2FA Explained – What is Two-Factor Authentication and Do You Need It?


- 2FA explained
- Different types of authentification methods
- Why you must enable 2FA
- Top services that offer 2FA
How many times do you use your phone per day? According to Deloitte’s 2018 Global Mobile Consumer Survey, American consumers check their smartphones 52 times on average each day. Yes, that number might have the word addiction written all over it, but when you consider how many apps and accounts we have on our devices, the stats don’t sound so shocking anymore.
From social media platforms to streaming channels and banking services, our devices are packed with applications that keep us busy throughout the day. But more accounts bear more risks and troubles. That’s because they attract cybercriminals like bees to honey.
You see, most Internet services use the most basic and common form of authentification: Username and password. That means the latter is your only line of defense. If hackers manage to acquire it, they’ll have full access to your account and data.
And passwords are pretty easy to get. Even mediocre hackers can sweep them up. That’s why many online platforms are now introducing two-factor authentication (2FA), which adds an extra layer of protection.
Table of Content
- What Is 2FA?
- Types of Dual Authentification
- Why It’s Better to Enable 2FA
- Top Services That Support 2FA
- Final Thoughts
What Is Two-factor Authentification?
The majority of users rely on a single step for account authentification, and that’s passwords. And while having a password is much better than no protection at all, these codes are not exactly a secure fortress, especially when you take them for granted.
Cybersecurity experts advise us to regularly change our passwords to stay once step ahead of online criminals. They also instruct us to use strong passwords with symbols and capital letters. But long codes with various characters are difficult to remember, especially when you have several accounts.
Therefore, a lot of people tend to recycle passwords across multiple surfaces. More dangerous are those who use weak, easy-to-memorize codes like “123456” or “password.”
Nonetheless, even if you have a complicated password, you must always protect yourself and your data with an extra layer of security. Two-factor authentification or 2FA will provide that. It helps online platforms truly identify if one of their users is trying to gain access by adding another authenticity request.
The first step remains the same as you’ll have to submit your username/email and password. But instead of immediately gaining access to your account, you’ll have to provide a secondary piece of information to confirm your identity.
Types of Dual Authentification
As the name suggests, 2FA requires two steps of verification before you can access your account. The second factor comes from one of the three following categories:
- Something you know: It could be something like a PIN code, answers to secret questions like favorite color or pet name, a password, or keystroke pattern.
- Something you have: The second authentication factor can also include something that you possess. For example, it could be a smartphone, credit card, or hardware token.
- Something you are: This advanced category features something unique to you, like fingerprints, retina scans, or voice recognition.
Cybercriminals can get a hold of your passwords and other sensitive information through several sneaky ways. They can use phishing, brute force attacks, keylogging, or other forms of malware. Having a secure passcode with various letters and symbols may help, but it’s not enough to keep scammers at bay.
With 2FA, however, you’ll get a safety net in case your password gets stolen. Hackers will have to obtain another piece of information to access your account, which is highly unlikely. Now, there are several types of two-factor authentification, some more secure than others. But no matter which one you use, it’s still better than password protection alone.
SMS Verification


A lot of services use SMS text messages as a second means of authentification. After you log in to your account using your credentials (username and password), the site will send you an SMS that contains a one-time-use code. Then, you’ll have to type in the code back into the service to access your account.
That way, even if scammers manage to steal your password, they’ll need the code on your phone to hack into your account. And while this may sound like a reasonably secure method, hackers can still infiltrate your files and data.
For example, they can steal personal information like your social security number, and impersonate you to order a new SIM card. The telecom company will think that you’re making the order because you lost your SIM or because you bought a new phone.
And just like that, cybercriminals will receive all incoming calls and SMS texts, including the authentification code. The attack is called SIM Swap, and hackers have been using it to steal victims’ money or make purchases on their behalf.
Nonetheless, SMS verification is still better than no 2FA at all.
Email Code Authentification
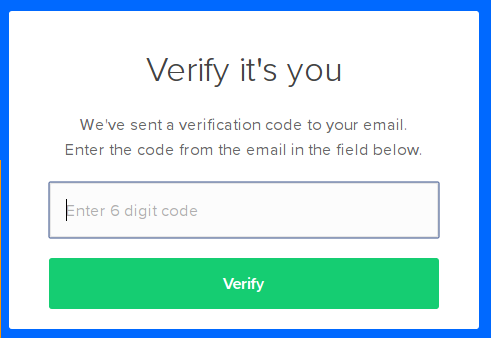

