The Top Five Risks of Torrenting


- Torrenting definition
- P2P file-sharing back on the rise
- Legal usage of torrenting
- Five torrenting risks
- Protect yourself with a top antivirus and VPN
“I would travel down to hell and wrestle a film away from the devil if it was necessary.” That is how legendary German actor and filmmaker Werner Herzog describes how indispensable cinema and television are. An overview of some of the numbers will show you just how big the Entertainment and Media industry really is.
According to PricewaterhouseCoopers (PwC), total US cinema revenue reached $12 billion in 2018, up 7.2% year-on-year. Meanwhile, subscription TV revenue reached $94.6 billion in the same year, while the OTT video market generated $14.5 billion.
In other words, television and cinema are bigger than ever, and they are showing no signs of slowing down. After all, what’s better than watching your favorite movies and series online for free? That’s exactly what torrenting websites like The Pirate Bay and RARBG provide.
Now, even though these services offer convenient and fast solutions for TV lovers, they also come with their share of risks. Viruses, malware, and copyright breaches are just some of the dangers. Therefore, it’s important to protect yourself before you engage in any P2P activity.
Content Overview
- What Is Torrenting?
- Torrenting Back in Favor
- Why You Should Use Torrenting
- Five Torrenting Risks You Should Be Aware of
- How to Protect Yourself When Torrenting
- Conclusion
What Is Torrenting?
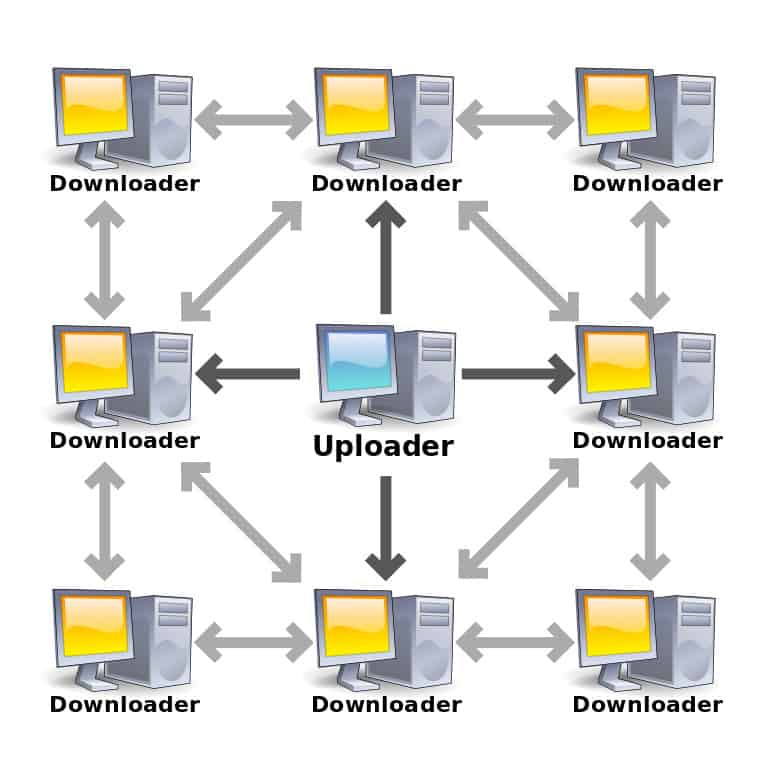
Usually, when you want to download something on the Internet, you just click a link and wait until the file is installed on your device. But did you ever think about how the process works? Well, in traditional downloading, your target exists on a single, centralized server. However, when it comes to torrenting, it’s actually the opposite.
Before I explain to you how torrenting works, it’s better that you familiarize yourself with the following jargon:
- Trackers: Servers and URLs that help in the file transfer process by channeling pieces of small data between uploaders and downloaders.
- Seeders: Users who downloaded a particular file in full. They allow other users who wish to download the file to take bits of data from their computers.
- Leechers: These are the ones who are downloading a specific file. They take bits of data from the seeders who have fully downloaded the file until the download is complete.
- P2P protocol: There is no central server in a P2P (peer-to-peer) network. Instead, each computer system is connected to the other through the Internet, and they can share files directly between them. In other words, each “peer” is a server and a client at the same time.
