What Are DDoS Attacks and How to Prevent Them?


- DDoS Attacks explained
- Differentiating between legitimate and fake traffic
- Different types of DDoS attacks
- Preemptive measures
2020 witnessed a substantial surge in cybercrime as the COVID-19 pandemic forced the entire globe into lockdown. And with almost every employee working from home and accessing company networks from private and insecure computers, cybercriminals took advantage of the chaos to launch brutal attacks. And according to Cynet, they went all in, using every trick and technique in their arsenal.
New phishing attempts, malware, and malware variants were deployed to bypass security protocols undetected. But known threats like distributed denial-of-service attacks, aka DDoS, were also used in vast numbers. Through DDoS, cybercriminals can overwhelm websites with heavy Internet traffic until they stop working and go offline.
As a result, DDoS attacks can have a massive impact on businesses, resulting in time, client, reputation, and financial losses. Therefore, you must learn how these attacks work and what you must do to avoid them.
What Is a DDoS Attack and How Does It Work?
A disturbed denial-of-service (DDoS) attack is one of the most popular tools for hackers and cybercriminals. Whenever hackers take down a website, it means it fell victim to a DDoS onslaught. They do so by directing traffic from a swarm of users towards the target, intending to overwhelm it, and disrupt its service. Once the website can no longer accommodate the requests, it crashes.
The traffic flow from hundreds of thousands of users may contain connection requests, incoming messages, or fake packets. In some cases, hackers target banking and financial institutions with low-level DDoS attacks. Their aim is to send warning shots, threatening to significantly enhance their offensives if the victims don’t pay a ransom. A cybercriminal group called the Armada Collective extorted several banks and web host providers this way in 2015 and 2016.
The most common way to carry out DDoS attacks is through remote-controlled, malware-infected devices. They can include computers, smartphones, and any other Internet-connected tool. Cybercriminals are increasingly using IoT (Internet of Things) devices in DDoS attacks. That’s because their security systems are weaker than those computers have, making them more vulnerable to hacking.
These malicious devices are referred to as botnets, a group of individual bots or zombies that hackers control to swamp websites and servers with more data than they can handle. Your computer can be part of a botnet without your knowledge. In other words, each bot is actually a legitimate device, making it harder for victims to separate normal traffic from DDoS attacks.
Botnets for Sale on Dark Web
Contrary to common belief, not all hackers can infiltrate NSA (or other major entities) systems in mere seconds by quickly tapping on their keyboards. Certain hacking attempts require advanced abilities and techniques that few cybercriminals can reach.
Assembling a botnet army for DDoS attacks, for example, is a time-consuming and challenging task for some. Therefore, more sophisticated and knowledgeable hackers develop botnets and sell them on the digital black market. The Internet isn’t just a source of information and entertainment. Just like “The Force,” it has a dark side called the dark web.
It is a place where criminals buy and sell products and services, like botnets and stolen credentials. These underground markets are just like regular online retailers, but for illegal deeds. You can find discounts, guarantees, and user ratings.
The only way to enter the dark web is through the Tor network, a web browser that provides anonymity when surfing the Internet. It reroutes your traffic through multiple nodes and encrypts it every step of the way. Tor isn’t solely for criminal or illegal activities. Anyone who values online privacy can use it.
How to Determine If You’re under a DDoS Attack?
Preventing DDoS attacks is a challenging task. As we already mentioned, it’s hard to distinguish between legitimate traffic spikes and distributed denial of service. Furthermore, symptoms of a DDoS attack can sometimes be attributed to virus infection or slow Internet speeds. Therefore, you must have professional diagnosis and analytics tools to help you detect traffic anomalies.
