Averting Cyberthreats – Why Businesses Must Combine MSS, EDR, and MDR


- The rise of new malware
- MSS, EDR, and MDR explained
- Top MSS, EDR, and MDR tools
- Companies must adopt EDR with MDR to protect network security
Cyberattacks aren’t just growing in number; they’re also becoming much more advanced. This threat evolution, coupled with an ever-increasing number of Internet-connected devices, rendered cybersecurity a challenging task. Add the coronavirus effects to the equation, which forced companies from every sector to shift to the digital realm due to lockdown restrictions, and you got a recipe for disaster.
That is why many organizations resorted to managed security services (MSS), a systematic approach to address security needs. MSS is responsible for security management, monitoring, and maintenance. However, it can only detect and respond to known threats, while new ones can slip through undetected. And according to the latest reports, unknown malware and attacking methods are on the rise, especially during the COVID-19 pandemic.
Therefore, the safest course of action is to mix MSS with endpoint detection and response (EDR) and Managed detection and response (MDR) technologies.
New Malware Surging
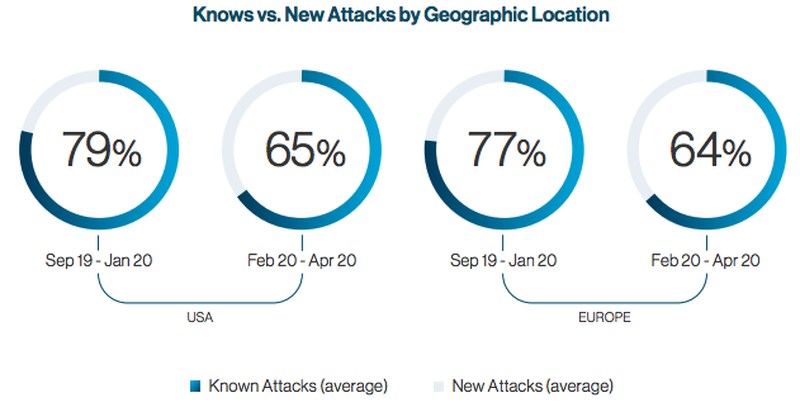
In a recent study on COVID-19-related cyberattacks, Internet security firm Cynet revealed that new malware has significantly increased. Hackers are using more advanced methods and techniques to bypass security protocols, especially in attacks against businesses in Europe and North America. Before the coronavirus outbreak, the company recorded that around 80% of offensives featured existing malware, while 20% had new threats.
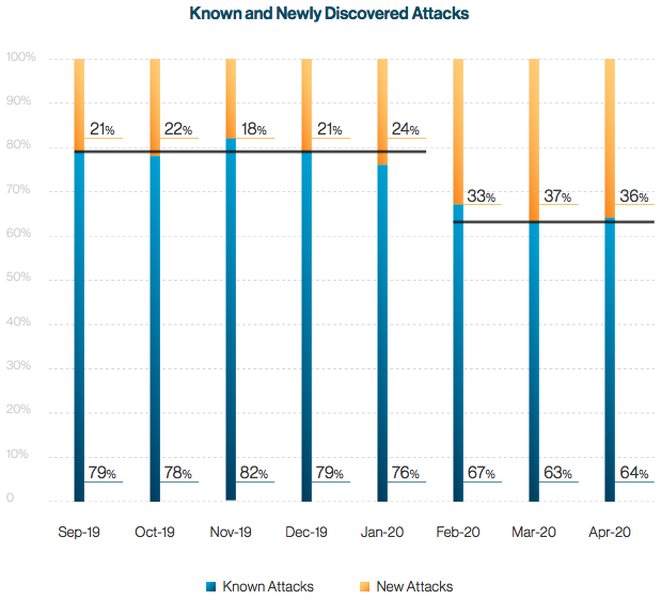

But after the spread of the coronavirus in early 2020, figures changed a little bit. The number of known malicious software dropped to 65%, while new, unknown threats increased to 35%. They included “new phishing attempts, new malware variants, and even new malware.” This sort of attack is tough to detect, prevent, or defend against.