- Peers: Every member of a P2P (peer-to-peer) file-sharing network. In other words, they are users who are constantly uploading and downloading files.
- Indexers: Torrent websites like The Pirate Bay and RARBG, where you search for the torrent you want, whether it’s a movie, series, or music.
- BitTorrent clients: The software or applications you need to download torrent files.
- Swarms: Peers who download or upload the same torrent files.
How It Works
You see, torrents follow a decentralized method to download/upload files. They break up the data into small pieces that are shared across a network of computers. Therefore, if you want to download the movie Kill Bill, for example, your file isn’t stored on the torrent website’s server.
On the contrary, it’s available on the P2P network, and more specifically, on the seeders’ computers. So you’re actually downloading Kill Bill from other torrent users who have already downloaded the file on their devices. And the more seeders you connect to, the faster your movie will download.
That’s why it’s easier and swifter to target torrents with plenty of seeders and few leechers. Your Internet connection plays a crucial role, as well.

Is Torrenting Back in Favor?
After a decade-long decline, torrenting is once again on the rise. The emergence of affordable streaming platforms like Netflix put a significant dent on P2P file-sharing websites. However, according to Sandvine’s Global Internet Phenomena report, users are shifting back to BitTorrent.
Experts attributed this revival to the exclusivity of streaming deals. Netflix, along with its competitors, offers movies and shows that are only available on their platforms. For example, Game of Thrones was exclusive to HBO Go/HBO Now users, while Hulu has rights for The Handmaid’s Tale.
And while all these services offered budget-friendly access to quality content separately, users aren’t willing to subscribe to all of them. After all, streaming platforms aim to provide cheaper alternatives to cable or satellite subscriptions. So if you have to pay for multiple services to watch your favorite shows, it will cost you almost the same amount.
“To get access to all of these services, it gets very expensive for a consumer, so they subscribe to one or two and pirate the rest.”
Cam Cullen, Vice President of Global Marketing at Sandvine
Furthermore, there’s the whole geo-blocked content issue. For example, HBO Go and HBO Now are only accessible inside the United States, while BBC iPlayer is only available inside the UK. Even services with global outreach like Netflix and Amazon Prime Video offer different libraries according to each region.
As a result, some users prefer to get their TV dosage from a single source that happens to be free as well: Torrent websites.
Why You Should Use Torrenting
Most Internet users believe that torrenting is just for pirating copyrighted materials like movies, series, or songs. But the truth is, it has several practical and legal uses as well.
Video and Music Sharing
Don’t let the DCMA or other copyright protection agencies fool you into thinking that all media torrents are illegal. A lot of emerging artists and cover bands make their music available to the public, and torrenting is a great way to do it.
Most online file storage services cost a lot of money. They usually charge per gigabyte and feature a bandwidth fee as well. Therefore, artists opt for sharing their music or videos via torrenting, which is free for use. They’ll also save money on bandwidth as users will contribute part of their Internet connection each time someone downloads the file.
Moreover, they’ll have a chance of reaching a broader audience and increase their exposure. The bottom line is it’s a win-win situation for artists and users who don’t have to deal with copyright problems. And it’s not just for music or videos.
Torrents are responsible for chopping up data into little pieces and distributing them over the P2P network. Such files include operating system installations, photo galleries, and any other large-sized documents.
Syncing Files
Looking to synchronize your files between computers? Well, you won’t find a more secure way than with torrenting. That’s because BitTorrent Sync does not store your data on a single server. Instead, it shares and saves it on any other computer that has the secret passcode.
The thing is every device you share your file with must have the BitTorrent Sync software installed. Also, you must turn on your computer at all times so that other users can sync the data on their computers. And since there is no centralized server, you don’t have to abide by the storage space of third-party services like Dropbox or Google Drive.
Gaming Downloads and Updates
Blizzard Entertainment, the company behind popular video games World of Warcraft, Diablo III, and Starcraft, uses a BitTorrent client for updates and downloads. The Video Game developer will send you a torrent client when you purchase one of its games so that you can download it.
Moreover, the torrent client will automatically download game updates once they’re available. Blizzard uses BitTorrent to reduce bandwidth costs and offer the fastest download speeds possible.