While some online platforms send the secondary authentification code via SMS, others prefer to use your email address. The process is similar to the SMS verification method, as you’ll first identify yourself through your username and password.
The service will then send a one-time-use code to your email, and you’ll have to submit it to enter your account. That makes it harder for hackers to steal your information as they’ll need access to your email address as well as your password.
However, this method is not the best in terms of security, as your email is subject to attacks and hacking attempts.
Hardware Tokens and Physical Devices
Physical authentification tools are very popular among big tech and financial companies. Instead of using SMS or email verification codes, users will get a USB key that they insert into the computer whenever they log in to their accounts. Then, they press the button on the USB, and the service will know it’s them.
There’s no need for entering codes or passwords when you use physical keys. Moreover, you can attach them to your keychain to keep them around you at all times.
Other hardware tokens cannot be inserted into USB ports. Instead, they produce a new numeric code every 30 seconds. Whenever you wish to access your account, you enter the code that’s on display and Eureka! You’re in. Other devices use NFC and Bluetooth technology for authentification.
The problem with tokens and USB keys is that they can be costly, especially for big companies with hundreds of employees. Furthermore, they are easy to misplace. They are more secure than one-time-use codes, though, as they can’t be intercepted. Even malicious phishing websites that scammers create won’t be able to steal your credentials.
2FA Apps


One-time-use codes are very common as second-factor authentification. But you don’t just receive them via SMS or email. Specialized 2FA apps can also produce them, and you can install these applications on your smartphone or desktop. And you can use them with any site that supports 2FA code verification.
These apps generate rotating passwords that are valid for less than a minute. Once you link them to your account, the “authenticator” app will display a code that you can input after you type in your credentials. The most widely-known application of this kind is Google Authenticator.
This method reduces hacking threats since everything is completed on the same device. Furthermore, you can use them at any time and in any place. They are compatible with smartphones, computers, and in some cases, wearables. Authenticator apps even work offline.
Push Notification
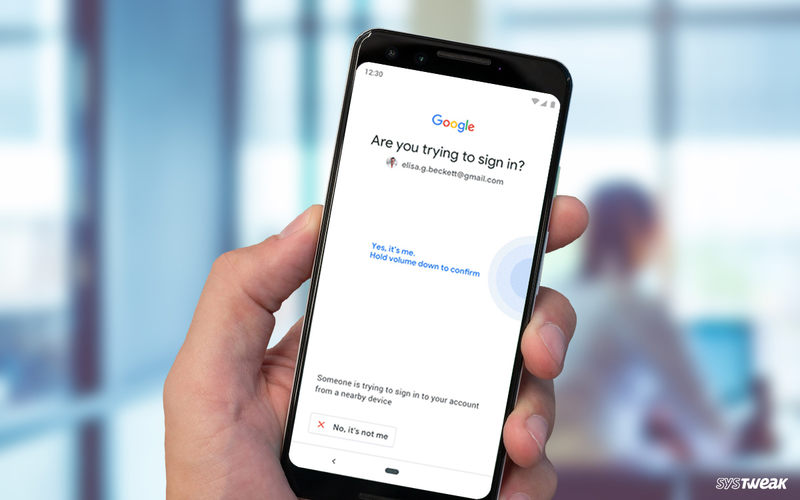

Two-factor authentification sometimes doesn’t even require any codes or devices. A lot of services now have 2FA using their own apps. For example, if you try to open your Gmail on a new device, Google will send a push notification to your phone. This codeless verification method notifies you that someone is trying to access your email from an unknown source.
You can choose to accept the action if you’re the one logging in from a new device or decline if someone else is hacking to your account. Other websites also offer 2FA push notifications, including Microsoft, Apple, and Twitter. The direct connection between the service, device, and 2FA removes a lot of threats like phishing and man-in-the-middle attacks.
However, push notifications require an Internet connection. Otherwise, they won’t work.
Biometric Authentification


