Raccoon and Vidar Stealers – SEO Poisoning Takes Over the World Wide Web


Cybercrime is achieved in various ways. Some use phishing emails, while others use fake websites to deploy any malware into their victims’ devices. However, one tactic search saw a huge rise in popularity – Search Engine Optimization (SEO) poisoning. Thanks to Raccoon and Vidar Stealers, we’ve all been reminded of the malicious practice.
Threat actors are using cracked software catalog websites that redirect their victims to pages where the payloads can be downloaded. This includes file-sharing platforms, such as GitHub.
Raccoon and Vidar stealers have been around in this campaign for almost three years, and the cybercriminals behind this don’t seem to be stopping any time soon. How is this executed, and what damage can be done? Here’s the full story.
Raccoon and Vidar – A New Level of Search Engine Leveraging
Cybercriminals have resorted to information stealers as a common tactic to infiltrate systems and harvest sensitive information from the infected host.
Over the years, multiple groups have used these stealers in different ways, be it malspam, fake installers, as well as phishing websites.
With the right social engineering capabilities, they can easily lure victims into downloading and executing the payloads. And that’s where everything goes south for the victim.
This time around, an unknown group is leveraging SEO to spread both Raccoon and Vidar info-stealers. It all begins with a basic search that leads to several malicious websites.
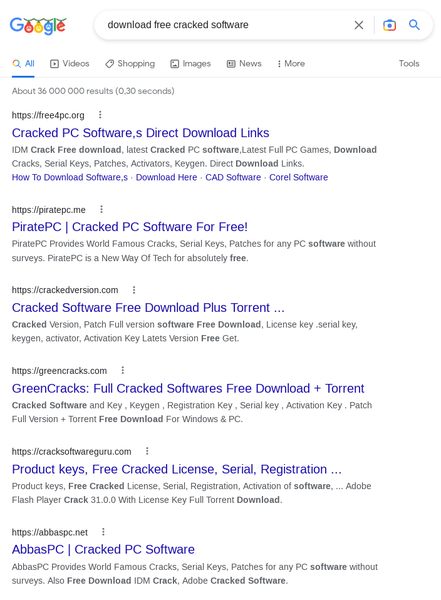

The campaign is executed in a brilliant way, which shows how capable the group behind it is. According to SEKOIA’s Threat & Detection Research Team:
“SEKOIA.IO analysts unveiled a large and resilient infrastructure used to distribute Raccoon and Vidar stealers, likely since early 2020.
The associated infection chain, leveraging this infrastructure of over 250 domains, uses about a hundred of fake cracked software catalogue websites that redirect to several links before downloading the payload hosted on file share platforms, such as GitHub.”
When the victims see top results that include their search queries, they’ll definitely fall for the trick and visit the recommended websites. There, they’ll be instructed to download the fake application.
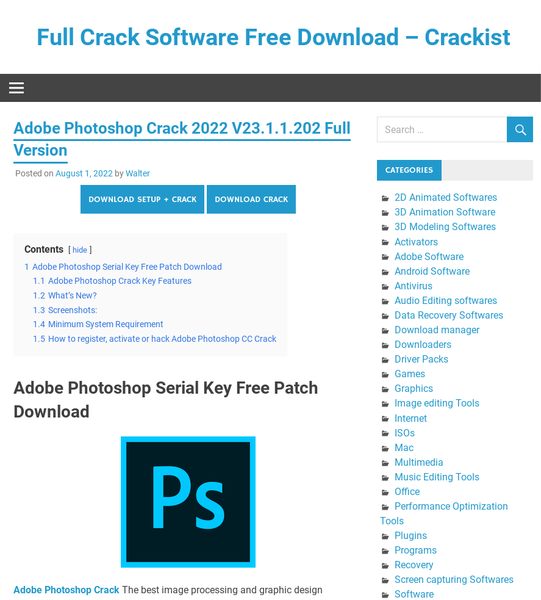

At the end of the page, victims can find tutorials demonstrating how to install the cracked version of the software. And finally, clicking on the download button will launch a new Window with further instructions. Here’s what the final page looks like before the download begins.
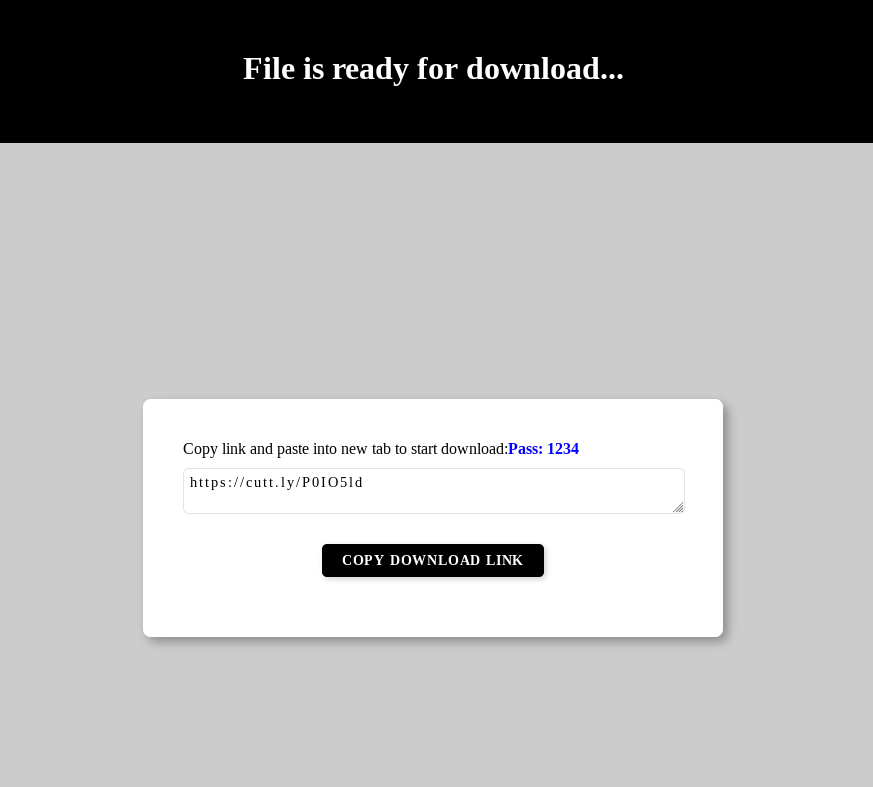

This shortened link points to a password-protected RAR archive file hosted on GitHub, along with its password. Now, when the victim uncompresses the RAR archive and runs the setup, either of the two malware families will take root within his/her system.
In the end, Raccoon and Vidar will siphon a wide range of personal information, steal credentials from web browsers, and exfiltrate data from various cryptocurrency wallets.
SEO Poisoning Campaign – Five Stages, One Outcome
According to the research team, there’s no known group behind this. However, the firm does state that more than a dozen accounts store malicious payloads on GitHub.
In other words, treat any website as if it’s a malicious one. Be always vigilant when it comes to downloading content through a web browser. Stay safe.



