A New Spear Phishing Attack – Users Drowning in MuddyWater


Throughout the years, multiple cybercriminal groups have emerged with new tactics to infiltrate systems. Some are old, and some are new, but one group stands out as it gets innovative every time it decides to strike. Yes, we’re talking about MuddyWater.
A lot of threat actors prefer using popular brands such as Instagram for their phishing schemes. However, the Iranian group is using already compromised corporate email accounts to send fake emails containing fake Dropbox links or document attachments.
So far, the research indicates that MuddyWater is targeting countries in the MENA region and Central/West Asia. How big is this phishing campaign? How is MuddyWater pulling it off? Here’s everything we know.
MuddyWater – Multiple Names, Same Malicious Outcome
As we mentioned, there are several malicious groups that prefer using phishing schemes in their practices. However, none of them have as many aliases as MuddyWater does.
Yes, you might encounter a group with a name or two, give or take, but this one has literally around seven. If it’s not tracked as MuddyWater, it’ll strike victims as Mercury, Seedworm, Boggy Serpens, Cobalt Ulster, Earth Vetala, Static Kitten, or TEMP.Zagros.
MuddyWater saw the light back in 2017 with a few targets in sight. These include telecommunications, government, defense, and oil sectors.
Just like most phishing campaigns, this one kicks off with a fake email containing a link that the victims are prompted to click on.
And since the attack targets countries such as Oman, Qatar, Armenia, Iraq, Israel, Jordan, Azerbaijan, Egypt, Tajikistan, and the UAE, the emails are either in English or Arabic.
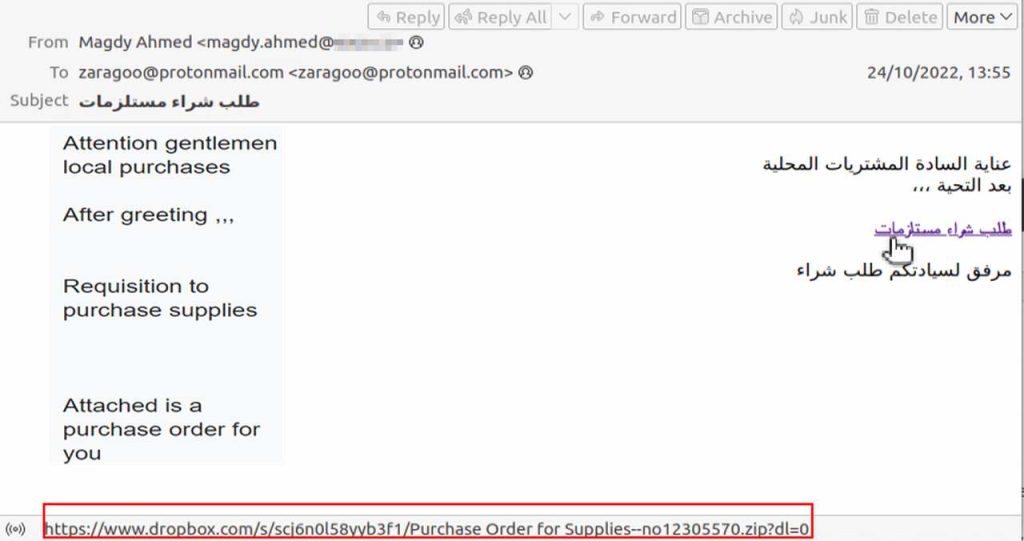

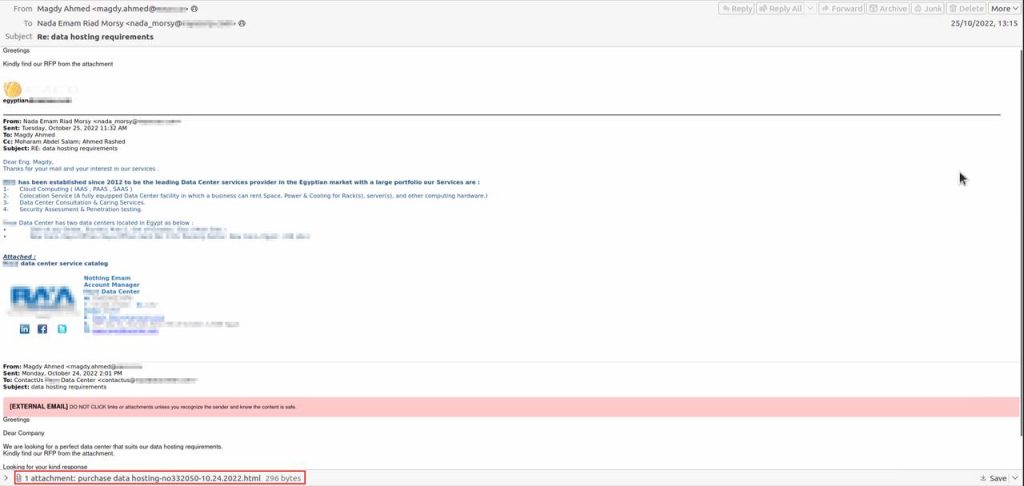

Once the victims click on the embedded link, they’ll head over to a fake page where they have to submit some personal information in order to download the Syncro installer. The URL claims that they’ll get a 21-day free trial, which shows some sort of urgency to the matter.


Yes, urgency is a huge motivator for high success phishing rates. When the installer takes root, this allows complete control over a computer.
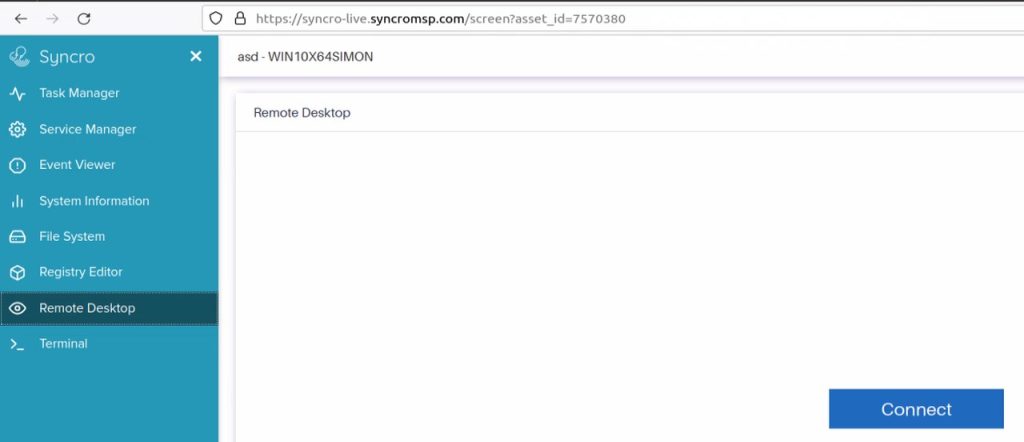

Syncro’s app has features that allow access to all kinds of commands, such as system terminal, services manager, remote desktop access, full file system access, and tasks.
With such privileges, the threat actors can start performing their malicious actions. Not only do they gain full control, but they also can embed additional backdoors, harvest files, and grant access to a whole different threat actor.
A Seedworm in Muddy Waters
Phishing attacks are very dangerous, and you should be vigilant when you receive an email. With cybercriminals offering compromised corporate email accounts for sale, these campaigns are definitely reaching a new high.
MuddyWater has been around for more than 5 years, and there’s a reason for this consistency. They’re elevating their techniques regularly, so we don’t know what their upcoming attack method would be. Just avoid clicking any links in emails your receive. That way, you’ll at least avoid any possible predicament.



