Can Your Antivirus Program Spy On You?


- Various types of viruses and how they work
- The role of antivirus programs
- Can antivirus software be used as spyware?
- Select your antivirus wisely
- Install a VPN for better protection
Computers, smartphones, and all our other devices have become an integral part of our daily lives. They are so important that we sometimes compare them to our own bodies, especially when it comes to infections. And what’s the best way to flush out a virus? You treat it with antibiotics or take a vaccine as a precautionary measure.
The same thing applies to their online counterparts. Antivirus programs are the first line of defense against malicious software that threat our devices. They act as both vaccines and antibiotics, depending on which brand you use and whether you signed up for the free or paid version.
This protective software is so crucial to your online security and privacy that it comes pre-installed in all your devices. But what if your most trusted weapon against the dark side of the web is actually spying on you and stealing your data?
Content Overview
- Viruses and How They Infect Your Device
- Antivirus Programs and How They Work
- From Security Tools to Spyware
- How to Choose the Best Antivirus Program
- Install a VPN for Extra Security
- Conclusion
How Viruses Infect Your Device
Any programmer can create a computer virus. The latter is a harmful software that attaches itself to the code of other applications and programs to replicate and spread. It works similarly to its biological counterpart (like the flu, for example), which needs to infect a cell to reproduce.
Therefore, once you open your seemingly-legitimate file, you’ll also launch the malware and help it infiltrate other applications. And the consequences can be catastrophic. Viruses can steal your data, shut down your computer, log credit card information, erase essential documents, and more.
But how can your device catch the virus in the first place? Through the most-used system in the world: The Internet. Cybercriminals use the web as a hunting ground to target users, and all it takes is one click from your part. Malicious websites, ads, and links contain malware that immediately infects your device without your knowledge.
Viruses can also sneak in when you connect infected hardware, like USBs or external hard drives, to your computer.
Most Common Types of Viruses
There are several types of viruses, and they all operate differently. Each one infects your device using separate methods, but the most common ones are:
- Boot sector virus: It infiltrates the master boot record and takes control of your device when you start your computer. It mostly spreads through removable hardware like USBs. And removing it usually requires a system format.
- Non-resident virus: This one infects a specific file or application and remains dormant until you open the contaminated program
- Resident virus: The malware infiltrates your device’s memory. It is hard to detect and remove.
- Multipartite virus: It spreads through multiple ways, infecting both computer files and operating system.
- Overwrite virus: This type deletes everything it touches. The only way to get rid of it is to remove the infected file before it spreads, thus losing the data inside it.
- Polymorphic virus: As the name suggests, this malicious software changes its signature when it replicates, making it difficult to detect.
- Web scripting virus: It exploits the codes of web pages and browsers to attack any device that accesses them.
Antivirus Programs and How They Work
Since viruses have such damaging effects, you must protect your device with a reputable antivirus program. The latter detects, prevents, and removes malicious software on your computer, from viruses to worms and trojan horses.
These security tools use the virus’s “signature” to locate its whereabouts and eradicate it. They scan all your files and applications in search of these footprints, while also looking for behavior anomaly. You see, antivirus manufacturers have databases of virus signatures.
But since new malware emerges every day, some viruses might slip under the radar because the antivirus cannot recognize their signatures. Therefore, the protective software deploys three types of scans to ensure nothing has infected your files:
- Specific scan: Your antivirus program scans your device for known malware with a particular set of characteristics.
- Generic scan: This course of action helps detect viruses that come from known families, or in other words, share a common codebase.
- Heuristic scan: Your antivirus looks for behavior anomaly and suspicious patterns in your system to identify new threats. Furthermore, developers encourage you always to update your software to add new virus signatures.
From Security Tools to Spyware?
Antiviruses have access to everything on your computer, from programs, applications, and files to emails and web browsers. After all, it’s their responsibility to check for, identify, and eliminate potential threats. And they won’t be efficient if you confine their movements.
