The End of the RAINBOWMIX – Google Removes 240 Apps for OOC Ads


- Apps displaying OOC ads found on Google Play Store
- Researchers name OOC app campaign RAINBOWMIX
- How RAINBOWMIX bypassed Google security
- Play Store removes all RAINBOWMIX apps
Retro video games take us on a trip down memory lane, back when Atari, Sega, Mattel, and Nintendo were all the hype. Pac-Man, Space Invaders, Contra, and Super Mario were just some of the stellar names that kids in the 1980’s would spend hours playing. Therefore, whenever we see emulator games on app stores, we’re tempted to download them.
But in some cases, cybercriminals take advantage of our nostalgia and develop fraudulent apps and games. And that’s precisely what White Ops researchers discovered on Google Play Store. They identified 240 Android applications displaying out-of-context (OOC) ads posing as retro game emulators. As such, they gave the malicious app group “RAINBOWMIX,” in tribute to the “colorful games of years ago.”
And after sharing their findings with Google, the tech giant removed all RAINBOWMIX apps from the Play Store. But in case you downloaded one of them, you better delete it ASAP.
The RAINBOWMIX Sighting
The Satori Threat Intelligence and Research team at cybersecurity firm White Ops recently discovered over 240 malicious apps on the Google Play Store. According to the researchers, these apps are displaying OOC ads to avoid suspension and remain undetected. Many of them are Nintendo (NES) emulators taken from legitimate sources or low-quality games. Even the ads on display seem like they’re coming from trusted sources, such as YouTube or Chrome.
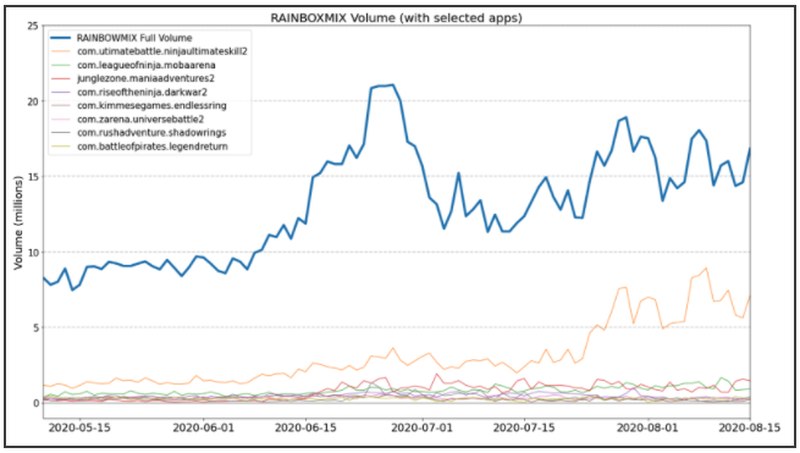
The fraudulent retro games work perfectly well initially, even if at low quality, prompting more than 14 million downloads. However, that helped them remain under the radar. They used packers to avoid Google Play Store’s security protocols and settled there for quite some time. More worrying is that RAINBOWMIX apps produced a total of 15 million ad impressions per day at their peak.
Packer software saves space and masks threats, allowing it to bypass security systems. Once it infiltrates its target, the packer unloads the malicious code, which, in this case, is OOC ads disguised as if they were from a reputable source. As a result, users don’t get suspicious.
“The main tool in the adware developer’s arsenal are the packers. They cloak and allow a threat to exist under the guise of intellectual property protection.”
Gabriel Cirlig, principal threat intelligence analyst for White Ops
RAINBOWMIX apps were also able to determine when users turned their screens on and off to deliver OOC ads at an ideal time. After all, displaying ads when the screen is locked would be quite alarming. According to the team, the RAINBOWMIX campaign has been running since at least 2019. But the apps recorded a significant surge in downloads during the COVID-19 pandemic and the resulting worldwide lockdowns.

RAINBOWMIX and OOC Ads Tricking the System
The research team, which consists of Cirling, Michael Gethers, Lisa Gansky, and Dina Haines, noticed that services and receivers inside the apps’ manifest responded to more triggers than they should. That included system boots, connection changes, plugging/unplugging charging cables, and app installations. The reason behind that is to “confuse analysts and trick static analysis engines.”
Every RAINBOWMIX app contained the service com.timuz.a, leading researchers to believe that the trigger for out-of-context ads resides there. The report explains that com.timuz.a receives orders from a command-and-control (C2), but its URL is hidden under a base64 encoding. Once the C2 connection is established, the service com.ironsource.sdk.handlers.a.a takes over and tries to deliver OOC ads every 10 minutes.
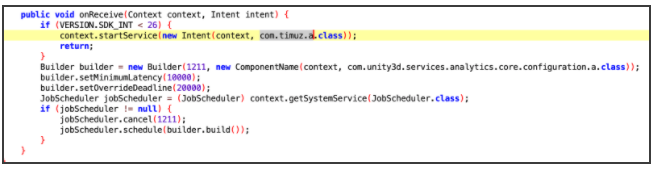

