SysUpdate Resurfaces: New Capabilities, Same Old Malicious Practices


Cybercriminals have one thing in mind – they infiltrate our systems to harvest personal data. However, each time malware is used, security firms come up with a solution to fend it off. That’s why threat actors tend to upgrade the malware in hopes of ensuring higher success rates. This is the case now, as none other than Lucky Mouse has just released an elevated version of the SysUpdate malware.
We always witness well-known cybercriminals targeting big companies around the world. Even Activision fell victim to a huge breach a couple of days ago.
But with Lucky Mouse creating a new Linux version of the SysUpdate malware toolkit, the risk is at its highest. What do we know about Lucky Mouse and the group’s malicious practices? Find out below.
SysUpdate Strikes Again – Lucky Mouse Gets Luckier
In the world of cybercrime, the more specific the attack is, the more damage it can do. For example, a while ago, operators of the Luna ransomware family launched a huge campaign that targeted Windows, Linux, and ESXi systems.
Another example is the HelloXD ransomware, as this one targeted Windows and Linux. Yes, Linux is very common, which is why SysUpdate has been developed and upgraded specifically for Linux devices.
This particular malware can evade any installed security software as well as resist any reverse engineering attempt. At least, that’s what its 2022 version can do.
But with Lucky Mouse’s role in this, the malware can do so much more now. The group is known globally as it goes under several aliases, including Bronze Union, Iron Tiger, and Emissary Panda.
It’s famous for utilizing malware families such as HyperBro, PlugX, and SysUpdate. The group has recently launched campaigns that involved compromising legitimate apps to perform its malicious practices.
We’re referring to incidents that include Able Desktop and MiMi Chat, where Lucky Mouse gained remote access to compromised systems.
Apparently, the group’s latest target is a gambling company in the Philippines, which has been a constant target ever since Lucky Mouse was known as Iron Tiger back in 2019.
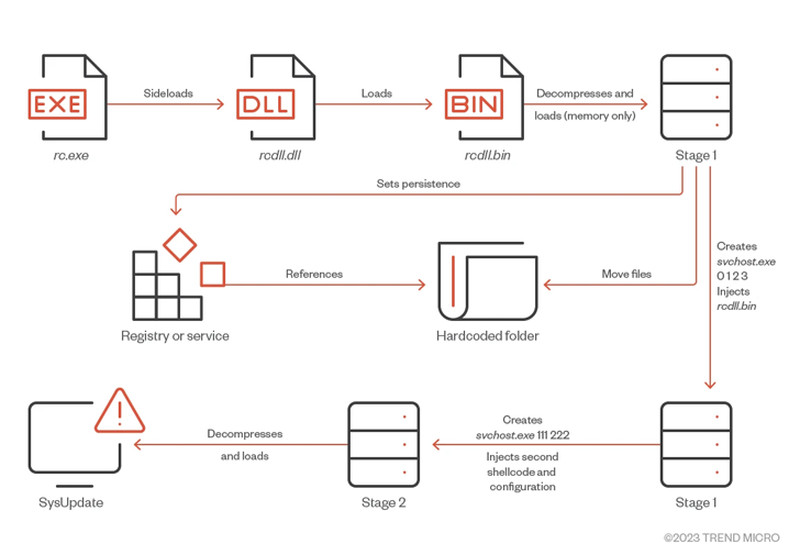

According to the study done by Trend Micro, SysUpdate is capable of performing the following practices once it takes rook within the device:
- Service manager (lists, starts, stops, and deletes services)
- Screenshot grab
- Process manager (browses and terminates processes)
- Drive information retrieval
- File manager (finds, deletes, renames, uploads, downloads a file, and browses a directory)
- Command execution
One feature that hasn’t been seen yet in this malware is that it now uses C&C communication through DNS TXT requests. While it’s not a communication protocol (Not supposed to be), Lucky Mouse abuses it to send/receive data.
Lucky Mouse Back at It – Malware Maliciously SysUpdated
Lucky Mouse has been terrorizing big companies for quite some time now. Apparently, the threat actors in the group have developed an interest in gambling companies.
Well, we know why! There’s a lot to gain there. The new SysUpdate shows potential, and it seems to be spreading through legitimate applications.
While it hasn’t reached macOS yet, it sure does have the potential to be a cross-platform toolkit. That only indicates that it might be heading to Mac devices next.



