Play Store at It Again: Ad-Fraud Apps in the Millions

Here we go again! Google Play Store is seriously not making it easy to trust it again with our downloaded content. A couple of months ago, Google Play distributed malicious applications with 10 million downloads. A month later, the store hosted adware-infected apps with 7 million.
Now, Android’s most trusted “Download” platform has kicked it up a notch in terms of impact. This time around, the infected apps have been downloaded 20 million times – can you imagine the scale of this campaign?
Basically, this entire “Attack” is designed to install malware on the victims’ devices and perform mobile ad fraud. And with such a number (20 Million), a lot of damage can be done.
What is this campaign and what applications are spreading the malware? We’ve provided everything you need to know in the following article.
The Clicker Malware – A Perfect Masquerade
We all need convenience and Android devices can deliver exactly that. However, sometimes, such a privilege comes with a hefty price – our online security.
Online protection measurements have been evolving over the years, but cybercriminals haven’t been sitting around either. They’ve been coming up with new innovative ways to infiltrate their victims’ systems, and in most cases, they’re succeeding.
Tricking Google Play Store requires skills, and the threat actors behind this recent campaign definitely have some. To spread the malware as much as they can, the attackers embedded it in popular tools that seem totally harmless.
We’re referring to applications such as cameras, currency/unit converters, QR code readers, note-taking apps, and dictionaries.
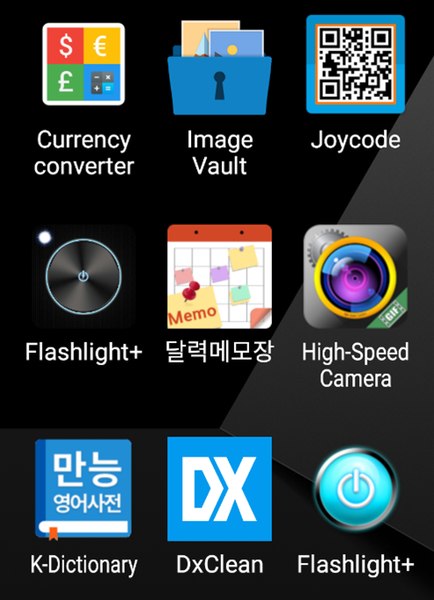

Using such applications guarantee excellent download numbers as such tools are highly in demand. You can find a full list of the infected apps below:
- High-Speed Camera – 10,000,000+ downloads
- Smart Task Manager – 5,000,000+ downloads
- Flashlight+ – 1,000,000+ downloads
- 달력메모장 – 1,000,000+ downloads
- K-Dictionary – 1,000,000+ downloads
- BusanBus – 1,000,000+ downloads
- Flashlight+ – 500,000+ downloads
- Quick Note – 500,000+ downloads
- Currency Converter – 500,000+ downloads
- Joycode – 100,000+ downloads
- EzDica – 100,000+ downloads
- Instagram Profile Downloader – 100,000+ downloads
- Ez Notes – 100,000+ downloads
- 손전등 – 1,000+ downloads
- 계산기 – 100+ downloads
- Flashlight+ – 100+ downloads
This clicker malware is very sneaky as it has the ability to evade any detection attempt by the infected victim. Such techniques allow it to easily do its job, which is visiting bogus websites in the background and simulating ad clicks without the victims’ knowledge.
The Malicious Practice
The malware’s functionality can drain the victims’ batteries and accelerate their data consumption. In other words, they might figure out the entire operation.
This brings us back to the “Sneaky” part where the application does not initiate its activities on the spot. Instead, it postpones it for an hour after downloading the app. Not only that, but it also incorporates a randomized delay in between to stay under the radar.
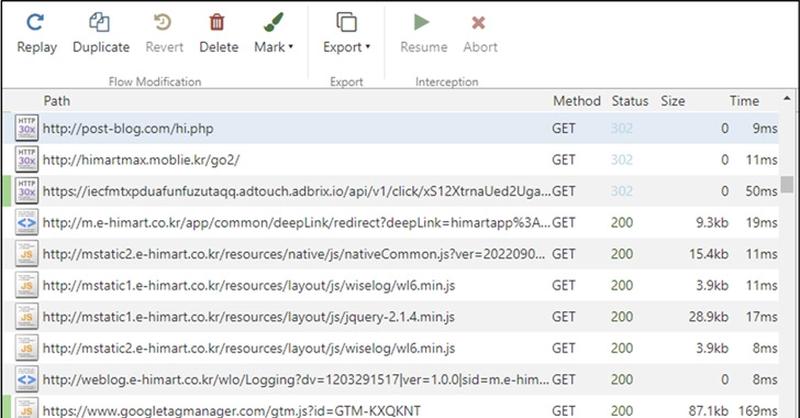

According to McAfee, this malware targets illicit advertising revenue and can disrupt the mobile advertising ecosystem. In other words, it continuously makes connections to websites, consequently awarding the attacker with revenue on a pay-per-click base.
Thanks to the security giant, this campaign was terminated and all the infected applications were later removed by Google Play Store.
Google Play Ad-Fraud: Convenience vs. Maliciousness
This Clicker’s behavior is cleverly hidden from detection and it might pop up in the near future. If we know cybercriminals, they’re definitely persistent.
Whenever you want to install an application, always make sure to read the reviews. Checking the number of downloads is not enough and this “Google Play ad-fraud” clearly shows that. Stay safe.