But with such freedom and authority over your device, is it possible to misuse this power? Surely your antivirus won’t commit the crime it vows to protect you from, would it? Well, according to certain reports, they are doing just that.
Because antivirus programs have such an open space for their operations, they can be the perfect spy tools. In fact, several well-known brands use them to invade your privacy, and they are supposed to be the good guys. You’ll soon find out that certain security products will monitor your online traffic, sell your browsing history, and insert backdoors for government agencies.
Kaspersky’s Russia Ties Accusations
Kaspersky Lab is one of the biggest cybersecurity companies in the world. According to Statista, it is one of the leading Windows anti-malware applications in the world, with over an 8% market share. However, the Russian company was involved in a massive privacy scandal.
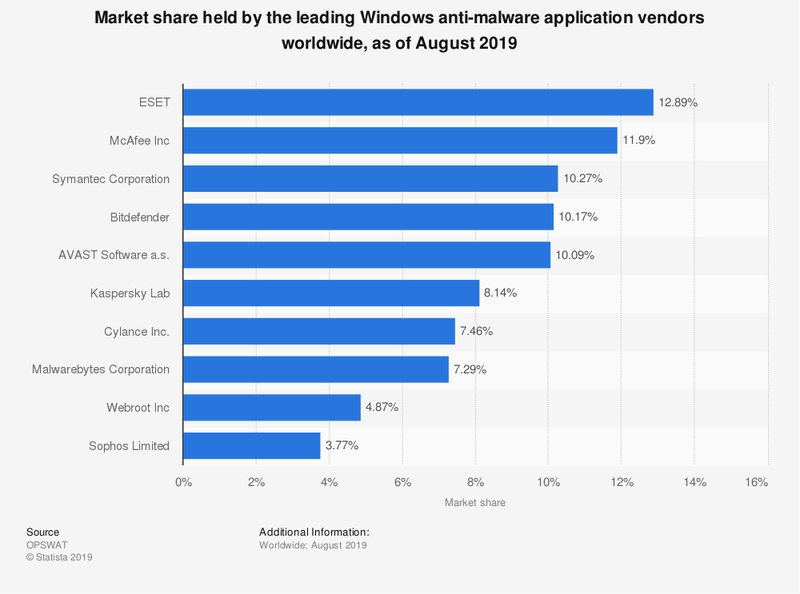

United States officials accused Kaspersky that its antivirus software was used as a spying tool by Russian intelligence agencies. As a result, the Department of Homeland Security urged federal civilian agencies to remove Kaspersky products from their devices.
The US received the tip from the Israeli government after its hackers found NSA hacking tools on the network of Kaspersky Lab. There has been no proof that the company is in collaboration with Russian authorities.
Kaspersky strongly denied any accusations concerning ties with Russian intelligence. “As a private company, Kaspersky Lab does not have inappropriate ties to any government, including Russia, and the only conclusion seems to be that Kaspersky Lab is caught in the middle of a geopolitical fight,” the company said.
Kaspersky founder Eugene Kaspersky stated in a blog post that the antivirus software’s task is to pick up malware from all quarters. In other words, he suggested that the NSA hacking tools were probably identified as malicious programs.
“We absolutely and aggressively detect and clean malware infections no matter the source.”
Eugene Kaspersky, CEO of Kaspersky Lab
Avast Selling User Data to Third Parties
Are you one of Avast’s 435 million users? Well, did you know that the company harvests your data and sells it to third parties? Yes, the multi-billion-dollar Czech security firm also makes a profit by sharing personal information such as your age, gender, and your other installed apps.
However, as Avast CEO Ondrej Vlcek told Forbes, there is no privacy scandal. Although he admitted that the company does indeed collect and sell user data, the information cannot be traced back to individuals. Here’s how Vleck explained it in a snippet from the interview:
“Avast users have their Web activity harvested by the company’s browser extensions. But before it lands on Avast servers, the data is stripped of anything that might expose an individual’s identity, such as a name in the URL, as when a Facebook user is logged in. All that data is analyzed by Jumpshot, a company that’s 65%-owned by Avast, before being sold on as “insights” to customers. Those customers might be investors or brand managers.”
