Shrootless – A New macOS Vulnerability


macOS is very popular among users as it boasts the highest levels of security. Some might say it’s limited, but in reality, it uses protection functions to limit operations that compromise the system.
Unfortunately, even the mighty macOS has vulnerabilities and one was discovered lately by none other than Microsoft. Ironic, isn’t it?
What is this Shrootless vulnerability in the macOS system? How can attackers capitalize on it? Find out in this article.
macOS SIP – From Rootless to Shrootless
Mac has more than 100 million active users, which makes the impact of such a vulnerability quite huge.
it’s a well-known fact that Apple products are very secure. In fact, over the years, the company has hardened Mac’s SIP against attacks by improving and fine-tuning the restrictions.
SIP, aka, rootless, is the main factor that helps to lock down the system from rooting, protecting the entire platform in the process.
Once the attackers bypass it, they can take full control of the system as they can implement any type of arbitrary code without triggering the protection mechanism.
Unfortunately, Apple missed a few steps with their latest upgrade and made Macs completely susceptible to such practices.
The vulnerability (Shrootless) exists in the macOS Big Sur and Monterey operating systems.
Shrootless, yet Harmful
Microsoft researchers first came across it while installing a new application. As reported, with this vulnerability in place, an attacker could hijack the installation process by creating a post-installation script.
After that, it puts it in the destination where the process searches for such scripts. Very crafty indeed.
After that, the attacker would be able to install a malicious kernel driver (rootkit) and install undetectable malware.
Microsoft researchers implemented the following algorithm to create a fully functional proof-of-concept (POC) exploit:
- Download an Apple-signed package (using wget) that has a post-install script.
- Plant a malicious /etc/zshenv that would check for its parent process; if it’s system_installd, then it would write to restricted locations.
- Invoke the installer utility to install the package.
As seen in the image provided by Microsoft below, the POC exploit was able to override the kernel extension exclusion list: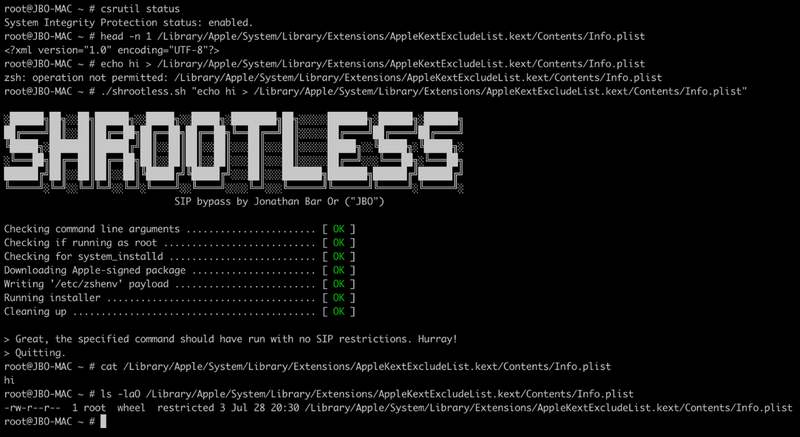

When everything is in place, the Shrootless attack bypasses the SIP and effectively gives the attacker root access.
As a result, the attackers can take complete control of the device and run any files, apps, processes, or programs they want without triggering any security measurements.
Make sure to check Microsoft’s full analysis as it sheds more light on the matter at hand.
macOS Vulnerability – Microsoft Saves the Day
macOS devices are as secure as they can get. However, malicious actors keep finding innovative ways to breach these barriers.
SIP on Mac acts as the device’s last line of defense against such attacks and malware. Microsoft was able to detect Shrootless, now identified as CVE-2021-30892, that was included in the security updates released by Apple on October 26, 2021.
Microsoft recommends that every company should have a security solution like Microsoft Defender for Endpoint. Let’s hope Apple gets the memo. We all know what a misconfiguration can do.



