CactusVPN Review: Limited Number of Servers, Slow Speeds, and Slow Support


Right after you create your CactusVPN account, confirm your email address, change your password like you were prompted to do, you still won’t be able to use CactusVPN’s apps. To do that, you will have to log in to your account, click on ‘How to Start’ on the side menu to the left of the page, and copy-paste the username and passwords found there into the app.
It turns out that the so-called ‘Client Area Password’, the one you set up right after subscribing, as well as the username for that matter, do not work for the apps.
That’s not difficult to do, that’s not why I’m complaining. In fact, this method is more secure. But the problem was that it was not specified anywhere. I got a few wrong username/password messages before I started my hunt for the right credentials.
Sign up frustrations aside, let’s dive into the service. Starting with…
Features
According to the website, CactusVPN promises a lot. However, in reality, promises are not kept as it doesn’t have much to deliver. A VPN that requests around $7 a month should at least provide features that help it compete with other premium providers in the industry. Well, CactusVPN does have some, but it sure lacks a lot more.
Servers
This section will be rather short since CactusVPN runs just 39 servers in 22 countries.
No point in creating a list, so I’m just gonna write them down here: There are four servers in the UK, 9 in the US, 6 in the Netherlands, 2 servers in Canada, and one server in each of Brazil, Germany, Switzerland, Spain, Latvia, Romania, Italy, Portugal, France, Poland, Russia, Sweden, Hong Kong, Australia, Japan, Singapore, India, and Malaysia.
If the servers you are looking for are here, then keep reading. If not, then there’s no point in considering CactusVPN as an option for you. I must say though that CactusVPN’s server network covers a few of what I call major content markets – that is markets with highly sought-after content platforms, such as Hulu, American Netflix, the BBC iPlayer, and so on. But I must also note that with just 4 servers, I am very skeptical of the service’s performance, particularly when it comes to HD streaming.
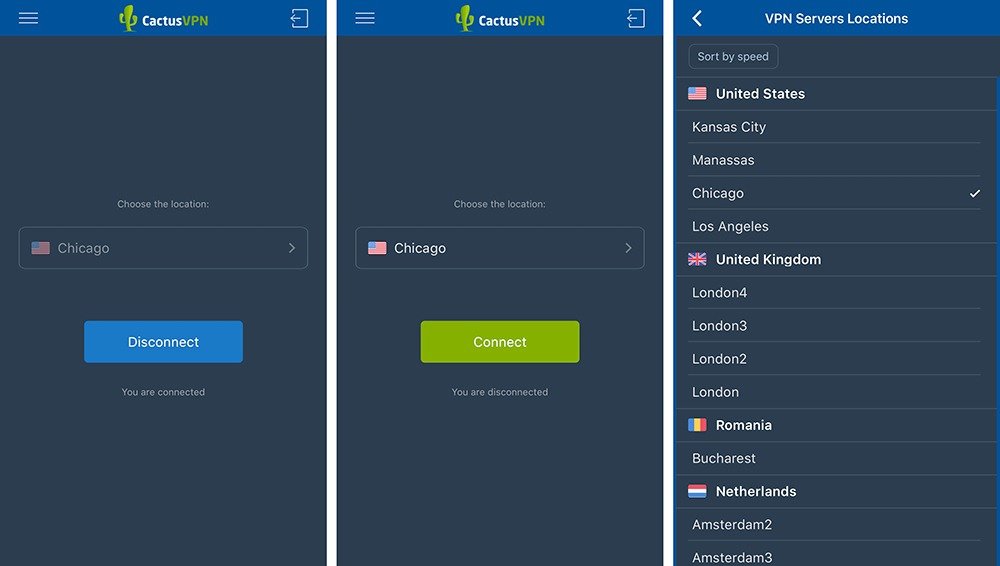

