Ukraine’s DELTA Gets Phished – One Compromised Email Wreaks Havoc


Ukraine has its hands full with the ongoing conflict with Russia. Unfortunately, the country can’t seem to take a break as a large-scale phishing campaign is targeting its ‘DELTA’ situational awareness program users, infecting their devices with info-stealing malware.
The threat actors might be Russian – that’s the obvious deduction. However, researchers are stating that the individuals behind this are still unknown.
Apparently, these cybercriminals picked the perfect disguise as they’re using a compromised Ukrainian Ministry of Defense email to send out phishing texts and emails. What is going on? How are the threat actors conducting this campaign? Find out below.
A Fake Ministry of Defense Email Fools DELTA
Cybercriminals have taken phishing campaigns to a whole new level lately. It has become very common among them to masquerade as legitimate companies to gain their victims’ trust before striking.
For example, the use of alternative WhatsApp clients that grant extra features spiked in popularity in the past few years. Threat actors noticed that, so they started exploiting them to steal the users’ information.
Even Instagram was used as a pawn to lure victims into huge phishing scams a couple of months ago. In other words, everything is possible once threat actors put their minds to it.
Now, Ukraine’s ‘DELTA situational awareness program is the new target, and the damage might be bigger than anyone thinks. You see, DELTA is a concoction of Ukraine and its allies that aids the military in tracking the movements of enemy forces.
So, the data it possesses is quite crucial. This time around, cybercriminals are using a compromised email belonging to the Ukrainian Ministry of Defense.
The email plays on the “Sense of urgency” as it prompts the receiving user to update the ‘Delta’ certificates. If they don’t, they can’t keep using the system securely.
Certificates authenticate servers and legitimize applications. In other words, updating them is a must, hence the sense of urgency. The email contains a PDF that provides the receivers with the necessary steps to update the certificates.
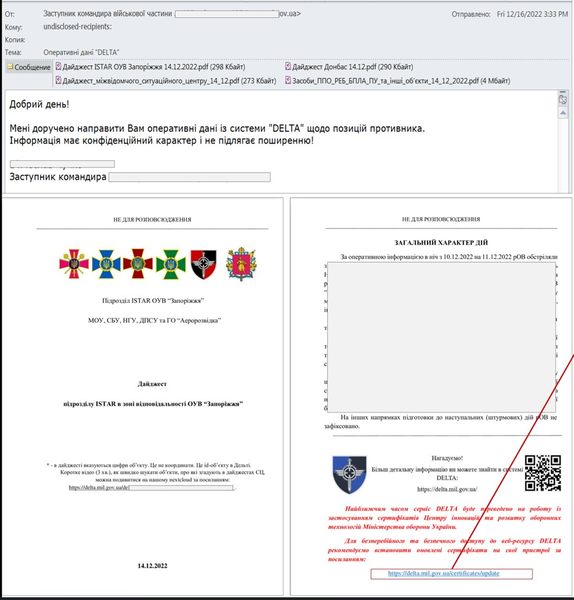

Just like most phishing emails, the victim is provided with a link that redirects them to a fake page that resembles DELTA’s website. This adds more legitimacy to the campaign.
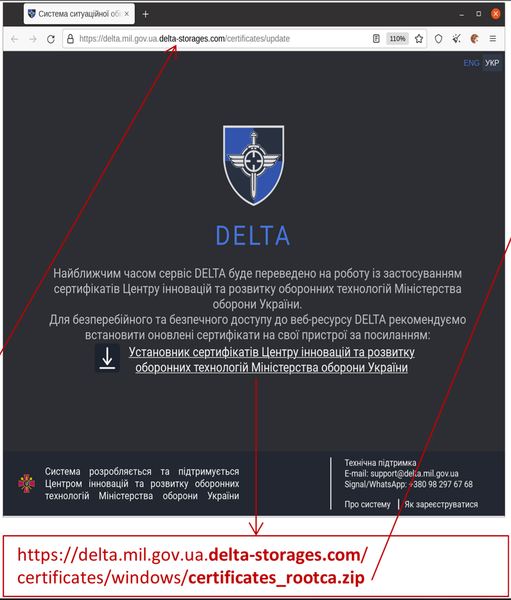

Once the victims download the file presented on the page, it creates several DLL files on their systems and initiates “ais.exe,” simulating the certificate installation. Again, this increases the illusion of the email’s legitimacy.
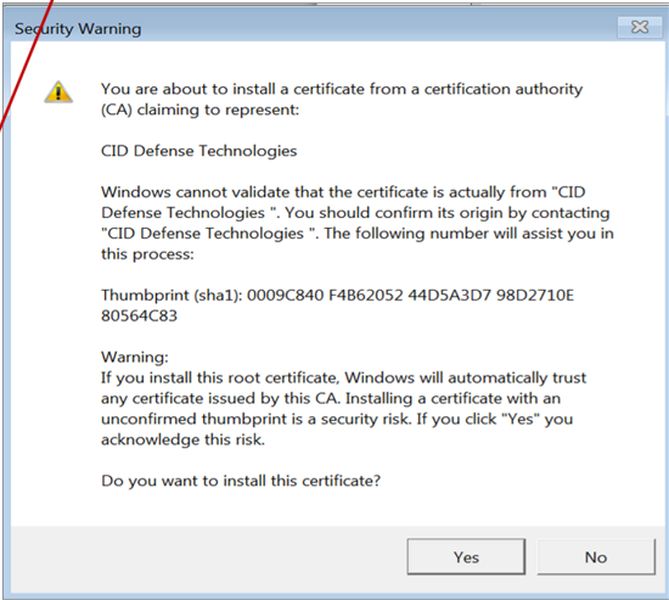

With VMProtect in place shielding the EXE files, AV analysis or detection is next to impossible. Once the DLL files (FileInfo.dll and “procsys.dll), of course, are malware, classified by CERT-UA as ‘FateGrab’ and ‘StealDeal.’
- FateGrab targets documents and emails.
- StealDeal harvests internet browsing data and passwords stored on the web browser.
If that doesn’t raise concerns among DELTA users, we don’t know what can. This is a dangerous campaign, and if the data gets into the wrong hands, chaos is inevitable.
A New Phishing Attack – Enter DELTA Infiltration Force
With the conflict between Russia and Ukraine reaching new highs, cyber-attacks are bound to happen on both ends. So far, CERT-UA did not link the operation to any known threat actors, but everyone has doubts.
Phishing attacks are dangerous but can be easily avoided. The link embedded in the email is everything the threat actors need you to click on. If you manage to avoid it, you’ll be saving yourself from such a predicament.