According to Cloudflare, here are some of the signs that indicate you’re under a DDoS attack:
- Suspicious amounts of traffic originating from a single IP address or IP range
- A flood of traffic from users who share a single behavioral profile, such as device type, geolocation, or web browser version
- An unexplained surge in requests to a single page or endpoint
- Odd traffic patterns such as spikes at odd hours of the day or patterns that appear to be unnatural (e.g. a spike every 10 minutes)
Also, Norton listed the symptoms of DDoS attacks, such as:
- Slow access to files, either locally or remotely
- A long-term inability to access a particular website
- Internet disconnection
- Problems accessing all websites
- Excessive amount of spam emails
The American software security company added it’s hard to label these indicators as unusual. But if two or more occur for long periods, there’s a high chance a DDoS attack has hit you.
Impact of DDoS Attacks
Bringing down websites and Internet services may not sound like much, but it actually causes heavy damages. Sophisticated DDoS attacks can disrupt platforms for days, if not weeks, resulting in the loss of money, clients, reputation, and time. Undoing the damage and getting the proper protection measures is also costly.
During the attack, visitors and employees won’t be able to access the network. That means online shopping websites, for example, won’t be able to sell products and make money. According to a Kaspersky study, these services could lose up to $20,000 per hour, depending on the severity of the attack.
The report also highlights the effects of DDoS attacks on bot computers. These victims are, in most cases, innocent bystanders and unknowing culprits. Cybercriminals exploit vulnerabilities in their systems, install malware, and use their devices to launch offensives. But sometimes, these victims contribute to their own downfall by opening malicious links, files, and attachments that hackers send.
Either way, DDoS attacks will cause bot devices to run slowly or even crash if there’s too much resource consumption.
Types of DDoS Attacks
Although all DDoS attacks rely on flooding their victims with too much traffic, industry experts have divided them into three categories:
- Volumetric: As the name suggests, hackers send massive amounts of traffic to overflow a network’s bandwidth.
- Protocol: These attacks are more targeted and take advantage of weaknesses in a server’s resources.
- Application: The most sophisticated and advanced form of DDoS attacks, focusing on particular web applications.
Now, hackers can use one or more attack vectors to try and circumvent security systems’ defensive measures. Here are the different types of DDoS attacks:
Volumetric Attacks
These are the most popular DDoS attacks among cybercriminals. The process is pretty basic, overwhelm the website’s servers with more traffic than it can handle. They use a botnet army to make the traffic seem legitimate.
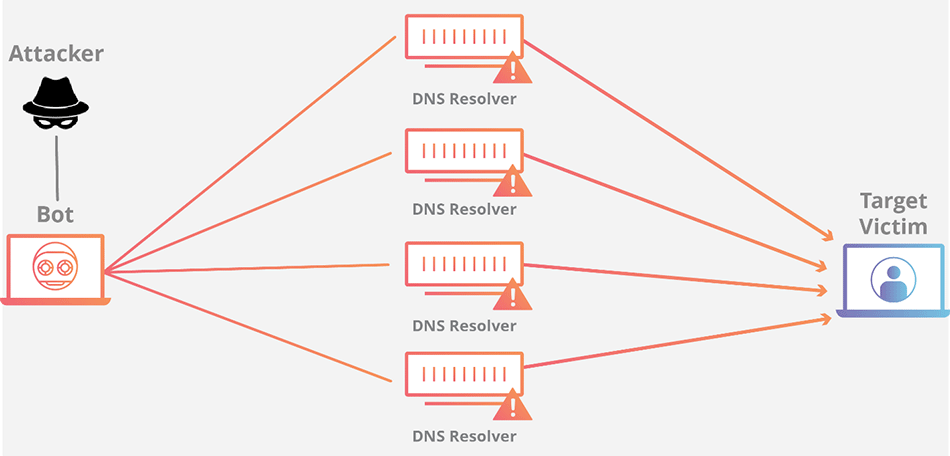

Source: Cloudflare
Application Attacks
Application layer attacks, or Layer 7 attacks, target the layer where server networks respond to HTTP requests and generate web pages. They single out applications instead of going for the entire bandwidth, making them harder to detect. Company servers will consider them legitimate traffic before it’s too late, and the victim is flooded with connection requests and unable to respond.