Perhaps the best way to verify that you’re the one who is trying to access your account is through biometrics. This method would also drastically reduce hacking attacks on the services that implement this technology. And while it is still restricted to unlocking phones, laptops, and computers, it seems that biometric 2FA will soon be upon us.
Biometric two-factor authentification relies on your unique human characteristics. That includes fingerprints, retina scans, and voice and facial recognition. In other words, scammers will need your eye, finger, face, or voice to access your device without your knowledge, which is impossible.
However, this technology must be perfected before web services can implement it. The program must be able to accurately identify users and notice the difference between them and cybercriminals. Furthermore, some biometrics like facial recognition won’t work if you wear lenses or, in some cases, wear makeup.
Why It’s Better to Enable Two-factor Authentification
As I mentioned earlier, passwords alone are no match for the advanced cyber-attacks that are happening these days. Even strong passwords like the ones password generators produce can’t protect you. That’s because hackers have programs that can run through millions of combinations per second until they find your login details.
And sometimes we don’t make it that hard for them either. For example, we use the same password across all our accounts or create predictable codes based on our pet’s name or birthday. You don’t have to be the world’s greatest detective to unravel such information. We share it with the rest of the world via Facebook, Twitter, Instagram, Snapchat, and who knows what else.
So as you can see, cybercriminals can find a lot of ways to get their hands on your password. Therefore, it’s up to us to make things a little more challenging by implementing another step/factor of verification. You’ll add another layer of protection to your bank and social media accounts, no matter which two-factor authentification category you use.
Now, does 2FA mean hackproof? Of course not. Advanced and determined hackers may still gain unauthorized entry, especially if you use one-time-use codes that are easily intercepted. But you’ll have a better chance to protect your account, or at least discover that you were hacked.
Yes, 2FA requires that you make one more step before you can access your account. But I wouldn’t call that a hassle. After all, it’s your data/money/sensitive information that’s on the line, so don’t take this matter lightly. Take my advice and enable 2FA on every service that offers this feature. It’s better to be safe than sorry.
Top Services That Support 2FA
A lot of services now use two-factor authentification to protect user accounts, especially top financial and tech companies. 2FA can significantly reduce data breach attempts by providing you with another layer of verification. You may find that extra step a bit annoying as we all like to access our accounts ASAP.
However, the additional process will only take moments of your time. And you’re better off enabling it as a precautionary measure than after you fall victim to a scam or hack. You’ll find below the top services that provide two-factor authentification and how to activate it.
Emails, documents, messages, and even payment information are part of Google. Therefore, protecting your account with 2FA is crucial. Google calls it 2-Step Verification, and it offers you three options as means of authentification: Phone Prompt (push notification), SMS or call, and security key.
Step one: Setting up Google 2FA
- Sign in to your Google account.
- Then, go to “Security” from the navigation panel on the left of the screen.

- Click “2-Step Verification,” followed by “Get Started.”

- Choose one of the three authentification options (Prompt, SMS/call, security key).

