Luna Ransomware – A Common Attack, A Not-So-Common Encryption Scheme


Based on how many cyberattacks have occurred this year, users are well informed about how dangerous the internet can be. Well, they’re about to enter a new malicious eclipse as Luna ransomware is on the rise.
Linux, Windows, and ESXi OS users, start securing your devices. If you operate any of these, Luna can infiltrate your platform and encrypt them.
The threat is real and might have a huge impact on the victims. But we have to ask: How does Luna operate? Who is using the newly developed ransomware? Find out in the following article.
Luna Ransomware – From Russia with Love
In 2022, cybercrime saw a huge spike as millions of victims were targeted by some sort of campaign, be it ransomware, malware, malvertising, phishing, and the likes.
A couple of days ago, even Google Play Store suffered an unexpected hit. The giant app library got infiltrated and hosted malicious applications (malware-infected) with thousands of downloads.
Now, the issue at hand is a new ransomware variant that goes by the name of Luna. Kaspersky, the famous cybersecurity firm, tracked down this campaign due to its unique approach.
As we mentioned, the malware targets specific devices – Windows, Linux, and ESXi systems. Moreover, the attackers wrote this malware in Rust, which is nothing new to the cybercrime empire.
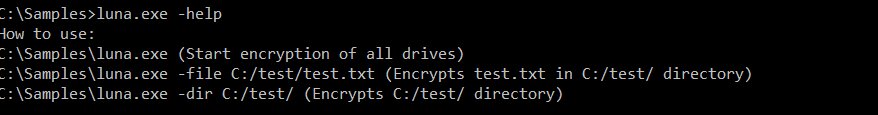

According to the study by Kaspersky, Luna doesn’t show a lot of complexity – it’s quite simple. However, what piqued the researchers’ interest was the malware’s encryption scheme.
As ransomware, Luna infiltrates a device and encrypts the targets’ data, which leads to a ransom negotiation in the end. Typical ransomware attack.
However, the security firm saw that their encryption is not so typical – Luna implements x25519 and AES – we don’t usually encounter such a combination in ransomware schemes.
Another discovery revolves around the malware’s origin, more accurately, what affiliates it works with. Apparently, Luna only works with Russian-speaking affiliates. How can we tell?
Any ransomware attack includes a note to inform the victims that they’ve been compromised. With this note, Kaspersky was able to know that the attackers are not of English-speaking origin.
The note hardcoded inside the binary contains spelling mistakes. For instance, instead of stating the phrase “a small team” it says “a little team.” Google translate maybe?
Lately, such attacks are following a trend of cross-platform ransomware. BlackCat and Hive are worth mentioning of course, as they heavily rely on languages like Golang and Rust.
This strategy promises higher success rates. Not only does it allow the attackers to transport from one platform to another, but it also helps to evade static analysis.
Luna Ransomware – The Malicious Side of the Moon
Ransomware attacks are on the rise, and new groups are emerging almost every day. Luna is still new, which is why security firms like Kaspersky have very little data on what victims have been encrypted or who future targets can be.
Ransomware remains a big problem in today’s society and it requires complete caution, especially for those who are not that tech-savvy when it comes to their online security. Protect your devices, take proper precautions, and stay safe.



