Purple Fox Malware – Telegram Poses a Risk to Desktop Users


Malicious installers containing malware have become sort of a thing in the world of desktop devices. With a simple click on a .exe file, things could take a turn to unwanted “cybercrime” places.
When the app is not known, many users might avoid putting themselves in such predicaments. However, when it’s one of the most popular messaging apps in the world – Telegram, the impact might be huge.
The malware is called Purple Fox, which as the name suggests, outfoxes the user and makes its way into desktop devices, and installs further malicious payloads once it infects them. This campaign is serious, and we’re going to be shedding more light on the matter in the following article.
The Purple Fox is Lurking
Desktop devices are always susceptible to such malicious practices as users can download almost anything on them.
When it comes to this Telegram Purple Fox malware campaign, all they have to do is download the package on their PC.
Once done, the Telegram Desktop.exe file drops two installers, which gives victims the option to choose between two installers. A legitimate Telegram installer and an AutoIT program (TextInputh.exe).
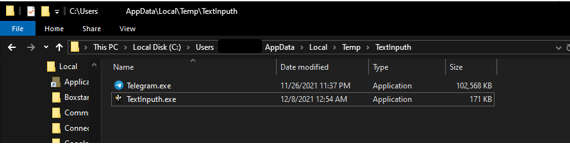

Unfortunately, while it may seem that the user is in control and has the privilege of choosing, it’s not like that in the background.
The AutoIT program does run the downloader regardless if anything is chosen, creating a new folder (“1640618495”) in “C:\Users\Public\Videos\” and connecting to the C2 to download a 7z utility and a RAR archive (1.rar) in the process.
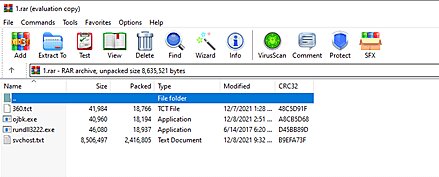

Now real malicious act begins. According to Minerva Labs, the TexInputh.exe file starts performing the following actions:
- Copies 360.tct with “360.dll” name, rundll3222.exe, and svchost.txt to the ProgramData folder.
- Executes ojbk.exe with the “ojbk.exe -a” command line.
- Deletes 1.rar and 7zz.exe and exits the process ojbk.exe.
It doesn’t stop here. Purple Fox has a lot to do to hide its presence. So, to block any 360 AV processes initiation and prevent its detection, the malware installs the following additional files:
- Calldriver.exe
- speedmem2.hg
- Driver.sys
- dll.dll
- kill.bat
Once everything is in place, the malware restarts the infected machine in order to apply the new registry settings. More importantly, it does that to disable the UAC (User Account Control).
When the UAC is disabled, rest assured that the malware now has full control over the device. It can now search and exfiltrate files, delete data, kill processes, download and run several codes, and worse, spread to other Windows systems.
Telegram Purple Fox Malware – Simple, but Dangerous
Impersonating legitimate applications to spread malware has become a common task among threat actors nowadays.
As of now, it’s not clear how the installer is being advertised or how the victims end up installing it. The most common ways to lure targets in are by using YouTube videos, forum spam, and shady software sites.
Not to mention pop-ups and ads that might bombard your browsing habits. Make sure not to download any app using any of these. Instead, head to the software’s official website and get it there. Stay safe.



