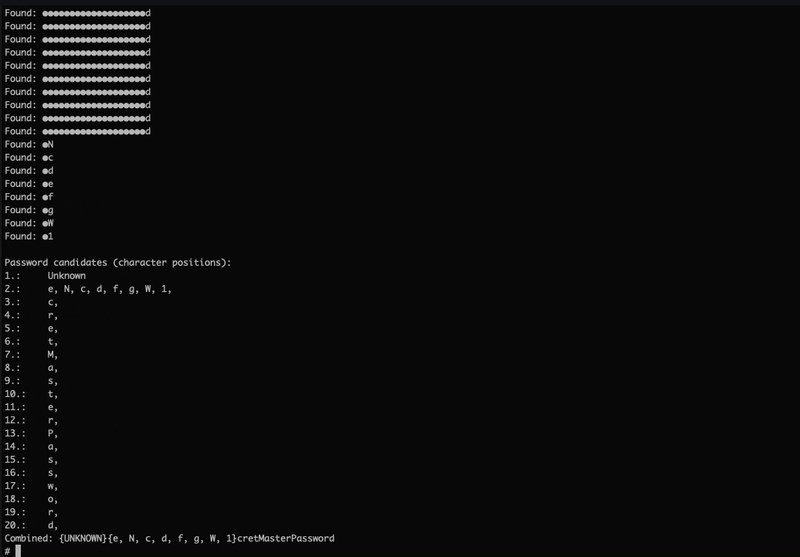

Based on the researcher’s analysis, this tool can retrieve the data from KeePass’ memory dump, which contains sensitive information.
After that, it delivers the potential password candidates to the users in plaintext form. It doesn’t matter where the data comes from.
Whether it’s from the process dump, RAM dump, swap file, or hibernation file, the tool will get the job done.
Yes, this is very serious and dangerous. As we mentioned, exploiting the vulnerability allows threat actors to obtain the master password, which is later used to unlock the software’s password database.
And finally, they’ll be able to siphon all credentials for all online accounts of the targeted user.
KeePass Flaw – Update the Software Now
According to Dominik Reichl, fixes have already been implemented. Now, once the users update their KeePass software, they’ll rest assured that the fixes can effectively prevent the exploitation of the flaw.
Another fix for version KeePass 2.54 will be made available by July 2023 and possibly earlier. If you’re using this version, make sure to stay tuned and update it on the spot.



