Android Malware Alert – Google Play Slips Up Once More


We have no idea what is wrong with Google Play Store lately. In the past couple of months, malware has been able to bypass its security measures through various applications. And now, the impact is bigger than ever as apps with over 10 million downloads are spreading Android malware through the store, yet again.
Google might be the most secure source for downloading apps, but it definitely doesn’t come without flaws. We do trust the app hosting giant. However, such a privilege is fading away courtesy of Google Play’s constant slip-ups.
With the ability to push intrusive ads, subscribe users to premium services, and steal victims’ social media accounts, these malicious applications can do serious damage. What apps are we referring to? How is this entire campaign operating? Find out below.
10 Million Downloads – A Scary Number for Android Malware
Threat actors have been elevating their techniques and it’s obvious due to their numerous successful Google Play Store infiltrations. No, this time around, no one is impersonating Play Store.
Somehow, someway, attackers are spreading apps within Google Play Store’s library, bypassing every single security measure the app giant has in place.
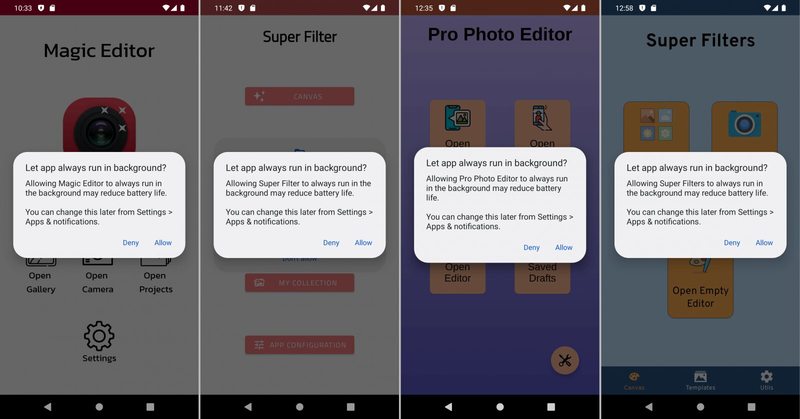
The malicious apps in this campaign come in different forms and have different functionalities. According to a report by Dr. Web security firm, the apps fall into categories such as image-editing tools, virtual keyboards, system optimizers, wallpaper changers, and more.
As with various malicious apps, the key to a successful malware injection is through claiming permissions. Once the victims install the apps, they’ll request permission to overlay windows over any app.
As a result, they’ll be able to can add themselves to the battery saver’s exclusion list. But the question is why? Well, it’s pretty simple. The attackers don’t want the user to close the app. By including the software in “battery saving,” it’ll proceed with its operations in the background.

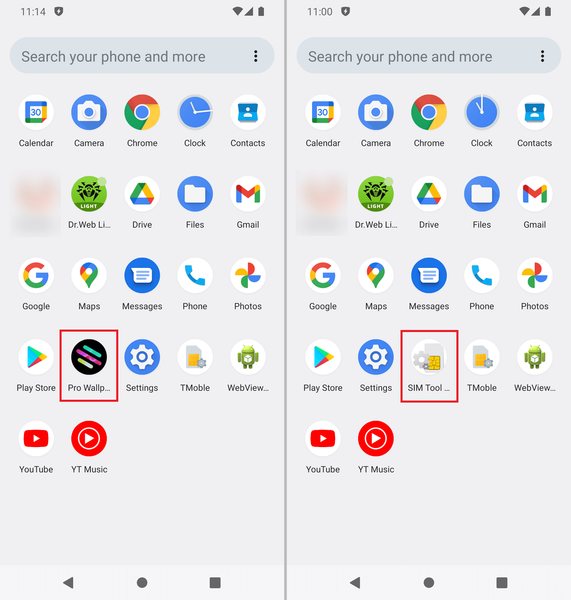
Aside from that, the apps try their best not to be discovered by the user if he/she wanted to delete/uninstall them. To do so, they hide their icons from the app drawer or disguise themselves are a core system application such as SIM Toolkit.

As we mentioned, these applications can do a lot of damage to the victim’s device. For example, “Neon Theme Keyboard,” the app that harnessed over a million downloads despite the low rating score and many negative reviews, can literally kill a device.
Users wouldn’t be able to enter their passwords to unlock the phone and uninstall it. To get rid of the app, a factory reset was needed.
The Malicious Apps
Do we have a list of the infected apps? Of course, we do. Here are the apps found hosting malware on Google Play Store:
- Photo Editor: Beauty Filter
- Photo Filters & Effects
- Emoji Keyboard: Stickers & GIF
- Neon Theme Keyboard
- Photo Editor: Retouch & Cutout
- Photo Editor: Art Filters
- Neon Theme – Android Keyboard
- Cashe Cleaner
- Fancy Charging
- FastCleaner: Cashe Cleaner
- Call Skins – Caller Themes
- Funny Caller
- CallMe Phone Themes
- InCall: Contact Background
- MyCall – Call Personalization
- Caller Theme
- Photo Editor & Background Eraser
- Photo & Exif Editor
- Caller Theme
- Photo Editor : Blur Image
- Photo Editor : Cut, Paste
- Funny Wallpapers – Live Screen
- 4K Wallpapers Auto Changer
- NewScrean: 4D Wallpapers
- Stock Wallpapers & Backgrounds
- Photo Editor – Design Maker
- Photo Editor – Filters Effects
- Notes – reminders and lists
Most of these apps have been removed from Google Play Store’s library. However, as of July 26th, 2022, three applications remain available for download and installation via the Play Store.
Google Does it Again – Android Malware Made Official
Google Play Store is the only trusted source for downloading Android applications. However, we’re starting to question this as too many malicious campaigns have been able to bypass its security measures.
To avoid such a predicament, always take a look at what other users have left in the review section. Make sure to check every little detail – it can change everything.