Sometimes, cybercriminals mix application attacks with other types of DDoS onslaughts to hit the entire network and bandwidth as well.
TCP Connection Attacks
Transmission Control Protocol attacks, aka SYN floods, take advantage of a vulnerability in the TCP connection sequence called the three-way handshake between client and host. Attackers send a connection request to the server to initiate the handshake. However, the SYN flood prevents the handshake from taking place, leaving the connected port as occupied and unavailable to process further requests.
Meanwhile, cybercriminals keep sending more requests to overwhelm the server and shut it down.
Fragmentation Attacks
Another common type of DDoS assaults is fragmentation attack, which could come in several forms. It involves taking advantage of the datagram fragmentation process, where IP datagrams are reduced to smaller packets, transferred across a network, then put together again. During the attack, however, fake data packets that remain divided swamp the server.
Cybercriminals sometimes use Teardrop attacks, a different form of fragmentation attack. They use malware to prevents data packets from regrouping. Windows was able to fix and protect against this problem in newer software versions. But those with older models could still be vulnerable.
Gaming Industry’s Share of DDoS Attacks
Some players will do anything to win live online matches against their peers. And when we say anything, we include resorting to cyberattacks like DDoS onslaughts. As I mentioned earlier, there are several DDoS-for-hire services on the dark web, making it easier for gamers with poor sportsmanship to target the opposing player’s server or IP address.
Once the server reaches its limit and crashes, you will be disconnected from the match and subsequently lose. According to cybersecurity software company Imperva, the gaming industry was on the receiving end of most DDoS attacks in 2019. In its Global DDoS Threat Landscape Report, Imperva said that 35.92% of attacks targeted the gaming sector.
The report added that 51% of the attacks lasted less than 15 minutes, with most of them aiming at the same targets. 77% of the attacks occurred in East Asia, with India taking first place at 22.57%.
Protect Yourself from DDoS Attacks
Avoiding Distributed Denial-of-Service attacks is tricky, especially when it comes to identifying fake connection requests. If your security system cannot differentiate between legitimate traffic and DDoS attacks, you won’t be able to take preemptive measures.
Therefore, the safest course of action is:
- Tweak your firewall and router: Your first lines of defense are your firewall and router, which is why you must always equip them with the latest security patches. Furthermore, you have to configure them to detect and reject fake traffic.
- Act quickly: The earlier your security systems pick up a DDoS attack, the better you can prepare yourself to contain it. With the help of anti-DDoS software, companies can identify unnatural traffic surges early, notify the ISP, and request a traffic rerouting. Some businesses even have a backup Internet service provider. ISPs will use the blackhole rerouting method to redirect the traffic to a null destination. The solution is not ideal, though, as all your traffic will go through that route, both legitimate and fake.
- Use AI technology: Programs with artificial intelligence can quickly redirect your traffic to the cloud, analyze it, and prevent malicious requests from reaching company servers. AI technology can determine known DDoS attacks, and its self-learning mechanism can predict future patterns and methods.
- Protect your IoT devices: As I mentioned earlier, IoT devices have weak security systems. Therefore, make sure you protect all your Internet-connected devices with the latest security systems. You must also use strong passwords to secure your accounts. Otherwise, cybercriminals could use your devices as part of their botnet army.
Concluding Your Guide to DDoS Attacks
As you can see, DDoS attacks are highly disruptive and could cost a lot of damage. The most dangerous thing about them is they can disguise as regular online traffic, making them hard to detect. Once they flood the server with more traffic than it can handle, the online service will run slowly or even crash.
Therefore, you must invest in special DDoS software to identify bogus traffic and prevent the different types of DDoS attacks. Otherwise, you risk losing money, clients, time, and reputation.
Have you ever experienced a DDoS attack? Share your thoughts below.