And although the latter service is a trustworthy SDK, it’s likely possible that ironSource is unaware of the abuse.
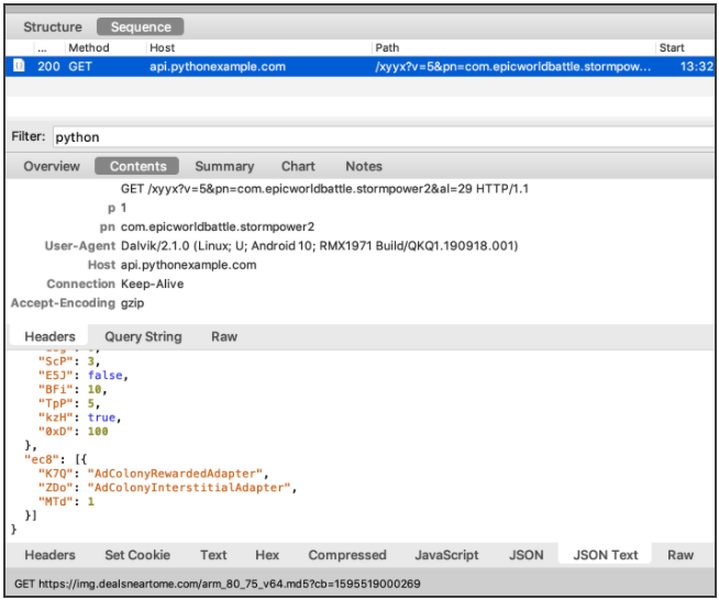
The C2 domain api[.]pythonexample[.]com launched in 2017. However, researchers believe that it is a hacked website that threat actors used to command apps to deliver out-of-context ads. The site hosted an online forum question in 2018, but it was most likely after that as it now defaults to a Ngnix page.
After they installed the app, the White Ops team noticed that a secondary URL is contacted, and a JSON payload is downloaded:
hxxp://api[.]pythonexample[.]com/xyyx?pn=com.androidapk.gbaemulator

Just a few seconds after that, the device displayed an out-of-context ad, with a small icon indicating that the user is receiving data from a different app than the one they’re running.


Do You Have a RAINBOWMIX App? Here’s What You Should Do
You don’t have to worry about unknowingly downloading a RAINBOWMIX app from now on because Google Play Store removed all of them. But if you already installed one of them on your device, we recommend you delete it as soon as possible. In case you’re not sure whether you downloaded a RAINBOWMIX app, check out the full list of fraudulent apps at the end of the White Ops report.
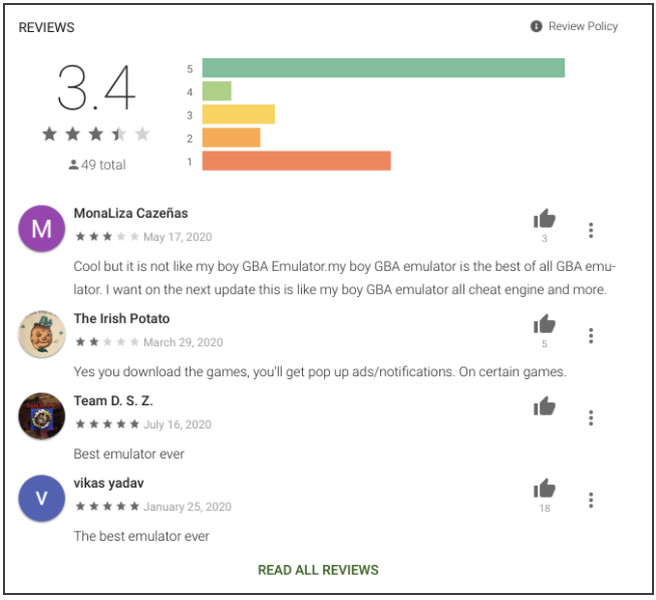
You can look for other signs as well if you don’t feel like searching among 240 apps. For instance, you can read what users had to say about the RAINBOWMIX apps on the Google Play Store. Researchers say that most malicious apps mainly earn 1 to 5-star reviews. In one example, the APK GBA Emulator app, most comments were negative and indicated that the app is barely functional. Many users also reported out-of-context ads.

But no matter which application you download, always take time to read reviews and data-access permissions. Furthermore, try to avoid app stores or sources outside the realm of Google Play Store or Apple’s App Store. In a statement to Forbes, Google said that it had previously detected most of the RAINBOWMIX apps. It also commended White Ops for sharing their findings, which the company confirmed.
“When we find policy violations, we take action and Google continues to make significant investments to protect our users and their experiences.”
Google
RAINBOWMIX, OOC Ads Damages
The White Ops report highlighted that OOC ads could have damaging effects on legitimate and reputable advertisers relying on consumer trust. Chrome, YouTube, and other trustworthy services would never spam consumers, but they could now be mistaken as out-of-context ads and subsequently dismissed.
Furthermore, the researchers noted that most of the traffic comes from the Americas and Asia. Brazil leads the way with 20.8%, while Indonesia isn’t too far behind with 19.7%. Vietnam came in third with 11.0% and the US fourth with 7.7%. Mexico (6.2%) and the Philippines (5.9%) made up the rest of the list.