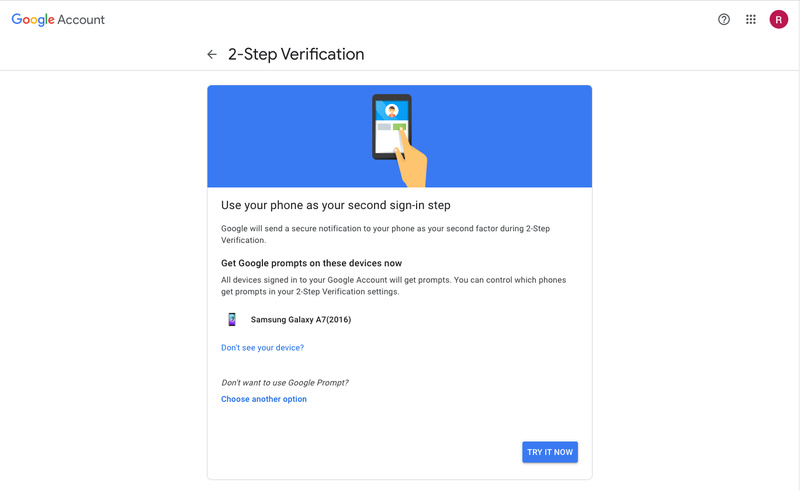
Step two: Backups
Google allows you to set up backups to your accounts in case you forget your password or lose your phone.
- Go to your Google account.
- Tap “Security” (on the left navigation panel).
- Click “2-Step Verification.”
- Add at least one additional second step:
- Backup codes
- Authenticator app codes
- Backup phone
Step three: Recovery information
Always provide updated recovery information to get your account back if you forget your password.
- Sign in to your Google account.
- From the navigation panel, click “Personal Info.”
- Under “Contact Info,” tap email and/or phone.
- Add or update your recovery email or phone number.
Your Facebook profile contains posts, photos, videos, and other files that are over a decade long. It would be a shame if someone infiltrated your account and deleted or stole them. What’s even scarier is if someone impersonated you and posted or chatted on your behalf without authorization.
You can minimize that danger by activating Facebook’s two-factor authentification. That way, hackers will have another security barrier to cross before they can access your profile. All you have to do is log in to your Facebook and go to “Settings.”
From there, click on “Security and Login” from the navigation panel, followed by “use two-factor authentification” under “Two-Factor Authentification.”
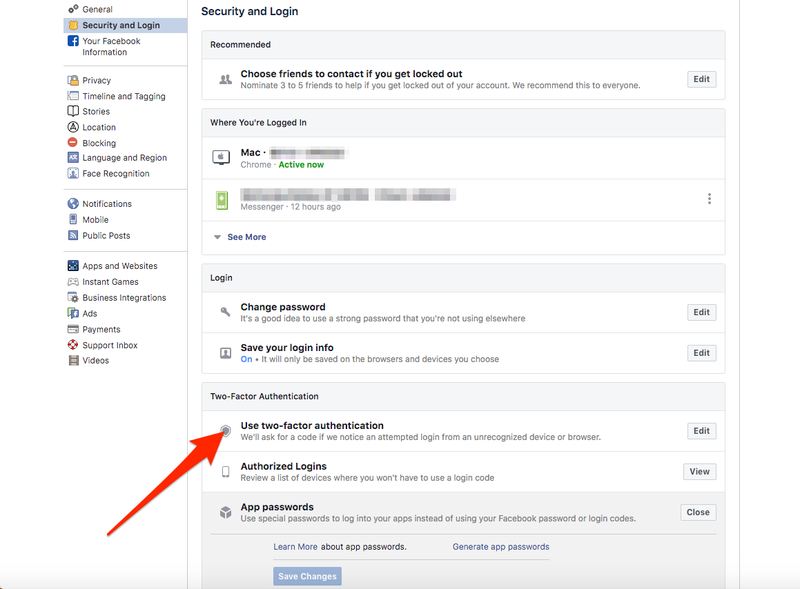

Next, choose one of two security methods: Authentication app (recommended) or text message (SMS).
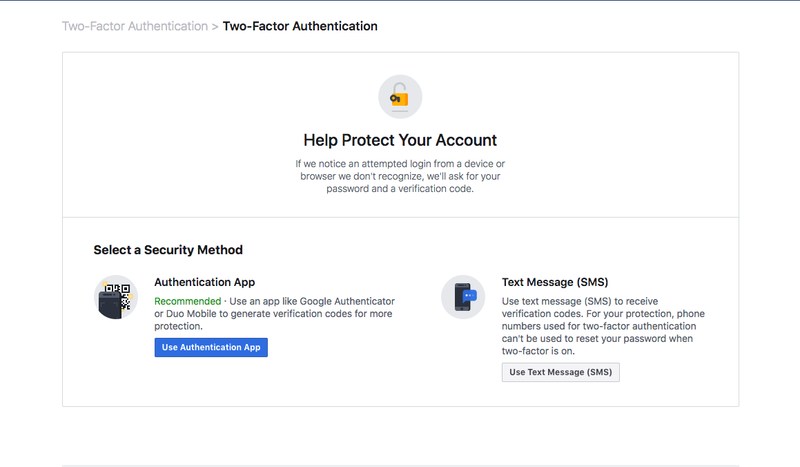