Five Torrenting Risks You Should be Aware of
While torrenting has a lot of advantages and gives you access to several files, there is also a dark side to it. The most obvious one is the illegal acquisition of copyrighted material. But there’s also a risk of malware infestation and Internet throttling.
Viruses and Malware
As I mentioned earlier, whenever you download a certain file using BitTorrent, you’re getting it from every seeder in the P2P network. In other words, the source is unknown. Cybercriminals can take advantage of that and embed a virus in the file.
As a result, they’ll have access to your device and every bit of data you have on it. That includes passwords, financial details, emails, and a host of other sensitive information. And some viruses can replicate and infect other files you might have without even your knowledge.
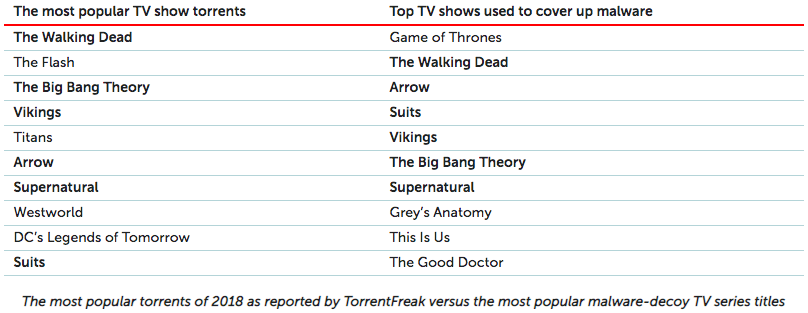
A 2019 Kaspersky Labs research showed that hackers were using popular TV shows torrents to infect users with malicious software. Game of Thrones topped the list of files that contain viruses, while The Walking Dead, Arrow, Suits, and Vikings also featured.

Therefore, you should always download a file that has a lot of seeders and good reviews from users. Besides, most indexers have a comment section for each torrent, where people can warn others if a file is contaminated with a virus.
Furthermore, the best precautionary course action against such threats is getting an elite antivirus program. These may cost you a bit of money, but they are capable of blocking potential risks and warning you about them. And it’s better if they feature a built-in firewall.
Adware
Every Internet user comes across adware. It’s those annoying ads that are on display whenever you visit a website, while some of them come in the form of pop-ups. But in both cases, they ruin your browsing experience, sometimes even preventing you from viewing the entire content that you want.
Although adware isn’t as dangerous as other online threats, it can affect your computer’s performance. Advertising-supportive software uses your PC resources to run, which slows it down and causes system instability. Moreover, they operate in stealth mode, meaning there are no signs that they in your device.
Developers can offer adware by hiding it in the movies, series, and music you download using BitTorrent. For example, an episode of the popular TV show Family Guy contained several pieces of known adware and spyware. Industry experts suspect that online marketers have launched campaigns to install their programs on more PCs with BitTorrent.
And while the damage that adware causes is minimal, mixing it with spyware can have much more dangerous effects.
Spyware
Just like adware, spyware crawls into your system and operates without your knowledge or consent. And as the name suggests, this form of malicious software will spy on you, meaning it will collect sensitive data. That includes your browsing history, web destinations, and IP address.
And since spyware and adware are like two peas in a pod, hackers can use such information to deliver targeted ads. That’s the least of your problems, however. Cybercriminals can also monitor your login details (username and passwords), banking information, and any other keystroke collection.
As a result, they can empty your bank account and wreak havoc under your name. Hackers will most likely include such malicious programs in software torrents. They will crack a legit, paid software, modify it, and make it available for free on torrent websites.
That will tempt users to download the free software, along with the spyware that comes with it. Therefore, as I previously mentioned, make sure you read the review about any file you wish to get on BitTorrent.
ISP Throttling
Online security and privacy are some of the most common issues associated with torrenting. Another problem that most users aren’t aware of is ISP throttling. That’s right; your Internet service provider can determine if you’re using a P2P protocol to download files.
And it may decide to limit your Internet speed if you consume too much bandwidth. As a result, the download process will slow down or drop altogether. And it’s not just with torrenting. Your ISP throttles your Internet speed when you watch too much Netflix or YouTube.