But some privacy-concerned users won’t settle for such an assurance. They prefer that the company does not share any of their information. Yet, Vleck added that this process helps the likes of advertisers and investors without endangering subscribers’ privacy.
“So we absolutely do not allow any advertisers or any third party… to get any access through Avast or any data that would allow the third party to target that specific individual.”
Ondrej Vlcek, CEO of Avast
(If you’d like to know more about Avast and how to prevent it from collecting data, check this out.)
And Avast isn’t the only antivirus program that sells your data. Security firm AVG also uses its tools to collect and share user information, which includes search and browsing history. That’s according to the company’s privacy policy.
The Installation of Unwanted Programs
Free versions of antivirus programs will sometimes install annoying and unwanted programs on your web browser. And while your security software may respect your privacy, the add-ons attached to it may not. In the best-case scenario, they make your browsing experience less desirable.

Potentially unwanted programs, or PUPs for short, aren’t usually malicious. But they can ruin user experience by consuming system resources, displaying ads, or switching your default web browser. Moreover, they can install programs like toolbars, adware, and plugins. And some of them even monitor your traffic and sell it to third parties.
Free versions of Avast and Comodo, for example, attempt to install PUPs like their own web browsers. AVG, on the other hand, automatically downloads SafePrice, an extension that can reportedly find the best prices for online shoppers. However, it can also read and change your data on the websites you visit.
Doorway to Hackers
The reason why we install cybersecurity solutions on our various devices is to protect our online data. Now, imagine if hackers exploit this software to steal your personal information. Even though Thor Foresight Enterprise isn’t an antivirus program per se, it is a tool compatible with various products of that sort.
The Royal Bank of Scotland (RBS) offered it to its customers free of charge. Little did they know that they were putting their clients’ data at risk due to a security flaw in the system. That turned Thor Foresight Enterprise into a tool for hackers to steal users’ emails, internet history, and bank details.
“We were able to gain access to a victim’s computer very easily. Attackers could have had complete control of that person’s emails, internet history, and bank details.”
Ken Munro, Security Researcher at Pen Test Partners
Pen Test Partners discovered the flaw and warned against its severity. Heimdal Security, the company behind the product, was quick to respond and patched things up to eliminate the bug.
“We naturally treat information like this very seriously. We issued a fix and automatically updated 97% of all affected endpoints within four days of being informed, and the rest shortly after.”
Morten Kjaersgaard, CEO of Heimdal
Luckily, RBS customers did not suffer any adverse consequences.
How to Choose the Best Antivirus Program
Antivirus programs cannot protect your computer or other devices if they can’t have access to certain data. That includes files, apps, traffic destinations, and more. But do they need unrestricted entry to everything you do or have? And why sell such private information to third parties?
These solutions are your first, and sometimes your only line of defense against malware and online threats. Therefore, choosing the right option is a crucial and delicate matter that you must never take for granted.
- Try to avoid free antivirus programs: The best things in life are free, except when it comes to cybersecurity. Feeless providers must make money to cover expenses and generate profit, and the best way to do that is by selling your data.
Premium, paid services, however, don’t have to resort to such methods, which makes them a more suitable option for privacy enthusiasts. - Check out privacy policies: Most cybersecurity companies, or at least the reputable ones, have transparent and honest privacy policies. Therefore, make time to carefully read the literature before you install the app or extension.
- Read the installation process: Instead of blindly clicking “Next” and “Agree” to hasten installation, read the displayed messages. Otherwise, you might unknowingly permit your antivirus to set up PUPs like browser toolbars and adware.
- Customize privacy settings: If your antivirus allows it, you can alter some privacy options to your liking. For example, you can disable the collection and analysis of usage statistics and browsing behavior.