You can also activate 2FA through the Facebook app on your phone or tablet. The process is similar to the desktop client. Just go to Settings & Privacy > Settings > Security and login > Use two-factor authentification > Select a security method.
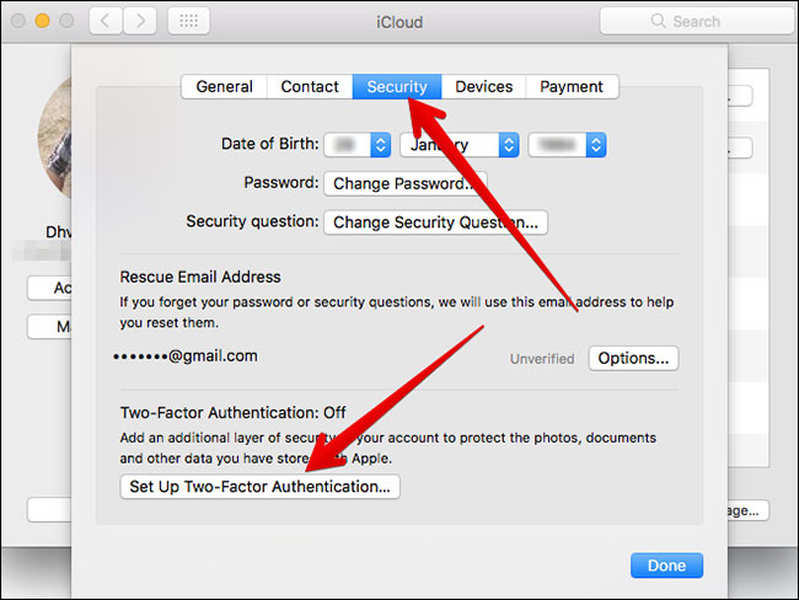
Apple
If you’re an iPhone, iPad, or Mac user, then I’m sure you have a massive appreciation for your Apple ID. It allows you to access the App Store to install or buy apps, as well as make purchases on iTunes and Apple books, not to mention iCloud storage.
That means cybercriminals can do a lot of damage if they break into your Apple account. Therefore, protecting it with just a username and password is nowhere near enough. Apple allows you to add another authentification step for better security. That way, you’ll make it harder for hackers to access it.
The Apple 2FA is only available for users on iOS 9 or macOS X El Capitan or later. to enable it, just follow these steps:
On iOS
- Go to Settings > [your name]. For iOS 10.2 users or earlier, go to Settings > iCloud and tap your Apple ID.
- Click “Password & Security,” then enter your Apple ID password.
- Tap “Turn On Two-Factor Authentication.”
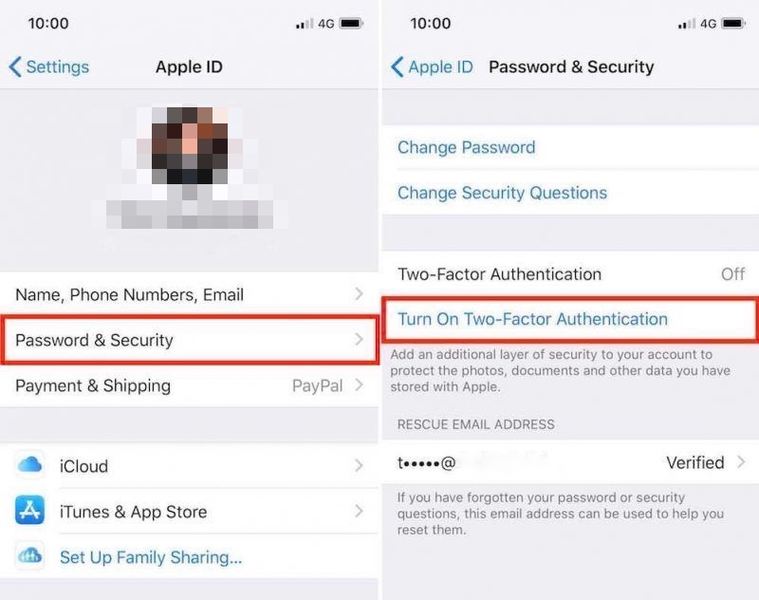

On macOS
- Go to the Apple menu () (top left of the screen) > “System Preferences.”
- Click “iCloud” > click “Account Details.” Then, enter your Apple ID password.
- Tap “Security.”
- Hit “Turn On Two-Factor Authentication.”

