PhoneSpy – 23 Malicious Apps, 1000s of South Korean Victims


Are you into learning Yoga, browsing photos, or watching TV/videos online? Well, you better think twice before downloading any dedicated app from now on. That’s right – enter PhoneSpy
Recent events show an ongoing mobile spyware campaign embedded in around 23 malicious Android apps and used to siphon sensitive information and gain control of devices owned by thousands of South Korean residents.
PhoneSpy is a serious threat, not only to Koreans but to every internet user out there. What is and how does operate? Find out in this guide.
PhoneSpy – Zimperium Knows Best
The Dallas-based mobile security company Zimperium discovered the malware campaign. Apparently, the apps don’t rely on Google Play Store.
As mentioned, they masquerade as legit apps for Yoga and watching TV online. The process is simple. To prey on victims, the attackers need no official or third-party stores.
Instead, they apply social engineering or web traffic redirection to trick users into downloading the apps.
And apparently, it’s working as thousands of Korean residents have fallen victim to the attack.
According to Zimperium researcher Aazim Yaswan:
“With more than a thousand South Korean victims, the malicious group behind this invasive campaign has had access to all the data, communications, and services on their devices. The victims were broadcasting their private information to the malicious actors with zero indication that something was amiss.”
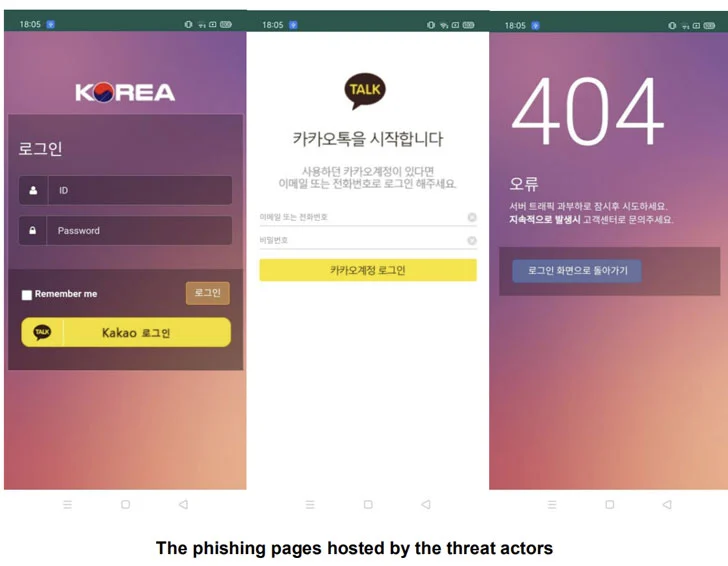
Now, once the app is installed, the application requests several permissions. Then, it opens a phishing site that’s perfectly crafted to look like login pages of popular apps such as Facebook and Instagram.
Once the users submit their login credentials, nothing happens. Instead, they’ll receive an HTTP 404 Not Found message.
While this may seem like a “Nothing happened” incident, the victims’ credentials have been stolen and redirected to a remote command-and-control (C2) server.
But Wait! There’s More
The attack is not contributed to a specific threat actor. Apparently, it has been passed down for years.
Various individuals have been updating and sharing it within private communities. And now, the variant is what’s striking Android devices in South Korea.
What exactly happens in the background? Aazim Yaswan explained:
“Many of the applications are facades of a real app with none of the advertised user-based functionality. In a few other cases, like simpler apps that advertise as photo viewers, the app will work as advertised all while the PhoneSpy spyware is working in the background.”
No matter how the malware operates, it’s just like any other trojan. It relies on the permissions users’ give the app and takes full control of the device.
Once the malware takes place, the attackers can access the camera to take pictures as well as get a precise GPS location.
Not to mention that they’ll be able to extract anything related to texts, call logs, as well as contacts.
PhoneSpy – Excellent Apps on the Surface, Malware in the Background
Malware that hits mobile devices is very a powerful and effective weapon against sensitive data.
To avoid such malware, spyware, and ransomware attacks, you must learn what websites to trust, how to choose your apps, and what links to click.
Make sure that the app is legit before getting it and never insert your information without double-checking the source.