Blind Eagle Emerges: A Well-Orchestrated NJRAT Attack Chain


Cyberattacks are rising in terms of numbers, and there’s no indication that they’re stopping any time soon. All over the world, threat actors have been elevating their techniques to guarantee higher success rates, and they’re succeeding. Speaking of elevation, Blind Eagle resurfaced with a new attack chain involving NjRAT.
In this new campaign, the cyber-espionage group has been targeting multiple countries at the same time. Those include the likes of Ecuador, Chile, and Spain.
Blind Eagle has been around for quite some time now, and we know what this group is capable of. This attack is big, and we’re here to share everything we know about it so far.
Blind Eagle – Attack Elevation at Its Best
The cybercrime universe has no shortage of malicious groups out to get any kind of data they manage to stumble upon.
These groups vary, and so do the methods used to perform these activities. Whether it’s phishing attacks, malware injection, or even ransomware – there’s always a beneficial goal at the end of the line.
Blind Eagle, a cyber-espionage group, has been terrorizing companies in the Colombian region for quite some time now, especially institutions that fall into the “Governmental” department.
Not only that, but they also target corporations in the financial sector, the petroleum industry, and professional manufacturing. The group also goes by the alias APT-C-36 and is suspected of having originated from South America since at least 2018.
The group is known for using a variety of sophisticated attack methods. In most cases, Blind Eagle uses spear-phishing.
In fact, both Check Point and BlackBerry released reports documenting the group’s activity as it used this tactic to deliver malware families like BitRAT and AsyncRAT.
However, throughout the years, security firms have indicated that it also focuses on custom malware and social engineering tactics, as well as using exploits for zero-day vulnerabilities in their attacks.
This time around, the attack chain includes the use of a JavaScript downloader to execute a PowerShell script through Discord CDN.
This also drops another PowerShell script and a Windows batch file within the Windows startup folder. Not only that, but it also saves a VBScript file in the folder to achieve persistence, as reported by ThreatMon.
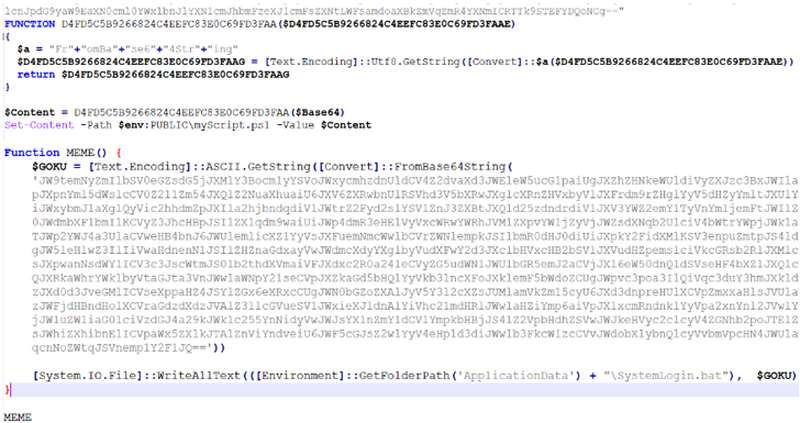

Once everything is set and takes root, the PowerShell script executes njRAT (Bladabindi), which has the capability to give the threat actors full control of the victims’ computers.
Another Cyberattack – njRAT Takes Over
Blind Eagle poses a big threat to any company or institution out there. It is definitely a financially motivated threat group, and it uses very effective tools to fulfill its tasks.
Earlier this year, Blind Eagle launched a huge campaign targeting Ecuador-based entities with a very complex toolkit. This shows that this particular group can do it all with ease.
When it comes to cybercrime, companies/organizations should implement the necessary precautions in order to prevent any infiltration attempt. And so should you! Stay safe.