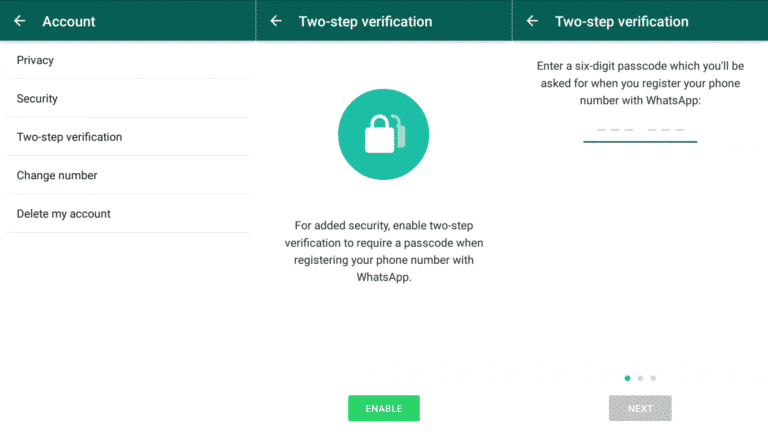
Facebook recently announced that WhatsApp now has two billion users. The social media platform bought the messaging service in 2014 for a whopping $19 billion. And the reason behind WhatsApp’s global popularity is because the app is user and privacy-friendly.
It added end-to-end encryption to all its messages in 2016, including texts, voice notes, photos, videos, and VoIP calls. But that’s the only feature that was introduced. WhatsApp also offers two-step verification, allowing you to enhance your security and privacy further.
Setting it up is easy, and it’s the same process through the app and desktop client. Go to Settings > Account > Two-step Verification. Next, tap “Enable” and create a six-digit PIN for which you’ll be asked for when you register your phone number with WhatsApp. The app will also ask for your email address in case you want to turn the verification.
Therefore, if you sign out of WhatsApp or log in using a new device, the app will send you a code, and you’ll have to re-enter the PIN as well.

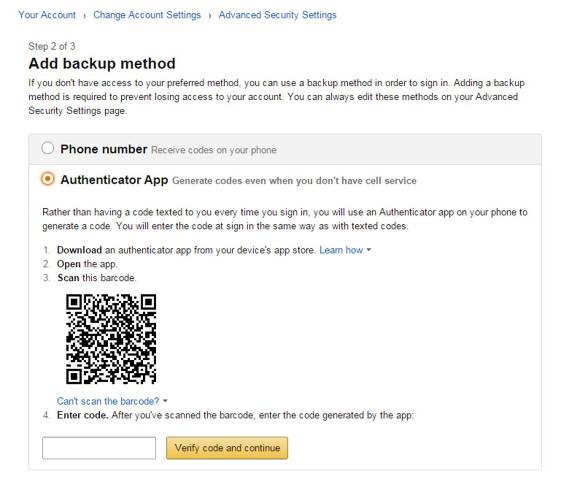
Amazon
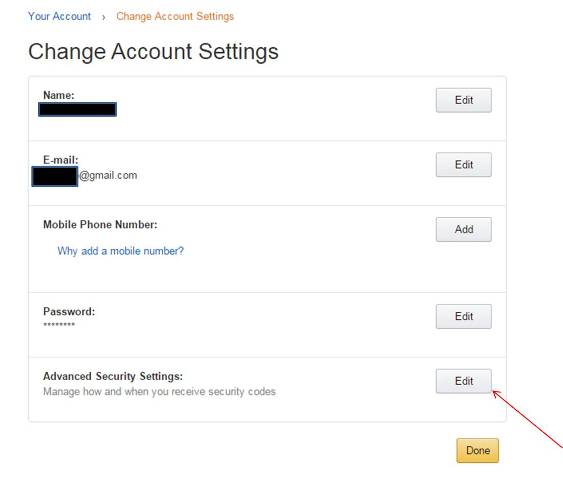
A lot of stores and online shopping websites use Amazon Pay, and all of them are tied to your credit card. Therefore, to better protect your financial accounts and transactions, you must activate two-step verification.
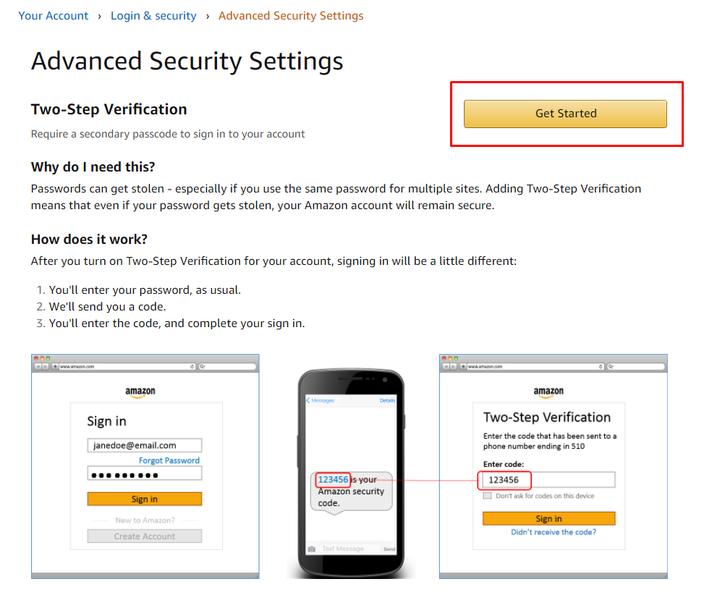
To do so, hover the cursor over Accounts & Lists and click Your Account from the drop-down menu. Then, click the Login & Security box at the top of the page, followed by the Edit button on Advanced Security Settings. Now, press Get Started and choose between two security options: Text message SMS) or authenticator app (scan the QR code).
Amazon iOS and Android users can activate 2FA by pressing the hamburger menu icon on the left of the screen, followed by Account > Login & Security. Then, follow the same Advanced Security Settings process as the above.