Therefore, businesses must employ advanced technologies that protect their systems while also executing behavioral analytics and launching investigations. MSS alone cannot accomplish all those feats, which is why you must combine it with EDR and MDR for maximum protection.

MSS, EDR, and MDR – Everything You Need to Know
Businesses need to invest in Security Operations Centers (SOCs) that focus on threat detection and response. According to research and advisory firm Gartner, 50% of all SOCs will start implementing modern services by 2022. In other words, they will feature an integrated incident response, threat intelligence, and threat-hunting capabilities. Less than 10% of SOCs offered these services in 2015.
Managed Security Services (MSS)
The origins of managed security services (MSS) dates back to the mid-1990s when companies would outsource their network security needs to a service provider. The organizations that offer such assistance are known as managed security service providers (MSSPs). Businesses resorted to MSSPs solutions to avoid dealing with critical security issues like cyberattacks and malware, and user data theft.
But as these services evolved and grew in popularity, several companies started conducting them in-house instead of outsourcing them. MSS is responsible for several functions, including:
- Round-the-clock network monitoring and management: MSS ensures that network security is fully functional and safe without any existing or potential threat. They do so by continuously monitoring the system, which provides the service with real-time visibility to the company’s security state. That includes analysis of several data, like network traffic.
- Vulnerability and intrusion management: MSS allows businesses to identify, prioritize, and repair system weaknesses that cybercriminals might exploit. Furthermore, their intrusion detection and management systems search for and subsequently block irregular malicious traffic, which could be malicious.
- Security technology management: MSS makes sure that network security tools like firewalls, VPNs, security gateways, and advanced threat defense technologies are fully functional.
- Security compliance monitoring and management: MSS helps organizations assess, track, and document data to prove they’re compliant with government and industry regulations. That includes mandates like the Payment Card Industry Data Security Standard (PCI-DSS) and the European Union’s General Data Protection Regulation (GDPR).
MSS Alone Isn’t Enough
While managed security services help companies monitor, identify, and respond to threats, they only protect against known malware. They are reactive services that act on what is reported and seen in the organization’s environment. Therefore, You need a proactive service that combines real-time behavioral analytics with the latest threat-detection technologies to locate and destroy new malware traces.
Top MSS Tools
| TOOL NAME | PROVIDER | SERVICES |
| IBM Managed Security Services | IBM | Firewall, Information event, and Intrusion detection and prevention system management, etc. |
| AT&T Managed Security Services | AT&T | MTIPS, business direct portal, mobile security, email and web filtering, DDoS mitigation service, etc. |
| Dell SecureWorks Managed Security | Dell SecureWorks | Firewall management, log monitoring and retention, intrusion prevention, vulnerability management, etc. |
| Verizon Managed Security Services | Verizon | Firewall management, e-mail security gateway, log monitoring and management, VPN, etc. |
| Cipher Managed Security Services | CIPHER | Cybersecurity monitoring, incident management & cyber defense, vulnerability & compliance management, etc. |
Endpoint Detection and Response (EDR)
Anton Chuvakin, a former Gartner research vice president and analyst, was the first to coin the term “Endpoint Threat Detection and Response (ETDR)” in July 2013. Today, it is commonly known as Endpoint Detection and Response (EDR). It’s an emerging technology that focuses on monitoring endpoints instead of the entire network.
EDR stores the information on a central database for further analysis, detection, investigation, reporting, and alerting. It uses analytic tools to identify, respond to, and deflect internal threats and external attacks. Not all EDR tools have the same capabilities, though. Some perform additional analysis on the agent, while others focus on the backend. In fact, certain services offer application control, data encryption, and network access control.
However, all of them provide continuous monitoring and analysis to identify, detect, and prevent advanced threats.
Companies Not Taking Full Advantage of EDR
According to Security Boulevard, businesses purchase expensive and sophisticated EDR services but don’t fully benefit from them. The cybersecurity news website describes it as buying a Ferrari just to commute instead of experiencing what the car can do. Therefore, SB recommends combining it with an MDR service to fully take advantage of it, thus maximizing your network security.
