BRATA Android Malware – Extra Capabilities for a Better Malicious Outcome


When it comes to malware, the stealthier it is, the more damage it does. Threat actors, throughout the years, have developed new techniques to commit their malicious practices. And now, the attackers behind the BRATA Android malware came up with some of their own.
When certain malware operators have been around for quite some time, they’re bound to enhance the material they work with. For example, Hello XD ransomware was just a typical campaign. However, its operators managed to add a “Backdoor” feature, which elevated the ransomware’s capabilities.
BRATA, on the other hand, got a major boost as it can now perform its attacks against financial apps in a stealthier matter. How is BRATA operating now? What techniques has it mastered? Give this article a quick read and find out.
BRATA – With Great Stealth, Comes Great Capability
It’s not a new form of attack that sees a certain piece of malware go international within a couple of years. BRATA, aka Brazilian Remote Access Tool Android, first saw the light in Brazil back in 2018.
The banking trojan then went global and reached Europe in the form of antivirus software and other productivity tools, which of course, are fake to trick users into downloading them.
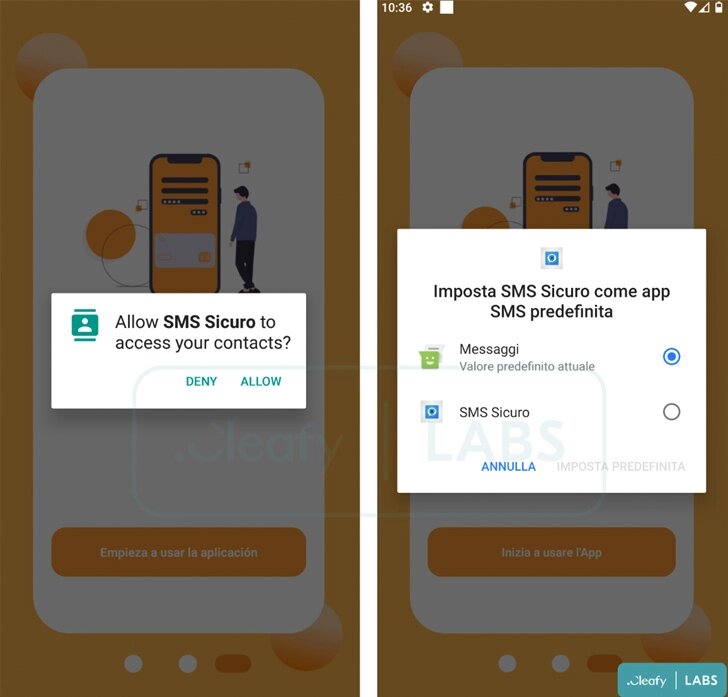

Now, it has changed the way it approaches its victims. By limiting the attack to a specific financial institution at a time, the percentage of success reaches a new high.
They only change the target’s bank once the victim suspects an intrusion and implement consistent countermeasures to stop it.
As seen in the image above, the malware campaign impersonates the login page of the financial institution to collect credentials, intercept SMS messages, and sideload a second-stage payload (“unrar.jar”). The attacker uses a remote server to save any events on the compromised device.
Cleafy Comes to Clarify
The researchers at Italian cybersecurity firm Cleafy explained the entire operation of the malware group in terms of intentions as well as the shift from apps to specific banks:
“The first campaigns of malware were distributed through fake antivirus or other common apps, while during the campaigns the malware is taking the turn of an APT attack against the customer of a specific Italian bank.
They usually focus on delivering malicious applications targeted to a specific bank for a couple of months, and then moving to another target.
The combination of the phishing page with the possibility to receive and read the victim’s sms could be used to perform a complete Account Takeover (ATO) attack.”
There you have it. Malware operations can take a whole new form and capabilities in no time. In other words, be careful when you download an app. You never know what malicious actor is behind it.
The threat actors have distributed several apps that include malware. One of them is an SMS securer that is, in reality, an interceptor to harvest everything your send or receive.
BRATA – From Brazil with Maliciousness
The lesson here today is that threat actors can further improve the capabilities of their piece of malware and pose bigger threats. As they grow, the damage they cause grows with them.
Most of their attacks come from phishing campaigns, so you have the chance to avoid this entire predicament. Don’t click on random links, don’t download apps from unknown sources, and of course, install a reputable antivirus program.



