From Shagle to Telegram – Trojanizing at Its Best


Impersonating big social media names to perform malicious activities is a popular tactic among cybercriminals. In the past, the likes of Instagram and Twitter were used to spread malware and ransomware. Now, threat actors are using the video chat service Shagle to target users with a trojanized version of the Telegram app.
While it might seem very strange, the campaign is definitely effective in terms of what the cybercriminals get out of it.
It all starts with a fake website, followed by an APK download. After that, it gets worse, as the advanced persistent threat (APT) group known as StrongPity will have complete control. We’ll dive into the details in the following article.
Telegram Trojan – A Backdoor Takes Root
As we mentioned, using social media applications as disguises to spread malware is pretty common nowadays.
In fact, 2022 had its fair share of impersonation attempts. We’ve seen campaigns that included both Twitter and Instagram.
Not only that, even Telegram was used in a campaign that targeted Windows users with the Purple Fox malware. Once they download the installer and run it, the threat actors will gain full control of the device.
We’re talking about major privileges like collecting SMS texts, monitoring phone calls, and stealing contact information. This can even lead to more malware injections.
Now, Telegram is back in the spotlight. However, Android users are the primary target this time around. It all starts with a fake page promoting the widely popular video app – Shagle.
Users probably end up on the page via smishing (SMS phishing), phishing emails, or instant messages on online platforms.
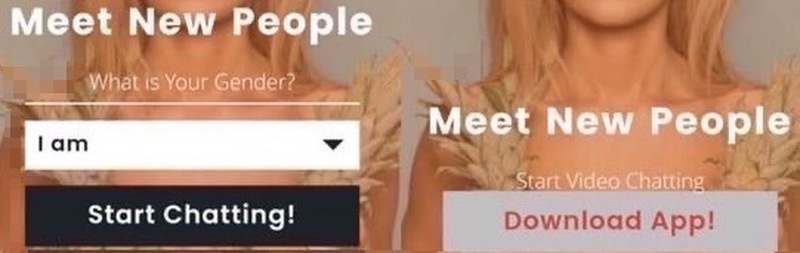

In case it’s not known, Shagle is a platform that’s only available via web browsers. So, this might seem a bit weird for users who are already familiar with the service.
Those who are not can easily be tricked into clicking on the “Download App!” button. Once they do, a file called “video.apk,” a modified version of Telegram v7.5.0 will be downloaded.
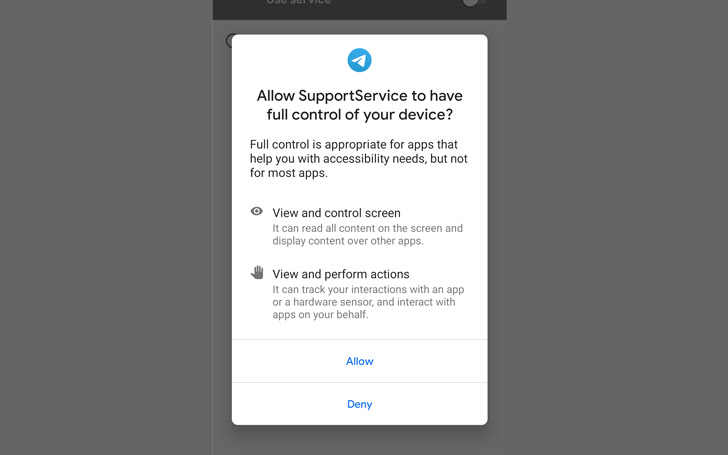
The APK will install a Telegram replica that will ask for crucial permissions when launched. In fact, it’ll literally state that it’s going to take full control.

Those who already have the Telegram application will be met with a failure notice. It’ll state that the application was not installed, which means the backdoor did not take root. In other words, they’re safe.
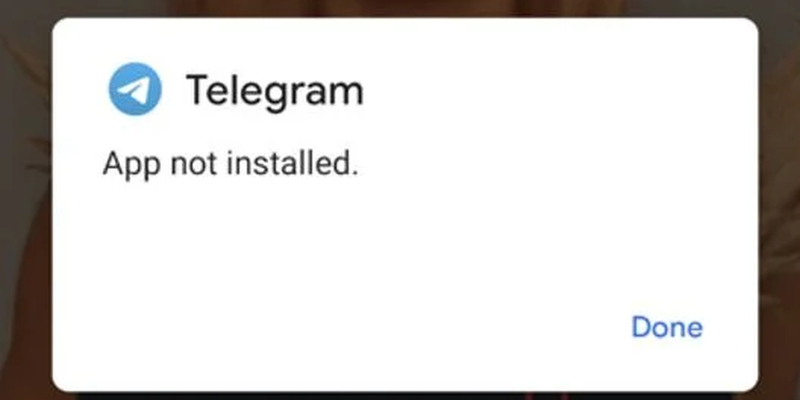

Those who receive this message are the fortunate ones since they have avoided a huge infiltration problem. In other words, having Telegram can save you from this predicament.
The Unfortunate Ones
Sadly, the ones that don’t have Telegram and proceeded with the process will have a backdoor installed on their device that can perform various malicious functionalities:
- libarm.jar – records phone calls
- libmpeg4.jar – collects text of incoming notification messages from 17 apps
- local.jar – collects file list (file tree) on the device
- phone.jar – misuses accessibility services to spy on messaging apps by exfiltrating contact name, chat message, and date
- resources.jar – collects SMS messages stored on the device
- services.jar – obtains device location
- systemui.jar – collects device and system information
- timer.jar – collects a list of installed apps
- toolkit.jar – collects contact list
- watchkit.jar – collects a list of device accounts
- wearkit.jar – collects a list of call logs
ESET researchers identified this active campaign and have attributed it to the StrongPity APT group. According to their statement:
“StrongPity’s backdoor is modular, where all necessary binary modules are encrypted using AES and downloaded from its C&C server, and has various spying features.”
This particular criminal group has been around since 2012, spreading its malicious activities across multiple platforms using backdoors. They’re dangerous, and they’re capable.
StrongPity Strikes – The Perfect Social Disguise
Android devices are very susceptible to such attacks since their operating systems allow any kind of file download. If you have an Android, make sure you get your files and downloads from trusted sources.
Always handle APKs with complete caution. You never know who’s the website’s host or what they’re after. Finally, pay close attention to the permissions the applications ask for. This can be an indication that something malicious is lurking within.



