It’s Smishing: Romanian Telecom Users Beware!


Phishing attacks are a common tactic among cybercriminals, and we’ve seen a rise in numbers throughout 2023. Of course, there are several types of phishing, and using text messages is a popular one. Speaking of, a new “Smishing” campaign is now targeting Romanian Telecom users.
Several smishing attacks have been discovered in the past couple of months, and this one is no different. Apparently, the attackers are using a fake page to trick users into submitting their credit card information.
The fake page replicates that of Posta Romana, and that alone is enough to fool anyone. But how are the threat actors implementing this attack? What’s at risk? Find out below.
The New Smishing Campaign – A Fake Romanian Telecom Account Update
When it comes to cybercrime, no company is safe! No matter what sector it covers, threat actors will target the desired company if deemed beneficial.
Even gaming companies like Activision have had their fair share of smishing attacks in the past, which solidifies our point.
Phishing begins with a link and ends with a travesty. If the victims follow the embedded URL, they’ll end up handing out their sensitive information willingly but unknowingly.
With Smishing, the entire campaign revolves around text messages (SMS Phishing), and that’s exactly what Romanian Telecom users are dealing with here.
The attack starts with SMS messages containing TinyURLs, which redirect victims to a clone version of the Posta Romana payment page.
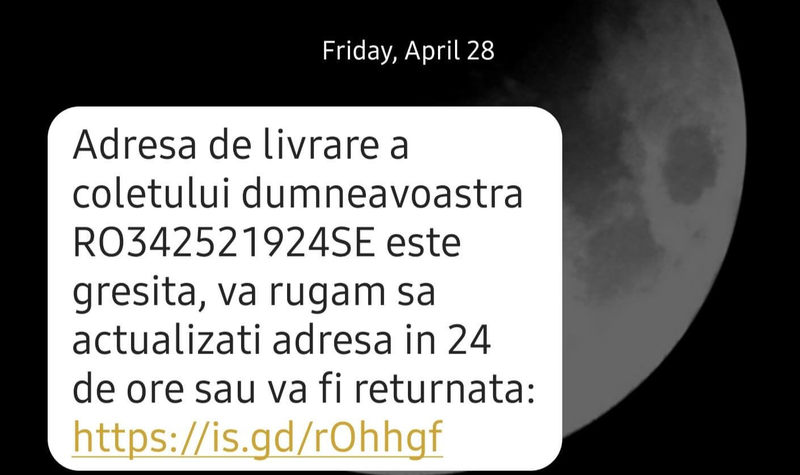

If we would translate this to English, the text message states the following: “The delivery address for your package RO342521924SE is not valid; please update your delivery address in 24 hours, or the package will be returned.”
This ignites a sense of urgency among receivers, which prompts them to click on the link immediately.
When the users follow the URL, their default browser will launch a fake page that asks them to submit their credit card information to cover a tax related to changing a delivery address.
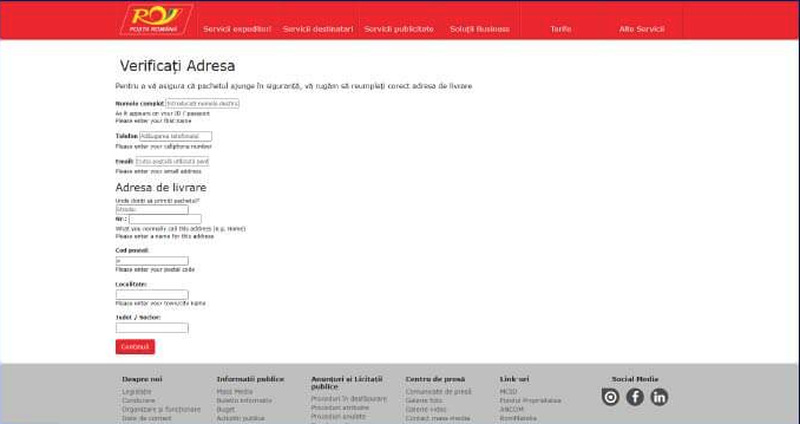

According to Heimdal Security, multiple tests were implemented to see how this page works. The findings were inconsistent in terms of end results.
The initial trial displayed a 403 error message after providing the requested information. However, that doesn’t mean that, in the background, the information wasn’t harvested.
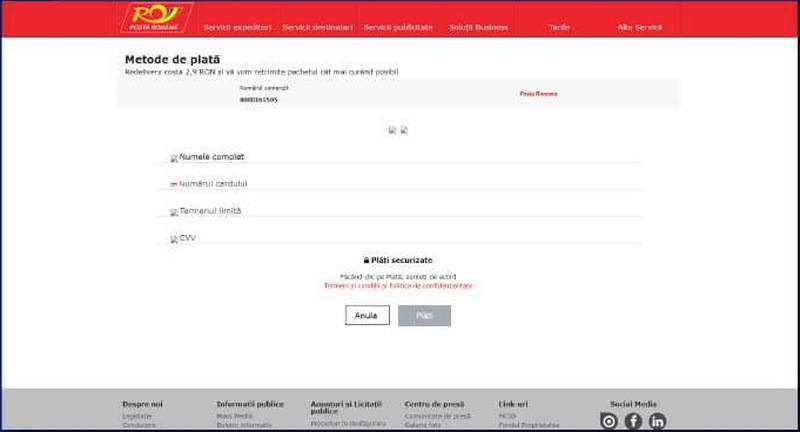

In another attempt, the fake page redirected to a blank page that showed no link to the official website. At the end of everything, submitting the credit card information is what the threat actors are looking for.
Remain Vigilant, Avoid Clicking Links
Whenever you’re browsing the web, you must always be aware of what you’re actually clicking on. Even Google Ads can take you to malicious places, as they’re present due to cybercriminal activities.
Just because it’s interesting or appealing, it doesn’t mean that it’s real. That’s exactly what threat actors prey on, so avoid clicking any link in an email or SMS.
Just visit the website manually. It might take a few seconds longer, but you’ll at least know that your data is completely safe.