Top EDR Tools
| TOOL NAME | PROVIDER | SERVICES |
| Cynet 360 Endpoint Detection and Response | Cynet | Total environment visibility, threat prevention & detection, 24/7 MDR service, automated response, etc. |
| Falcon Insight | CrowdStrike | Real-time, full-spectrum visibility, threat detection, response & forensics, etc. |
| VMware Carbon Black EDR | Carbon Black | Continuous visibility, threat hunting, incident response, managed detection, audit & remediation, etc. |
| ActiveEDR | SentinelOne | Automatic threat mitigation, threat hunting, real-time threat detection, AI technology, etc. |
| Symantec EDR | Broadcom | Cloud-delivered analytics, threat intelligence, 24/7 managed services, threat hunting & detection, etc. |
Managed Detection and Response (MDR)
MDR services aid businesses in continuously detecting threats, responding to incidents, and monitoring their IT assets. They focus on threat detection instead of compliance, protect Internet gateways, and detect threats that pass traditional security tools. Moreover, MDR mostly relies on security event management and advanced analytics.
Humans analyze security events and alert the customer instead of relying on fully automated systems. While automation is involved, customers can interact directly with the team of analysts. There are no portals or dashboards concerning alerts, security events investigations, case management, or other activities.
Additional valuable MDR functions include sandboxing, malware reverse engineering, and identification of compromise indicators.
A managed detection and response team is an ideal solution for companies without time or resources to manage their security systems. Besides, some of the tools that MDR uses are too expensive for businesses to buy independently. That is why investing in this service would make more sense. Furthermore, MDR detects, analyzes, and prevents threats. I’m not just talking about known malware, but also new ones that traditional MSS providers usually miss.
Selecting the Right MDR Provider
Strengthing your security system through a managed detection and response service provider is the right way to go. There are a couple of things to keep in mind first, though, including:
- Not all MDR providers offer the same services. Each company has its own tools and procedures to detect and respond to threats. Therefore, make sure you pick the ideal service that will maximize your company’s security.
- MDR services enhance your current tools and expertise. Therefore, if you don’t have extensive resources, get a managed detection and response provider with a considerable toolset. And if you’re already equipped with secure technology, consider a provider with a different a toolset than what you have. We recommend combining EDR with MDR.
- As I mentioned earlier, MDR focuses on threat detection rather than compliance. However, the service must never ignore data and privacy regulations.
Managed detection and response services are relatively new in the IT industry. But they provide valuable solutions to companies seeking to improve their security systems. Gartner expects the appetite for MDR services to reach 15% in 2020, a massive jump from the 5% market share it registered in 2018.
Top MDR Tools
| TOOL NAME | PROVIDER | SERVICES |
| SentinelOne Vigilance | SentinelOne | Threat detection, deep-dive analysis, threat insights & documentation, proactive escalation, 24/7 assessment & response, etc. |
| Falcon | CrowdStrike | Managed threat hunting, threat intelligence, malware research & analysis, vulnerability assessment, container security, etc. |
| eSentire MDR | eSentire | 24/7 in real-time threat investigation and response, threat detection, full visibility, unlimited incident response, etc. |
| Expel MDR | Expel | 24/7 monitoring, proactive threat hunting, advanced analysis, incident response, containment & remediation, etc. |
| Cybereason MDR | Cybereason | 24/7 proactive threat hunting, contain, eliminate, and root out threats, threat intelligence, incident response, etc. |
MDR – The Wave of the Future
The cybersecurity sector has long focused on protecting the network, providing limited managed security services (MSS). But after cyberattacks became more complex and advanced, and the number of Internet-connected devices significantly grew, a more secure approach was needed. Otherwise, MSSPs risk becoming irrelevant to their clients. So, in reality, it’s an “evolve or die” matter.
But then came endpoint and application-level protection with EDR and MDR. Combining these two solutions provides real-time threat detection and response capabilities that organizations desperately need. Moreover, managed detection and response services deliver advanced threat hunting and remediation. Businesses will finally be able to detect new malware before and proactively eliminate it.



