A New Malicious Campaign – Some Good Old TOAD Vishing


Threat actors are always coming up with new tactics to lure victims into installing malware on their devices. The most notable technique would be sending phishing emails as it tends to have higher success rates. As dangerous as this is, cybercriminals can be more terrifying if they develop excellent social skills – enter VISHING.
Voice phishing is a technique that requires the best in social interactions – maintaining a convincing phone call. That’s exactly what’s going on in this new campaign, as threat actors are using the TOAD technique (telephone-oriented attack delivery) to deploy an Android malware dubbed Copybara.
The trojan saw the light back in 2021, and it has resurfaced again with a new voice phishing campaign. What is this campaign all about, and how are the threat actors implementing it? Here’s what we know.
A Vishing Campaign – Copybara From Rome with Love
Just like any other voice phishing attack, threat actors must be in direct contact with the victim, which can ensure that everything goes according to plan.
This particular campaign is not new. In fact, a while back, the same tactic was used to target customers of an Indian bank.
Now, the phishing scheme goes all the way to Italy, as the main targets are multiple Italian banks and their customers. Using personal information retrieved from fraudulent websites, the attackers call their victims in hopes of directing them to fake web pages.
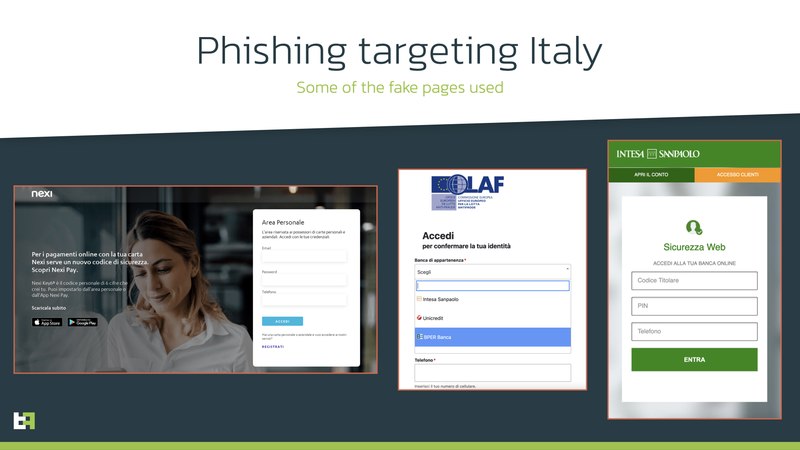

As seen in the image above, the threat actors are using a couple of pages that impersonate several Italian financial services and anti-fraud offices.
The pages require specific information, including a phone number that sets up the next process in the phishing campaign. Once the victim submits the data, the page notifies them that a support operator will contact them soon.
With the help of this “Agent,” the victims are instructed to install the necessary “security” app on their device. We all know what this is, right? This whole step-by-step walkthrough leads to the installation of the Android banking Trojan.
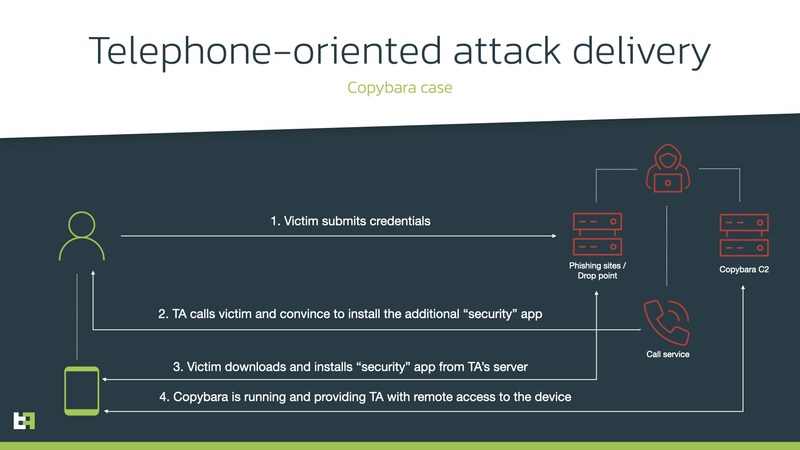

As the final step, the threat actor asks the victim to install a downloader app that will download the actual payload. The payload then installs an update for the downloader, substituting it.
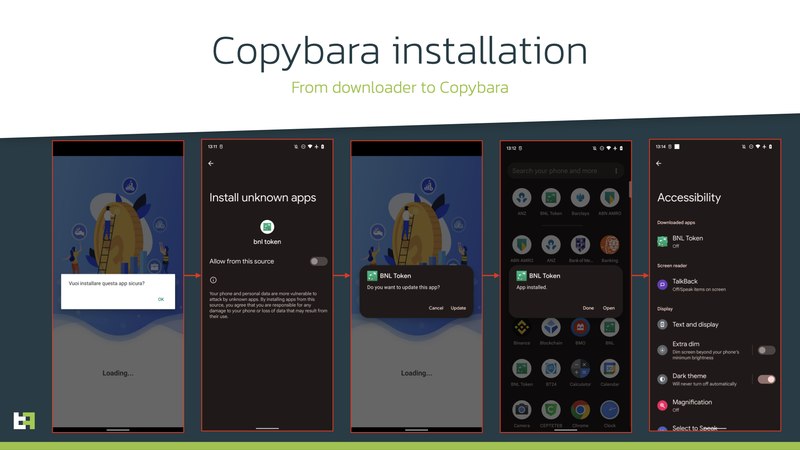

With Copybara in place, the attackers can perform all sorts of malicious practices. These include abusing the operating system’s accessibility services API, gathering sensitive information, and even uninstalling the downloader app to reduce its forensic footprint.
But wait, there’s more! Apparently, the trojan installs another malware named SMS Spy. This one allows the attacker to access all incoming SMS messages, including one-time passwords (OTPs) sent by banks.
Relying on traditional methods such as Google Play Store droppers, rogue ads, and smishing is in the past now. With social engineering skills, Vishing could become very popular sooner than we’d expect.
Vishing – The New Type of Phishing Attacks
Phishing attacks can come in several forms, such as email phishing, SMS phishing, or in this case, voice phishing.
The approach is very different in each of these campaigns, but the end result is the same. To avoid such predicaments, stay vigilant when approached with a shady email.
Not only that but if you get a call from anyone requesting you to download anything, double-check by calling your financial organization. Don’t fall for these schemes.



