Raccoon Stealer Malware is Back… More Malicious than Ever


Cybercriminals’ regular upgrades to their malware variants have been a constant threat to both home users and businesses. One of the most well-known and widely used among these families would be the Raccoon stealer. After a long hiatus, this dangerous variant is back with some new malicious capabilities.
This particular malware was last seen around six months ago when it targeted users via Search Engine Optimization (SEO) poisoning. However, after the arrest of its author, the info-stealer was nowhere to be seen.
Now, despite what went on, the developers of Raccoon Stealer information-stealing malware went public on hacking forums, promoting their new 2.3.0 version of the malware. Why now? What is the new Raccoon stealer capable of doing? Find out below.
Raccoon Stealer 2.3.0 – New Version, New Capabilities
In the world of cybercrime, info-stealers are considered some of the most effective methods to infiltrate systems and benefit from the targeted victims.
Raccoon, to be exact, is a well-known and widely used information-stealing malware that has been wreaking havoc among companies and organizations all around the world for quite some time now.
When it was active back then, its operators used to utilize its capabilities to steal information from over 60 applications. That’s how capable the variant was.
Once they inject Raccoon into devices, they can harvest very sensitive data, including cryptocurrency wallet accounts, login credentials, credit card information, browsing history, and cookies.
That’s not all. The Raccoon Stealer was available to everyone on hacking forums. Well, technically, to everyone who can shell out $200 a month.
Back in 2022, the FBI took down the then malware-as-a-service’s infrastructure. This came after the arrest of Raccoon’s primary author, Mark Sokolovsky, in the Netherlands.
Fast-forward some months into 2023, Raccoon found its way to hacking forums yet again, but with new and improved malicious capabilities.
Raccoon is Back – How Different Is It?
According to a post by VX-Underground, the team behind Raccoon decided to rebuild the malware’s entire infrastructure from scratch after Mike’s arrest. They also shared the group’s “Return” post on their X (Previously Twitter) account.
Cyberint cybersecurity firm assessed the new variant and what it can do. According to their report, Raccoon has introduced “quality of life” and OpSec adjustments, granting its operators more convenience.
That means it has become much easier and safer to use, giving new and less skilled threat actors the opportunity to try it out without having to worry about researchers and law enforcement.
The first adjustment comes in the form of a quick search tool. With it, the threat actors can easily find and gather all kinds of stolen information from huge databases.
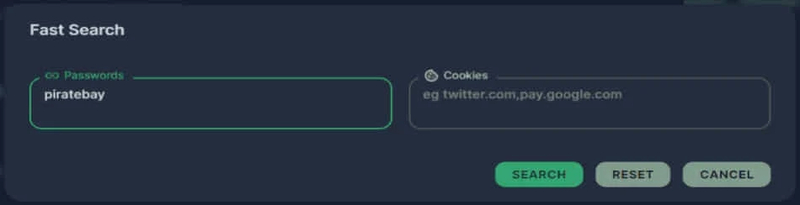

Another new feature would be the ability to block bots and spot unusual activity automatically. Raccoon is capable of deleting records instantly once irregular activities are found, making it more difficult for security tools to detect the malware’s presence.
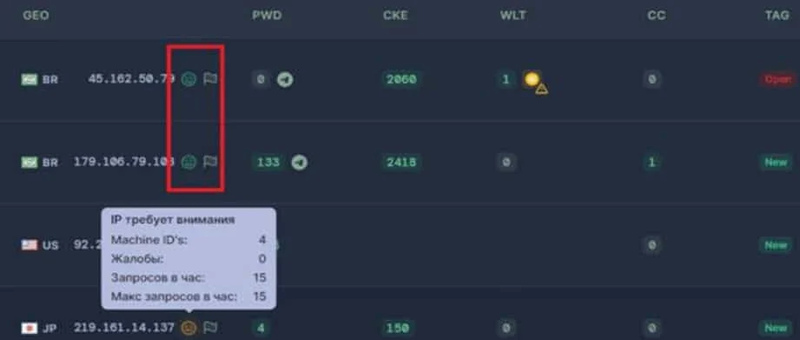

Finally, the malware has a system that records logs. Cybercriminals with Raccoon access can easily see successful breaches by country, number of breached devices, and more.
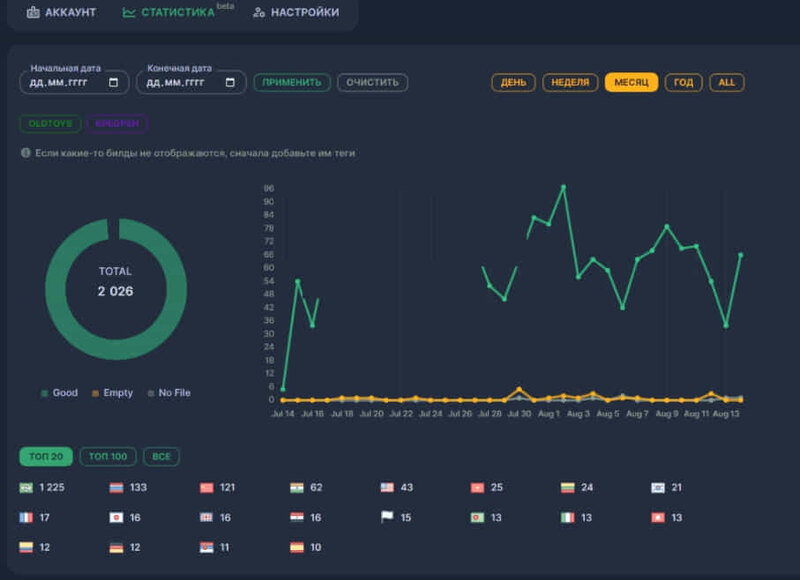

The Raccoon Stealer has been around for quite some time now, and it’s back with a vengeance. After a long time away, the group behind it has concocted a new variant with so many dangerous capabilities.
Be Careful – Your Sensitive Data is at Risk!
No matter what malware variant is out there, you should always remain vigilant when browsing the internet. Do not download random files, and do not trust third-party sources.
As for emails, make sure you don’t click on any link provided within. If it’s important, you can visit the source’s website manually. That’s your safest option.