And in some countries where torrenting is illegal, Internet service providers will ban the most popular websites. Even if you somehow manage to access a site that isn’t blocked yet, your ISP can monitor your online activities and bandwidth. So it’s just a matter of time before the website becomes inaccessible.
Furthermore, your ISP might punish you for breaking its terms by reducing your bandwidth or speed or even terminating your connection.
Legal Issues
Even though there are several legal uses for torrenting, users mostly engage in P2P file-sharing activities to illegally download copyrighted materials. From movies and TV shows to music and video games, copyright trolls are always lurking online, looking for anyone who violates digital media laws.
As I previously mentioned, your Internet service provider can easily identify torrenting activities. And whenever you go online, you use an IP address that your ISP provides. Therefore, the latter will receive a warning letter from copyright holders or studios notifying them of their illegal actions.
Your ISP will transfer this warning to you by tracking you down using your IP address and connection timestamp. Your punishment will vary from a slap on the wrist to service termination, depending on how many times you engage in torrenting. Usually, it’s strike three, and you’re out.
Copyright trolls might resort to more cunning ways by posing as a seeder or peer. They will upload the file they are trying to protect on torrent websites, then track anyone who downloads it. That’s quite easy to execute as torrenting uses a peer-to-peer network to upload/download files.
And since torrenting shares your information and IP address with other peers, copyright trolls and ISPs will have no problem identifying you.
Legal Actions
Countries that criminalize torrenting and other forms of online piracy may inflict severe punishments on users. In the US, violators can end up paying more than $150,000, as in the case of RIAA vs. Thomas-Rasset. In Canada, meanwhile, fines could reach a maximum of $5,000. If you ignore the legal notices and penalties, the next step will be a “lien on your house” or a “garnishment of your salary.”
“They can get a default judgment, and they can go for the maximum, which is $5,000”
David Fraser, Privacy Lawyer at McInnes Cooper
According to legal analytics company Lex Machina, over 1,000 lawsuits were filed against BitTorrent pirates in the United States in 2019. While that number may seem insignificant when you consider the number of users, it is a major, escalating step against torrent users.
And even though it is extremely rare, you can get some serious jail time if you continue to download copyrighted material with BitTorrent.
How to Cover Your Back When Torrenting
Well, it seems that you have three types of concerns whenever you download torrent files: Malware, throttling, and legal issues. To avoid these problems, all you need to do is get a trustworthy antivirus program and a reputable VPN service.
Antivirus Programs
To stay safe from the dangers of viruses, malware, adware, spyware, or any other malicious software, you need a premium antivirus program. Top brands may be a bit pricey, but they can detect and eliminate any online threat that tries to find its way to your computer.
Moreover, they have active protection while you’re using the Internet, and perform automatic scans to your files and programs. Most of them also come with cleanup tools that clear out unused applications and programs. As a result, your device’s performance will improve, becoming faster and smoother.
These top antiviruses also update automatically without bothering you with manual steps. Updates are extremely important for such programs as it allows them to identify new forms of malware so that they can prevent it. Moreover, they feature built-in firewalls, meaning you don’t have to install third-party services.
Most high-end antiviruses allow you to execute programs in the “Sandbox.” The latter is an isolated environment where you can run files and applications without affecting the system.
There are a lot of antivirus programs on the market, including well-known brands like McAfee or Norton. You can also opt for Bullguard, TotalAV, or Bitdefender. But most importantly, try to avoid free brands as they may monitor, collect, and share your data.
Virtual Private Networks (VPNs)
You can fix throttling and legal issues with a premium VPN service. Virtual private networks hide your actual IP address and give you a different one from almost any region in the world. You just have to connect to one of its many servers, and you’ll get an IP that matches the VPN server location.
Therefore, the torrent swarm won’t be able to see your actual IP address. Instead, the IP address of the VPN server you’re connected to will be on display, which means that no one can track your location and trace anything back to you.
But why is it so important to hide your IP address? Because ISPs and copyright trolls use it to track your online identity and location. Therefore, when you go online, they will think you are elsewhere. Moreover, VPNs use top-level encryption to encrypt your traffic and data. As a result, no one can monitor your online activities and trace back to you. That includes your ISP, P2P network, copyright holders, hackers, and government agencies.