One upside, however, is that CactusVPN does not limit speed, bandwidth use, or server switches. That’s expected from every paid VPN, but still worth a mention.
Platforms & Simultaneous Connections
CactusVPN offers native apps for Windows, macOS, iOS, Android, Android TV, and Amazon Fire TV. That’s more than you can expect from budding VPN service providers, which typically stick to the four big platforms – Windows, Mac, Android, and iOS.
Additionally, there are setup tutorials for Windows Phone, Ubuntu, Chromebook, Boxee Box, and Routers, including DD-WRT, Asus, Mikrotik, D-Link, TP-Link, Linksys, Tomato, and Tenda.
One CactusVPN account will run on unlimited devices simultaneously. I need to mention that since CactusVPN can be set up on routers, you can cover even more devices that are not natively supported.
Just bear in mind that you should rely on your router to cover those static devices – such as smart TVs and gaming consoles – while keeping your mobile devices logged in separately.
Security
A VPN’s sole purpose of existence is to enhance a user’s security, and Cactus VPN actually does a good job in this department. Aside from encryption, VPN protocols are the main factor in your data’s routing process. So, with that said, let’s take a look at what CactusVPN has to offer when it comes to security:
Protocols
Depending on which device you are using, you could be using one of the following protocols:
WireGuard: Practically the newest. protocol on the list, which is considered the best to use in the VPN industry nowadays. WireGuard was originally deployed for the Linux kernel. However, it’s is now deployable on all major operating systems. The protocol is known for being security-focused, protecting user data with complete simplicity and ease of use. Moreover, it’s said to have better performance and connection speeds than OpenVPN and IPSec.
OpenVPN, open-source software that is generally recommended: “for the most security-conscious”. It is reliable and supports a great number of strong encryption algorithms and ciphers.
L2TP/IPSec is typically used when newer protocols aren’t supported – think old hardware, or in cases where security isn’t a major concern. The protocol also used for countries where this particular protocol is able to penetrate government and ISP firewalls. It is not generally recommended unless necessary.
IKEv2, or Internet Key Exchange version 2, is particularly well suited for mobile devices since it is good at reconnecting following a drop in your connection – think stuttery internet connections, driving through tunnels or in remote areas, or switching between a mobile and wifi connection. Naturally, IKEv2 is featured in many mobile VPN suites. Similar to L2TP, IKEv2 is merely a tunneling protocol, therefore, it is usually used in conjunction with IPSec for encryption even if it is not mentioned.
SSTP, or Secure Socket Tunneling Protocol, is a proprietary Microsoft protocol, making it a very good option for machines running the Windows operating system: it’s integrated into the system, making it more stable than other protocols when it comes to Windows machines. It is highly secure as well, and much less susceptible to blocking by firewalls than L2TP. It is only natively available on windows; aside from macs, it can run on other systems through third-party apps.
SoftEther, a relatively new protocol that is generally regarded as the challenger to OpenVPN. It is faster than the latter – the throughput for SoftEther is over 900 Mbps whereas OpenVPN’s stands at Mbps – while employing equally sturdy encryption methods to OpenVPN.
PPTP, the oldest and most vulnerable protocol. It has been failing security analyses since it was introduced in 95. So why is it still around? Well, PPTP is arguably the easiest to set up and fastest protocol around. But you SHOULD NOT use it unless security isn’t a concern for you.