- Run background checks: Every antivirus software claims it offers the best services. But you can check for yourself by doing a bit of homework on the product and its manufacturer. You can either search online for news or visit review websites like Trustpilot.
Turn Your Device into a Fortress by Adding a VPN
For Internet users who are obsessed with privacy and security, an antivirus isn’t enough. Virtual private networks, better known as VPNs, are the ultimate tools for people who wish to protect their online welfare. They truly go above and beyond even the most secure antivirus programs.
VPNs use their own servers to transmit your data instead of those of your Internet service provider. They also protect your online traffic and activities with an encrypted tunnel, preventing any third party from monitoring. That includes ISPs, cybercriminals, and government agencies.
You see, a virtual private network works by redirecting your Internet connection through one of its servers. These servers are spread across dozens of countries and cover almost every region in the world. Once you choose your target destination, the VPN will reroute your traffic through it, making it appear as if you were living there.
And the pièce de résistance is changing your IP address to match the same location of your VPN server. These numerical labels assigned to your device give away your geographic position. By switching to another one, the entire online world will think that you are someplace else.
As a result, VPNs can help you avoid geo-blocks and gain unlimited Internet access. You’ll be able to unblock streaming services like Hulu, HBO Go, and BBC iPlayer, which are unavailable outside their respective regions due to licensing agreements.
Moreover, you can bypass Internet censorship if you live in countries like China, where Facebook, Twitter, and Google are banned.
But just like with antivirus software, you must steer clear of free services because they have similar privacy issues, as well as performance inefficiency.
ExpressVPN


I doubt that you’ll find a better overall VPN service than this one. ExpressVPN is a reputable and reliable brand in the industry, giving you the highest levels of security and privacy features.
Subscribers will benefit from the military-grade Advanced Encryption Standard with 256-bit keys (AES-256). That’s the toughest protocol in the business, and the same one the US government implements to protect information.
It translates to 115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,560,000,000,000,000,000,000,000,000 possible combinations.
And unlike certain antivirus programs, ExpressVPN does not collect or share activity or connection logs. Its servers “categorically eliminate storage of sensitive data,” which has been proven when Turkish authorities seized one of its servers in 2016 and found nothing.
“We designed our systems to not have sensitive data about our customers; even when compelled, we cannot provide data that we do not possess.”
ExpressVPN
There’s plenty more on offer, including a kill switch and DNS leak protection. Moreover, users will enjoy a 30-day refund policy, as well as a vast network of over 3,000 servers across 94 countries.
For the full details, check out the ExpressVPN review.
BulletVPN


Another VPN service that will go great with your antivirus program is BulletVPN. It may not be as famous as ExpressVPN, given it’s a relatively new brand, but they do share a lot of features, especially in the privacy and security fields.
The company also enforces the AES-256 encryption and has a similar zero-logs policy to protect user privacy. And for extra safety, the kill switch will cut off the Internet connection to your device in case BulletVPN stops working. That way, your ISP’s servers won’t intercept your traffic.
And if you activate BulletShield with it, the only way you’ll be able to access the Internet is if you connect to a BulletVPN server. Furthermore, there is a 30-day money-back guarantee, Netflix and torrenting support, as well as 24/7 customer support.
The only major drawback of this VPN is its limited server network, which features just 76 servers in 41 countries. Fortunately, though, they cover every region on the planet from west to east and north to south.
If you wish to know more, check out the BulletVPN review.
How Antivirus Programs Turn to Spyware – Final Thoughts
Antivirus programs are essential tools in combating online threats and protecting your privacy. But what happens when some of these products engage in the shady activities they are supposed to prevent?
Selling your data to third parties is a serious offense for an antivirus, even if the information doesn’t reveal your identity. Therefore, be careful when choosing your software and read the privacy policy thoroughly. And for additional security, privacy, and online access, install a premium VPN service.
Do you think antivirus programs should harvest and sell your sensitive data? Or do you feel like they are breaking their own vows? Tell us what you think below.