However, Internet service providers can figure out if you’re using a VPN. Each country has a set of dedicated IP addresses, so when you use a foreign one, your ISP will find out that it did not provide you with it. But it can’t determine why you’re using a VPN.
That is why virtual private networks can fix Internet throttling. Your ISP won’t know what you’re doing online, including torrenting or streaming. Not all VPNs can do that, though. Only elite services have such efficiency, which means you must never consider a free brand.
ExpressVPN


The VPN industry is packed with VPN providers, many of which label themselves as the best. Yet, few can match what ExpressVPN offers. That includes the military-grade Advanced Encryption Standard with 256-bit keys (AES-256). This encryption has never been breached before, and it is the same one that governments use to protect classified information.
You’ll also benefit from a no-logs policy, which means that ExpressVPN won’t collect or share any records of your online activities or connection. The company also allows P2P file-sharing, but at your own expense. And if you’re dissatisfied with the service, you can get a refund, thanks to the 30-day money-back guarantee.
Pros
- AES 256-bit encryption.
- No-logs policy.
- A kill switch.
- DNS Leak protection.
- Torrenting and P2P allowance.
- 3,000+ servers in 94 countries (according to the website).
- Support for Netflix and streaming.
- Top speed rates.
- Outside data-retention-law jurisdiction.
- Smart DNS proxy: MediaStreamer.
- Ready-made apps for iOS, Mac, Windows, Android, Linux, and Kindle Fire.
- Five concurrent device connections.
- 24/7 customer support.
- 30-day money-back guarantee.
Cons
- Expensive subscription plans.
BulletVPN


BulletVPN is another ideal choice for torrenting and P2P file-sharing. First of all, it doesn’t block torrent-related websites, and second, it uses the same top-level encryption as ExpressVPN. There are other similarities, like a zero-logs policy, Netflix support, high device compatibility, and top levels of speed.
The company also offers a kill switch that cuts off your Internet connection in case the VPN stops working. As a result, your data won’t leak to your ISP’s servers. And with BulletShield, you won’t be able to connect to the Internet unless you use a BulletVPN server.
Pros
- Military-grade encryption (AES 256-bit).
- Torrenting and P2P support.
- Zero-logs policy.
- A kill switch + Bulletshield feature.
- Fast speed rates.
- Unlimited bandwidth.
- 24/7 customer support.
- High-compatibility with major operating systems.
- Works with Netflix.
- Support for five VPN protocols.
- 30-day money-back guarantee.
- Six simultaneous device connections per account.
Cons
- Smaller server network (75+ servers in 41+ countries).
There is one thing you should note, though. Technically speaking, you may still receive a warning letter even if you’re using certain VPNs. Copyright trolls can determine that you’re using a VPN IP address and send a complaint to the respective virtual private server (VPS).
The latter will contact your VPN provider, who will check the timestamp of the downloaded file and see which users were connected to the appropriate server at that time. Your VPN will then notify you of the warning, but without revealing your identity to copyright holders.
Also, please note that top VPNs do not keep records of your actual or VPN IP address. Therefore, your identity is always protected.
Read User Comments and Reviews
Torrent websites, aka indexers, usually feature a comment section for each torrent so that users can rate them. Make sure you read what other seeders had to say about the file you seek to download as they will warn you against any potential viruses.
Also, you should always download a file that has a lot of seeders and good reviews. One, you can ensure that the torrent is clean from any malware; and two, the file will download much faster that way as it is distributed over several peers.
Five Risks of Torrenting – Final Thoughts
As opposed to what many users believe, torrenting has legal usage. Not all files have copyrights, which means anyone can download them. Furthermore, you can use BitTorrent to synchronize files and download or update video games. But the most common torrent practice is the download of copyrighted movies, shows, and music.
A lot of risks accompany torrent files, some of which can infect your device and compromise your data, while others can get you in trouble with the law. Therefore, stay on the safe side and get reputable antivirus programs and VPN services before you start sharing files.
Have you ever been in trouble for torrenting? Share your experience in the comment section below.