Location & Logs
CactusVPN started as a small company in Moldova in 2011. The company’s technical team still operates out of Moldova, but the company has established its headquarter in Canada, which means that it falls under Canada’s jurisdiction, Quebec.
The good news is that Canada does not require its ISPs to retain online data of their customers. But back in August 2014, it was revealed that the government’s electronic intelligence agency, known as the Communications Security Establishment Canada, refused to openly declare how long it held onto the communications logs of Canadians.
In fact, Canada is a Five Eyes alliance member. The country has in place a legal framework that empowers its intelligence agencies to access and share electronic data with other member nations in certain situations.
I would like to also add a few words on Moldova’s situation regarding privacy since the company’s technical team, and I assume much of its equipment, is still based there. Moldova is located outside any data-sharing intelligence agreements, but the country does have a few privacy blemishes. Surveillance in Moldova is permitted, but only after obtaining a court order.
There is also the case of the “registru”, a centralized database that keeps information on all citizens of Moldova. The registry draws the ire of privacy activists and certainly does not sit well with us.
Regardless, CactusVPN’s no logs policy goes some way to appease our fears. The website reads: “No connection logs and most certainly no traffic logging. A completely log free VPN for every single one of you.”
Kill Switch
The Kill Switch acts as a fail-safe for when your VPN connection drops. Without a Kill Switch, your communications would automatically revert back to your original IP and your data will not be encrypted anymore leaving you exposed for an unspecified amount of time – the time it will take you to realize that you’ve defaulted back to your regular connection.
DNS Leak Protection
CactusVPN uses its own DNS servers. This means that ISP’s won’t be able to tell which websites you visit by intercepting a stray DNS request.
Apps Killer
An extension of the Kill Switch of sorts. The Apps Killer feature lets you specify which applications will be closed when the connection drops.
Support

Took about 40 minutes to get a reply; I’ve had to wait less for email support. But at least the support personnel I spoke with was courteous and knowledgeable.
Speed
Arguably the most critical part of a VPN review. As usual, I tested the speed performance of servers in major cities around the world.
Paris was a disaster: Download speed was reduced by 71.7% while the upload speed was reduced by a whopping 91.8%.
Chicago was a disaster: Download speed was reduced by 73.2% while the upload speed was reduced by 84.5%.
London was pretty bad: Download speed was reduced by 46.3% while the upload speed was reduced by 35.2%.
Amsterdam was acceptable: Download speed was reduced by 28.8% while the upload speed was reduced by 32.9%.
It’s just impossible to look past these bad scores.
Price & Final Verdict
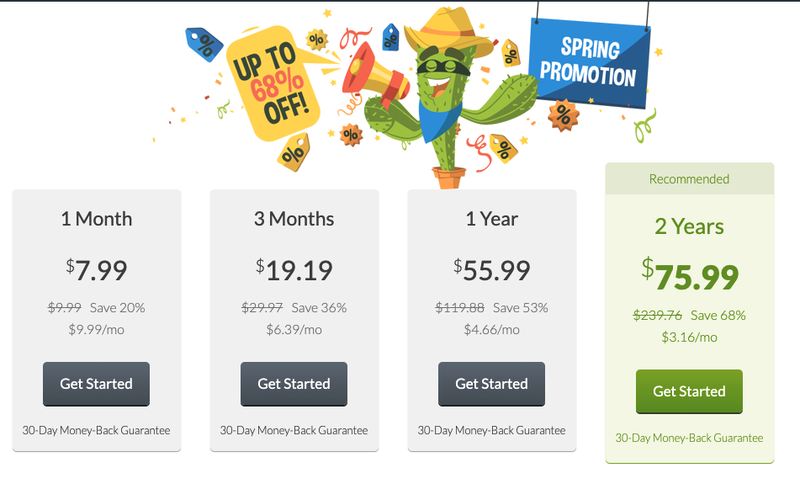

And it’s not just the speed. The app I used is far from pleasant looking. Using it wasn’t that great either. For instance, once you click on a server location in the servers’ list you have to manually leave the list to be able to hit connect. If you’re connected, you can’t browse the server list, you would have to disconnect first. Those aren’t deal-breakers, but they reflect a certain degree of laziness that I despise. And combined with the extremely limited server network, the slow support, and the atrocious speed performance, CactusVPN just does not cut it.
Before I leave, I should mention that the grid above shows the prices for monthly, quarterly, yearly, and biennial packages. You can check them if you like. The full yearly VPN package boils down to about $4.6 a month, which isn’t even cheap.