PennyWise Stealer – Horror Infiltrates the Crypto World


The IT movies have struck fear into viewers all over the world. Well, they should as Pennywise is one creepy clown. While horror does hit a nerve, it’s not real. However, when PennyWise infiltrates the online world as the newest malware variant, that’s when fear becomes a reality.
This stealer has the word “Penny” as part of the name, which directly indicates what it’s designed to do. Yes, it’s direct to the point – PennyWise harvests sensitive browser data and cryptocurrency wallets.
Cybersecurity firms have marked the malware as active due to its recent activities. It disguises itself as a free Bitcoin mining program and promotes itself through a very popular platform. What is PennyWise capable of? What platform is it using to spread around? Here’s everything you need to know.
PennyWise Stealer – Definitely not a Laughing Matter
Cryptocurrency wallets are used all over the world. In fact, back in 2021, the number of blockchain wallet users surpassed 68 million. The number continues to grow as we are introduced to new blockchain wallets and cryptocurrencies to the market regularly.
So far, Bitcoin remains the leader of the pack with over a $928.50 billion market cap. As a blockchain goes more popular, it becomes a valid target for cybercriminals.
A while ago, threat actors breached email marketing giant Mailchimp and were able to steal Trezor crypto wallet data. Now, a new threat is upon us and it comes in the form of PennyWise.
Spreading malware through popular platforms has become a common practice among attackers. With PennyWise, it’s no different as the operators behind it are using none other than Youtube.
Binge-Viewing Goes Malicious
The attackers behind PennyWise promote the malware through a video that showcases free Bitcoin mining software. The video includes a download link and those who are interested become instant victims.
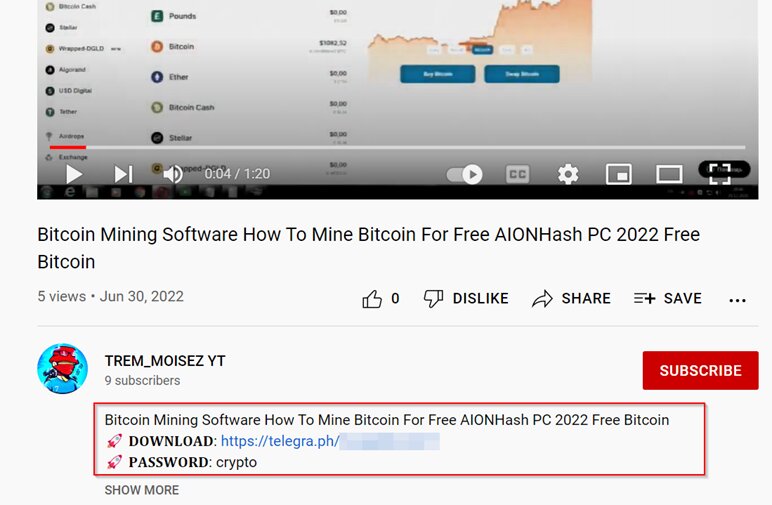

The malware, which is likely named after the monster in Stephen King’s horror novel IT, is very capable as it can easily target over 30 browsers and cryptocurrency applications. According to Cyble,
“In its current iteration, this stealer can target over 30 browsers and cryptocurrency applications such as cold crypto wallets, crypto-browser extensions, etc.
The stealer is built using an unknown crypter which makes the debugging process tedious. It uses multithreading to steal user data and creates over 10 threads, enabling faster execution and stealing.”
Once the software takes root within the device, it can perform several malicious practices. That includes taking screenshots and stealing sessions of chat applications such as Discord and Telegram.
But we’re not going to forget about its main objective. PennyWise exists to steal data from the victims’ systems. The stealer harvests data that comes in the form of Chromium and Mozilla browser information. We’re referring to cryptocurrency extension data and login data.
The malware causes a real threat to anyone who has access to Youtube. Why? Well, the attackers created a channel that consists of more than 80 videos.
In other words, that many videos on their YouTube channel will be the key to mass infection. Cyble shared an image of how many videos the channel provides.
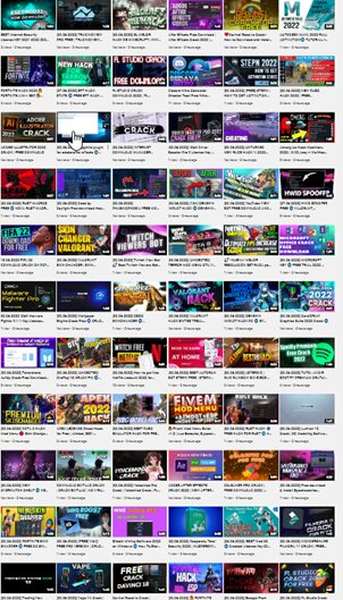

The attackers can easily take over the victims’ devices. Once they have everything they need on the attacker-controlled server, the data vanishes from the computer.
PennyWise Malware – Download, Install, Steal
Users always fall for the tricks and traps that cybercriminals set up for them. To avoid such a predicament, you should never download software from unverified or untrustworthy sources.
Aside from that, always keep your antivirus enabled for the purpose of installing a new application. Finally, stay vigilant and stick to your official app stores for any download.