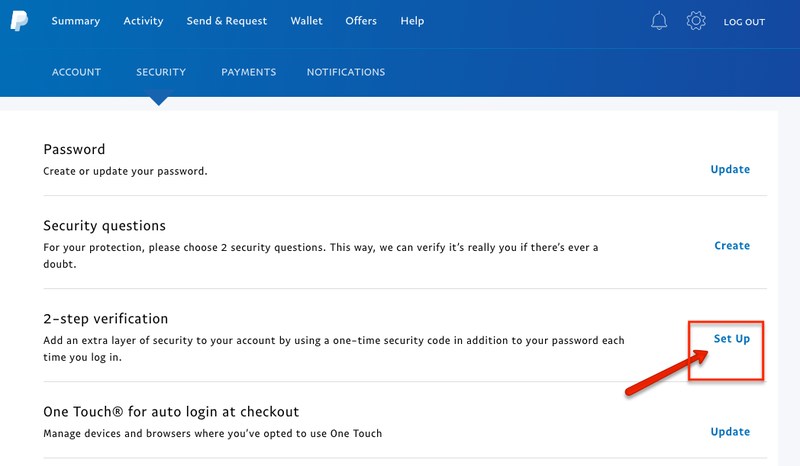
PayPal
PayPal is an online payment system that allows you to send/receive money transfers and make purchases over the Internet. In other words, your account must be as secure as possible. That is why PayPal provides two-factor authentification, “making it more difficult for unauthorized users to access your gateway.”
“When you enable 2FA on your Control Panel account, you will be required to enter both your normal password and a different code each time you sign in.”
PayPal
To enable 2FA on PayPal, follow the below steps:
- Log in to your account.
- Click the gear icon on top of the page.
- Hit the “Security” tab, followed by “Set Up” next to “2-step verification.”
- Then, choose how you want to receive the code (via authenticator app or SMS).

What Is 2FA and Why You Should Use It? – Final Words
Cybercrime is on the rise and costing damages worth billions of dollars each year. Hackers are coming up with new ways to take down the strongest of defenses, so they shouldn’t find much trouble breaking into your account. As a result, you must make things harder for them by enabling two-factor authentification.
2FA will add another layer of protection to your accounts, whether via codes, physical tokens, or push notification. And with major tech companies working to perfect biometrics, we could have a much more secure 2FA method on our hands soon.
Do you enable 2FA on all your accounts? Share your experience in the comment box below.






2 Comments